Example for Configuring PPPoE+
Networking Requirements
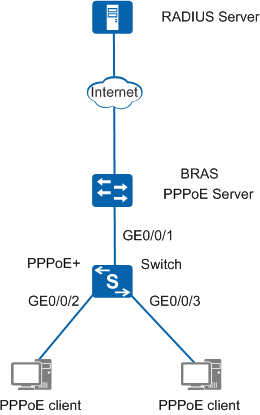
As shown in Figure 1, the Switch is connected to an upstream BRAS and a downstream PPPoE client. The BRAS functions as a PPPoE server. On networks, unauthorized users listen to PPPoE packets of authorized users and even embezzle accounts of authorized users. The administrator wants to prevent these problems and ensure user account security.
Configuration Roadmap
The configuration roadmap is as follows:
Enable PPPoE+ globally to authenticate the user account and access interface information, preventing the user account from embezzling.
Configure the interface connecting the Switch and the PPPoE server as a trusted interface, preventing PPPoE packets from being listened by unauthorized users when the packets are forwarded to non-PPPoE service port.
Configure the policy for processing user-side PPPoE packets on the Switch, enabling the Switch to properly communicate with the PPPoE server.
Procedure
- Enable PPPoE+.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] pppoe intermediate-agent information enable

After PPPoE+ is enabled globally, PPPoE+ is enabled on all the interfaces.
- Configure the GE0/0/1 interface
as a trusted interface.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] pppoe uplink-port trusted [Switch-GigabitEthernet0/0/1] quit
- Set the policy for processing original fields in user-side
PPPoE packets to replace on all interfaces, and replace original
fields in PPPoE packets with the circuit ID and remote ID of the Switch.
[Switch] pppoe intermediate-agent information policy replace
- Set the format of circuit-id to extend.
[Switch] pppoe intermediate-agent information format circuit-id extend
- Verify the configuration.
# Run the display pppoe intermediate-agent information policy command to verify the policy for processing original fields in user-side packets.
[Switch] display pppoe intermediate-agent information policy The current information Policy :REPLACE The current ignore-reply Policy:ENABLE
# Run the display pppoe intermediate-agent information format to verify the format of circuit-id.[Switch] display pppoe intermediate-agent information format The current information format : Circuit ID : EXTEND Remote ID : COMMON For example: interface GigabitEthernet0/0/1 SVLAN:200 CVLAN:100 The PPPOE Intermediate Agent information follow: Circuit ID:00 04 00 c8 00 00 Remote ID:0025-9efb-494a