Authorization Scheme
An authorization scheme is used to define methods for user authorization and the order in which authorization methods take effect. An authorization scheme is applied to a domain. It is combined with the authentication scheme, accounting scheme, and server template in the domain for user authentication, authorization, and accounting.
Authorization Methods Supported by a Device
- HWTACACS authorization: An HWTACACS server is used to authorize users.
- Local authorization: The device functions as an authorization server to authorize users based on user information configured on the device.
- Non-authorization: Authenticated users have unrestricted access rights on a network.
- if-authenticated authorization: If passing authentication, a user passes authorization; otherwise, the user fails authorization. This mode applies to scenarios where users must be authenticated and the authentication process can be separated from the authorization process.

RADIUS authentication is combined with authorization and cannot be separated. If authentication succeeds, authorization also succeeds. When RADIUS authentication is used, you do not need to configure an authorization scheme.
In addition, the "authentication + rights level" method is typically used to control access of the administrators (login users) to the device, improving the device operation security. Authentication restricts the administrators' access to the device and the rights level defines commands that the administrators can enter after logging in to the device. For details about the method, see CLI Login Configuration in S2720, S5700, and S6700 V200R019C10 CLI-based configuration - Basic Configuration Guide.
Order in Which Authorization Methods Take Effect
An authorization scheme enables you to designate one or more authorization methods to be used for authorization, thus ensuring a backup system for authorization in case the initial method does not respond. The first method listed in the scheme is used to authorize users; if that method does not respond, the next authorization method in the authentication scheme is selected. If the initial method responds with an authorization failure message, the AAA server refuses to provide services for the user. In this case, authorization ends and the next listed method is not used.
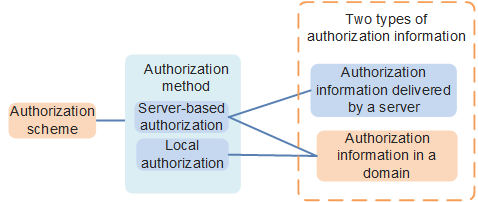
Authorization Information
- If local authorization is used, the user obtains authorization information from the domain.
- If server-based authorization is used, the user obtains authorization information from the server or domain. Authorization information configured in a domain has lower priority than that delivered by a server. If the two types of authorization information conflicts, authorization information delivered by the server takes effect. If no conflict occurs, the two types of authorization information take effect simultaneously. In this manner, you can increase authorization flexibly by means of domain management, regardless of the authorization attributes provided by the AAA server.
Table 1 shows authorization information typically used by a server. Table 2 shows authorization information that can be configured in a domain.
Authorization Information |
Description |
|---|---|
| ACL number | Is delivered by the server. You need to configure ACL number-related rules on the NAS. |
| ACL rule | Is directly delivered by the server. As defined in the rule, users can access all network resources included in the ACL. You do not need to configure the corresponding ACL on the NAS. |
| VLAN | If dynamic VLAN delivery is configured on the server, authorization information sent to the NAS includes the VLAN attribute. After the NAS receives the authorization information, it changes the VLAN to which the user belongs to the delivered VLAN. The delivered VLAN does not change or affect the interface configuration. The delivered VLAN, however, takes precedence over the user-configured VLAN. That is, the delivered VLAN takes effect after the authentication succeeds, and the user-configured VLAN takes effect after the user goes offline. |
| User group/UCL group | The server delivers the user group name, UCL group name, or UCL group ID to the NAS. You need to configure the corresponding group and network resources in the group on the NAS. |
| CAR | The server delivers authorization to control the committed information rate (CIR), peak information rate (PIR), committed burst size (CBS), and peak burst size (PBS) for access between the user and NAS. |
| Administrator level | Priority of an administrator (such as a Telnet user) delivered by the server. The priority ranges from 0 to 15. The value greater than or equal to 16 is invalid. |
| Service scheme | Name of a service scheme delivered by the server. You need to configure the corresponding service scheme and the network authorization and policy in the scheme on the NAS. |
| Idle-cut | Idle-cut time delivered by the server. After a user goes online, if the consecutive non-operation period or the duration when traffic is lower than a specified value exceeds the idle-cut time, the user is disconnected. |
| Reauthentication or forcible logout | Remaining service availability period delivered by the server. If the period expires, reauthentication is performed for the user or the user is forced to go offline according to the server-delivered action. |
Authorization Parameter |
Description |
|---|---|
VLAN |
VLAN-based authorization is easy to deploy and requires low maintenance costs. It applies to scenarios where employees in an office or a department have the same access rights. In local authorization, you only need to configure VLANs and corresponding network resources in the VLAN on the NAS. An authorized VLAN cannot be delivered to online Portal users. For MAC address-prioritized Portal authentication, the Agile Controller-Campus V1 delivers the session timeout attribute after Portal authentication succeeds so that users go offline immediately, and then delivers an authorized VLAN to users after the users pass MAC address authentication. After a user obtains VLAN-based authorization, the user needs to manually request an IP address using DHCP. |
Service scheme |
A service scheme and corresponding network resources in the scheme need to be configured on the NAS. |
User group (common mode) |
A user group consists of users (terminals) with the same attributes such as the role and rights. For example, you can divide users on a campus network into the R&D group, finance group, marketing group, and guest group based on the enterprise department structure, and grant different security policies to different departments. You need to configure a user group and corresponding network resources in the group on the NAS. |
UCL group (unified mode) |
UCL groups identify the user types. The administrator can add the users requiring the same network access policy to the same UCL group, and configure a set of network access policies for the group. You need to configure a UCL group and corresponding network resources in the group on the NAS. |