Example for Configuring Local Attack Defense
Networking Requirements
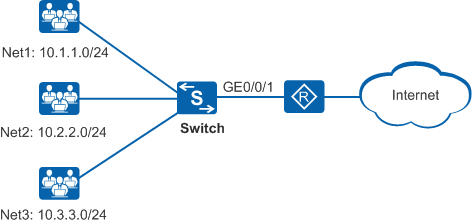
As shown in Figure 1, users on different network segments access the Internet through the Switch. Because a large number of users connect to the Switch, the Switch's CPU will receive a lot of protocol packets. If attackers send a lot of malicious attack packets to the Switch, CPU usage will increase to affect services. The network administrator has the following requirements:
- The network administrator wants to monitor CPU status. When the CPU is attacked, the Switch can promptly notify the administrator and take measures to protect the CPU.
- When the Switch receives a lot of ARP Request packets, the CPU usage of the Switch greatly increases. The administrator wants to reduce CPU usage to avoid impacting services.
- Users on Net1 often initiate attacks, so the administrator wants to reject access by Net1 users. Net2 users are fixed authorized users.
- The administrator wants to upload files to the Switch through FTP, so data transmission between the administrator's computer and the Switch must be reliable and stable.
Configuration Roadmap
The configuration roadmap is as follows:
- Configure attack source tracing, alarms, and punish function so that the device can send an alarm to the administrator when detecting an attack source and automatically take punish actions.
- Add Net2 users to the whitelist to exclude them from attack source tracing analysis and punishment.
- Set the protocol rate threshold so that the Switch can limit the rate of protocol packets based on ports and record a log. (Port attack defense is enabled by default, so it does not need to be enabled again.)
- Set the CPCAR for ARP Request packets to limit the rate of ARP Request packets sent to the CPU. This reduces the impact of ARP Request packets on the CPU.
- Add Net1 users to the blacklist to reject their access.
- Set the rate limit for the FTP packets sent to the CPU to ensure reliability and stability of data transmission between the administrator's computer and the Switch. (ALP is enabled for FTP by default, so it does not need to be enabled again.)
Procedure
- Configure the rule for filtering packets sent to the CPU.
# Define ACL rules.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] acl number 2001 [Switch-acl-basic-2001] rule permit source 10.1.1.0 0.0.0.255 [Switch-acl-basic-2001] quit [Switch] acl number 2002 [Switch-acl-basic-2002] rule permit source 10.2.2.0 0.0.0.255 [Switch-acl-basic-2002] quit
- Configure an attack defense policy.
# Create an attack defense policy.
[Switch] cpu-defend policy policy1
# Configure attack source tracing.
[Switch-cpu-defend-policy-policy1] auto-defend enable
# Enable the alarm function for attack source tracing.
[Switch-cpu-defend-policy-policy1] auto-defend alarm enable
# Configure a whitelist for attack source tracing.

Add the IP addresses of valid servers, interconnected interfaces, and IP address of network management device to the whitelist.
[Switch-cpu-defend-policy-policy1] auto-defend whitelist 1 acl 2002
# Set the punish action to discard.
Before configuring the punish action, ensure that the device is undergoing an attack; otherwise, the punish action may discard a lot of valid protocol packets.
[Switch-cpu-defend-policy-policy1] auto-defend action deny
# Set the rate threshold to 40 pps. (Port attack defense is enabled by default, so it does not need to be enabled again.)[Switch-cpu-defend-policy-policy1] auto-port-defend protocol arp-request threshold 40
# Add the network-side interface GE0/0/1 to the whitelist so that the CPU can promptly process the packets from the network-side interface.[Switch-cpu-defend-policy-policy1] auto-port-defend whitelist 1 interface gigabitethernet 0/0/1
# Set the CPCAR of ARP Request packets to 120 kbit/s.
[Switch-cpu-defend-policy-policy1] car packet-type arp-request cir 120 Warning: Improper parameter settings may affect stable operating of the system. Use this command under assistance of Huawei engineers. Continue? [Y/N]:y
# Configure the blacklist for CPU attack defense.
[Switch-cpu-defend-policy-policy1] blacklist 1 acl 2001
# Set the CIR of FTP packets sent to the CPU to 5000 kbit/s.[Switch-cpu-defend-policy-policy1] linkup-car packet-type ftp cir 5000 [Switch-cpu-defend-policy-policy1] quit
- Apply the attack defense policy globally.
[Switch] cpu-defend-policy policy1 global [Switch] quit
- Verify the configuration.
# Display the configuration of attack source tracing.
<Switch> display auto-defend configuration ---------------------------------------------------------------------------- Name : policy1 Related slot : <0> auto-defend : enable auto-defend attack-packet sample : 5 auto-defend threshold : 60 (pps) auto-defend alarm : enable auto-defend trace-type : source-mac source-ip auto-defend protocol : arp icmp dhcp igmp tcp telnet 8021x auto-defend action : deny (Expired time : 300 s) auto-defend whitelist 1 : acl number 2002 ----------------------------------------------------------------------------# Display the configuration of port attack defense.
<Switch> display auto-port-defend configuration ---------------------------------------------------------------------------- Name : policy1 Related slot : <0> Auto-port-defend : enable Auto-port-defend sample : 5 Auto-port-defend aging-time : 300 second(s) Auto-port-defend arp-request threshold : 40 pps(enable) Auto-port-defend arp-reply threshold : 30 pps(enable) Auto-port-defend dhcp threshold : 30 pps(enable) Auto-port-defend icmp threshold : 30 pps(enable) Auto-port-defend igmp threshold : 60 pps(enable) Auto-port-defend ip-fragment threshold : 30 pps(enable) Auto-port-defend alarm : disable ----------------------------------------------------------------------------
# Display the configuration of the attack defense policy.<Switch> display cpu-defend policy policy1 Related slot : <0> Configuration : Blacklist 1 ACL number : 2001 Car packet-type arp-request : CIR(120) CBS(22560) Linkup-car packet-type ftp : CIR(5000) CBS(940000)
# Display the CPCAR setting.<Switch> display cpu-defend configuration packet-type arp-request slot 0 Car configurations on slot 0. ---------------------------------------------------------------------- Packet Name Status Cir(Kbps) Cbs(Byte) Queue Port-Type ---------------------------------------------------------------------- arp-request Enabled 120 22560 3 UNI ----------------------------------------------------------------------
Configuration Files
Switch configuration file
#
sysname Switch
#
acl number 2001
rule 5 permit source 10.1.1.0 0.0.0.255
acl number 2002
rule 5 permit source 10.2.2.0 0.0.0.255
#
cpu-defend policy policy1
blacklist 1 acl 2001
car packet-type arp-request cir 120 cbs 22560
linkup-car packet-type ftp cir 5000 cbs 940000
auto-defend alarm enable
auto-defend action deny
auto-defend whitelist 1 acl 2002
auto-port-defend protocol arp-request threshold 40
auto-port-defend whitelist 1 interface GigabitEthernet0/0/1
#
cpu-defend-policy policy1 global
#
return