Domain-based User Management
An NAS performs domain-based user management. A domain is a group of users and each user belongs to a domain. A user uses only AAA configuration information in the domain to which the user belongs.
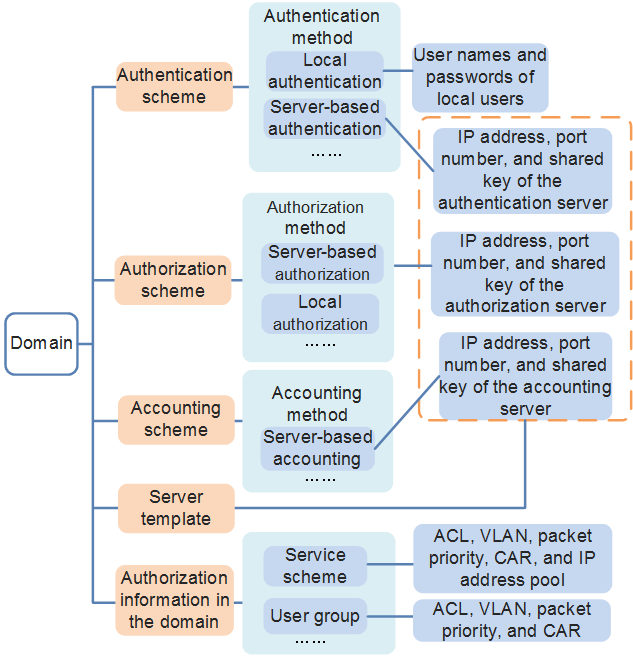
As shown in Figure 1, the domain manages configuration information including the AAA scheme, server template, and authorization information in a unified manner.
- AAA scheme: is divided into authentication, authorization, and accounting schemes that are used to define authentication, authorization, and accounting methods and the order in which the methods take effect. For details about the AAA scheme, see AAA Scheme.
Server template: is used to configure a server for authentication, authorization, and accounting. When a server is configured for authorization, you can obtain the authorization information from the server and domain. For details, see Figure 2.
If local authentication or authorization is used, you need to configure information related to the local user.
- Authorization information in the domain: can be configured in a domain. You can bind a service scheme and a user group to a domain. Authorization information includes the authorization ACL and VLAN can be configured in a user group.
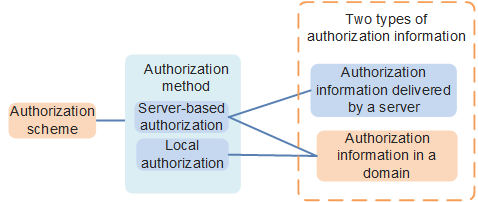
- If local authorization is used, the user obtains authorization information from the domain.
- If server-based authorization is used, the user obtains authorization information from the server or domain. Authorization information configured in a domain has lower priority than that delivered by a server. If the two types of authorization information conflicts, authorization information delivered by the server takes effect. If no conflict occurs, the two types of authorization information take effect simultaneously. In this manner, you can increase authorization flexibly by means of domain management, regardless of the authorization attributes provided by the AAA server.
Domain to Which a User Belongs
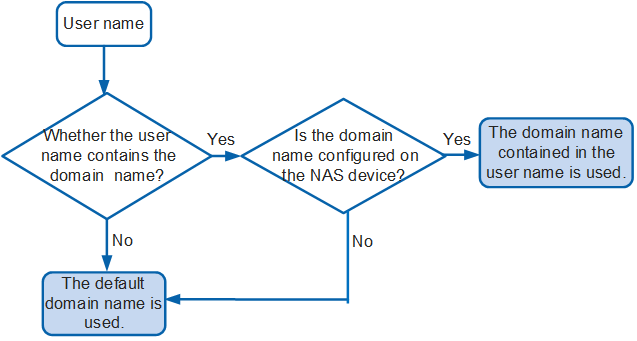
As shown in Figure 3, the domain to which a user belongs is determined by the user name for logging in to the NAS. If the user name does not contain the domain name or the domain name contained in the user name is not configured on the NAS, the NAS cannot determine the domain to which the user belongs. In this case, the NAS adds the user to the default domain based on the user type.

The accounting scheme default is bound to the two global default domains. Modifying the accounting scheme may affect configurations of the two domains.
The two global default domains cannot be deleted and can only be modified.
User Type |
User Access Mode |
Global Default Domain |
Default Configurations in the Global Default Domain | ||
|---|---|---|---|---|---|
| Authentication Scheme | Accounting Scheme | Authorization Scheme | |||
Administrator |
Is also called a login user and refers to the user who can log in to NAS through FTP, HTTP, SSH, Telnet, and the console port. |
default_admin |
default (local authentication) |
default (non-accounting) |
N/A |
Access user |
Includes NAC users (including 802.1X authenticated, MAC address authenticated, and Portal authenticated users). |
default |
radius (local authentication) |
default (non-accounting) |
N/A |
The global default domain can be customized based on actual requirements. The customized global default domain can be the global default common domain and the global default management domain at the same time.
<HUAWEI> display aaa configuration
Domain Name Delimiter : @
Domainname parse direction : Left to right
Domainname location : After-delimiter
Administrator user default domain: default_admin //Global default management domain
Normal user default domain : default //Global default common domain
For some access modes, you can specify the domain to which a user belongs using the command provided in the corresponding authentication profile to meet requirements of the user authentication management policy. For example, you can configure a default domain and a forcible domain for NAC access users on the NAS based on the authentication profile and specify the user type (802.1X, MAC address, or Portal authenticated user), achieving flexible configuration. The forcible domain, default domain, and domain carried in the user name are listed in descending order of the priority.
Forcible domain with a specified authentication method in the authentication profile > Forcible domain in the authentication profile > Domain carried in the user name > Default domain with a specified authentication method in the authentication profile > Default domain in the authentication profile > Global default domain. Note that a forcible domain specified for MAC address authenticated users within a MAC address range has the highest priority and takes precedence over that configured in an authentication profile.
Format of User Names Sent by an NAS to the RADIUS Server

- Only RADIUS authentication supports modification of the user-entered original user names.
- You can change the user-entered original user name based on the RADIUS server template.
An NAS can determine whether a user name sent to the RADIUS server contains the domain name based on the RADIUS server requirements. By default, an NAS directly sends the user-entered original user name to the RADIUS server without changing it.
You can set the format of user names sent by an NAS to the RADIUS server using the commands in Table 2.
The following commands modify only the user name format in RADIUS packets sent to the RADIUS server and do not modify the user name format in EAP packets. During 802.1X authentication, the RADIUS server checks whether the user name carried in EAP packets is the same as that on the RADIUS server. Therefore, you cannot modify the original user name using the radius-server user-name domain-included or undo radius-server user-name domain-included command during 802.1X authentication; otherwise, authentication may fail.
Command |
User Name Format |
User-entered User Name | User Name Sent by an NAS to the RADIUS Server |
|---|---|---|---|
radius-server user-name original |
User-entered original user name (default configuration) |
user-name@huawei.com | user-name@huawei.com |
| user-name | user-name | ||
radius-server user-name domain-included |
Domain name included |
user-name@huawei.com | user-name@huawei.com |
| user-name | user-name@default Assume that users use the default domain default. |
||
undo radius-server user-name domain-included |
Domain name excluded |
user-name@huawei.com | user-name |
| user-name | user-name | ||
undo radius-server user-name domain-included except-eap |
Domain name excluded NOTE:
This command takes effect only for non-EAP authenticated users. |
user-name@huawei.com | user-name |
| user-name | user-name |