Example for Configuring Domain-based User Management
Networking Requirements
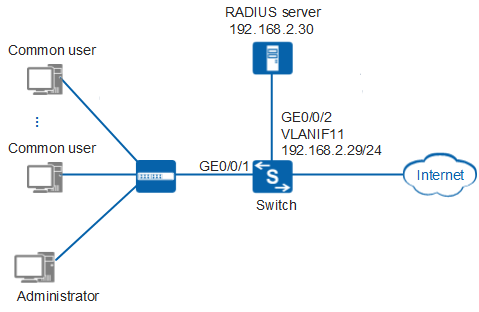
As shown in Figure 1, enterprise users access the network through Switch. The user names do not contain any domain names.
The enterprise requires that common users access the network and obtain rights after passing RADIUS authentication and that administrators log in to the device for management only after passing local authentication on Switch.
Configuration Roadmap
The configuration roadmap is as follows:
- Create a VLAN and a VLANIF interface for Switch to communicate with the RADIUS server.
- Configure authentication and accounting schemes for common users and apply the schemes to the default domain to authenticate common users, such as users using 802.1X or Portal authentication. The user names of the users do not contain domain names.
- Configure authentication and authorization schemes for administrators and apply the schemes to the default_admin domain to authenticate administrators, such as a user logging in through Telnet, SSH, or FTP. The user names of administrators do not contain domain names.

Ensure that users have been configured on the RADIUS server. In this example, the user with the user name test1 and password 123456 has been configured on the RADIUS server.
This example provides only the configuration for Switch. The configurations of the RADIUS server are not described here.
Procedure
- Create a VLAN and configure interfaces.
# Create VLAN 11 on Switch.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 11
# Set the link type of GE0/0/2 of Switch that is connected to the RADIUS server to access, and add GE0/0/2 to VLAN 11.
[Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access [Switch-GigabitEthernet0/0/2] port default vlan 11 [Switch-GigabitEthernet0/0/2] quit
# Create VLANIF 11, and configure the IP address of 192.168.2.29/24 for VLANIF 11.
[Switch] interface vlanif 11 [Switch-Vlanif11] ip address 192.168.2.29 24 [Switch-Vlanif11] quit
- Configure RADIUS AAA for common users who use 802.1X authentication.

Ensure that the shared key in the RADIUS server template is the same as that set on the RADIUS server.
# Configure a RADIUS server template named rd1.
[Switch] radius-server template rd1 [Switch-radius-rd1] radius-server authentication 192.168.2.30 1812 [Switch-radius-rd1] radius-server accounting 192.168.2.30 1813 [Switch-radius-rd1] radius-server shared-key cipher Huawei@2012 [Switch-radius-rd1] radius-server retransmit 2 [Switch-radius-rd1] quit
# Create authentication and accounting schemes both named abc, and set the authentication and accounting modes to RADIUS.
[Switch] aaa [Switch-aaa] authentication-scheme abc [Switch-aaa-authen-abc] authentication-mode radius [Switch-aaa-authen-abc] quit [Switch-aaa] accounting-scheme abc [Switch-aaa-accounting-abc] accounting-mode radius [Switch-aaa-accounting-abc] quit
# Test connectivity between Switch and the RADIUS server. Ensure that the test1 user with the password 123456 has been configured on the RADIUS server.
[Switch-aaa] test-aaa test1 123456 radius-template rd1# Apply the authentication scheme abc, accounting schemes abc, and RADIUS server template rd1 to the default domain.
[Switch-aaa] domain default [Switch-aaa-domain-default] authentication-scheme abc [Switch-aaa-domain-default] accounting-scheme abc [Switch-aaa-domain-default] radius-server rd1 [Switch-aaa-domain-default] quit [Switch-aaa] quit
# Set the NAC mode to unified
[Switch] authentication unified-mode After the common mode is changed to unified mode, the device automatically restarts. By default, the unified mode is used.
After the common mode is changed to unified mode, the device automatically restarts. By default, the unified mode is used.# Enable 802.1X authentication on GE2/0/0.
[Switch] dot1x-access-profile name d1 [Switch-dot1x-access-profile-d1] quit [Switch] authentication-profile name p1 [Switch-authen-profile-p1] dot1x-access-profile d1 [Switch-authen-profile-p1] authentication mode multi-authen max-user 100 [Switch-authen-profile-p1] quit [Switch] vlan batch 10 [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type access [Switch-GigabitEthernet0/0/1] port default vlan 10 [Switch-GigabitEthernet0/0/1] authentication-profile p1 [Switch-GigabitEthernet0/0/1] quit
# Set the global default domain for common users to default. After common users enter their user names in the format of user@default, the device performs AAA authentication for the users in the default domain. If a user name does not contain a domain name or contains a non-existing domain name, the device authenticates the common user in the default domain for common users.
[Switch] domain default - Configure local authentication and authorization for the
administrator test.
