Applying an Attack Defense Policy
Context
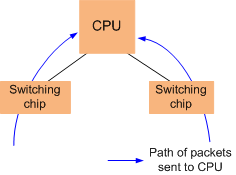
Packets sent to the CPU pass through the switching chip before they reach the CPU, as shown in Figure 1. Therefore, an attack defense policy is usually applied to the switching chip of a switch by specifying the global keyword.
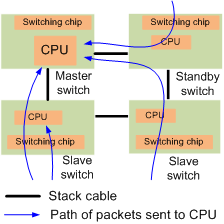
In a stack system shown in Figure 2, applying an attack defense policy to the CPU of the master switch by not specifying the global keyword. If you only limit packet rates on switching chips of member switches, the CPU of the master switch may still be overloaded by a large number of protocol packets, because most protocol packets need to be sent to the CPU of the master switch after being processed by the CPU of the standby switch or a slave switch. Applying an attack defense policy to the CPU of the master switch can limit the rates of protocol packets sent to this CPU, protecting the CPU from attacks.
Procedure
- Apply an attack defense policy to the CPU.
- Run the system-view command to enter the system view.
- Run the cpu-defend-policy policy-name1 command to apply an attack defense policy.

Only the stack-capable models support this command.
In a stack system, some protocol packets are not sent to the CPU of the master switch. If you apply an attack defense policy against such protocol packets to the CPU, the system displays an error message, indicating that the policy cannot be applied.
Only the attack defense policies that limit the rates of packets sent to the CPU can be applied to the CPU. Other types of attack defense policies are not applicable to the CPU, so configuring such policies cannot protect the CPU.
- Apply an attack defense policy to the switching chip.
- Run the system-view command to enter the system view.
- Run the cpu-defend-policy policy-name2 global command to apply an attack defense policy.