# Configure the device to use AAA for the Telnet user that logs in through the VTY user interface.
[Switch] telnet server enable [Switch] user-interface vty 0 14 [Switch-ui-vty0-14] authentication-mode aaa [Switch-ui-vty0-14] protocol inbound telnet [Switch-ui-vty0-14] quit
# Configure a local user named test with password admin@12345, and set the user level to 3.
[Switch] aaa [Switch-aaa] local-user test password irreversible-cipher admin@12345 privilege level 3
# Set the access type of test to Telnet.
[Switch-aaa] local-user test service-type telnet# Configure local account locking. Set the retry interval to 5 minutes, the maximum number of consecutive authentication failures to 3, and the local account locking duration to 5 minutes.
[Switch-aaa] local-aaa-user wrong-password retry-interval 5 retry-time 3 block-time 5# Create an authentication scheme named auth, and configure the authentication scheme to use local authentication.
[Switch-aaa] authentication-scheme auth [Switch-aaa-authen-auth] authentication-mode local [Switch-aaa-authen-auth] quit
# Create an authorization scheme named autho, and configure the authorization scheme to use local authorization.
[Switch-aaa] authorization-scheme autho [Switch-aaa-author-autho] authorization-mode local [Switch-aaa-author-autho] quit
# Apply the authentication scheme auth and authorization scheme autho to the default_admin domain.
[Switch-aaa] domain default_admin [Switch-aaa-domain-default_admin] authentication-scheme auth [Switch-aaa-domain-default_admin] authorization-scheme autho [Switch-aaa-domain-default_admin] quit [Switch-aaa] quit
# Set the global default domain for administrators to default_admin. After administrators enter user names in the format of user@default_admin, the device performs AAA authentication for the administrators in the default_admin domain. If the user name of an administrator does not contain a domain name or contains a non-existing domain name, the device authenticates the administrator in the default domain for administrators.
[Switch] domain default_admin admin [Switch] quit
- Verify the configuration.
# Run the display dot1x interface command on Switch to verify the 802.1X authentication configuration.
# If you log in as a common user, enter the user name test1 and password 123456 on an 802.1X client, and run the display access-user domain and display access-user user-id commands to check the domain to which you belong and your access type.
<Switch> display access-user domain default ------------------------------------------------------------------------------ UserID Username IP address MAC Status ------------------------------------------------------------------------------ 16040 test1 - 00e0-4c97-31f6 Success ------------------------------------------------------------------------------ Total: 1, printed: 1
<Switch> display access-user user-id 16040 Basic: User id : 16040 User name : test1 Domain-name : default User MAC : 00e0-4c97-31f6 User IP address : - User IPv6 address : - User access time : 2009/02/15 19:10:52 User accounting session ID : huawei255255000000000f****2016040 Option82 information : - User access type : 802.1x AAA: User authentication type : 802.1x authentication Current authentication method : RADIUS Current authorization method : - Current accounting method : RADIUS
# If you log in through Telnet, enter the user name test and password admin@12345, and run the display access-user domain and display access-user user-id commands to check the domain to which you belong and your access type.
<Switch> display access-user domain default_admin ------------------------------------------------------------------------------ UserID Username IP address MAC Status ------------------------------------------------------------------------------ 16009 test 10.135.18.217 - Success ------------------------------------------------------------------------------ Total: 1, printed: 1
<Switch> display access-user user-id 16009 Basic: User id : 16009 User name : test Domain-name : default_admin User MAC : - User IP address : 10.135.18.217 User IPv6 address : - User access time : 2009/02/15 05:10:52 User accounting session ID : huawei255255000000000f****2016009 Option82 information : - User access type : Telnet AAA: User authentication type : Administrator authentication Current authentication method : Local Current authorization method : Local Current accounting method : None
Configuration File
Switch configuration file
# sysname Switch # vlan batch 10 to 11 # telnet server enable # authentication-profile name p1 dot1x-access-profile d1 authentication mode multi-authen max-user 100 # radius-server template rd1 radius-server shared-key cipher %^%#Q75cNQ6IF(e#L4WMxP~%^7'u17,]D87GO{"[o]`D%^%# radius-server authentication 192.168.2.30 1812 weight 80 radius-server accounting 192.168.2.30 1813 weight 80 radius-server retransmit 2 # aaa authentication-scheme abc authentication-mode radius authentication-scheme auth authorization-scheme autho accounting-scheme abc accounting-mode radius domain default authentication-scheme abc accounting-scheme abc radius-server rd1 domain default_admin authentication-scheme auth authorization-scheme autho local-user test password irreversible-cipher $1a$|^<)!}4$IN$9BrKBRY#L:pEc{P#HQ=OI#p["6tY%94gGg2#@FzP$ local-user test privilege level 3 local-user test service-type telnet # interface Vlanif11 ip address 192.168.2.29 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type access port default vlan 10 authentication-profile p1 # interface GigabitEthernet0/0/2 port link-type access port default vlan 11 # user-interface vty 0 14 authentication-mode aaa protocol inbound telnet # dot1x-access-profile name d1 # return