Example for Configuring HWTACACS+Local Authentication, Command Authorization, and Command Auditing for Administrators
Networking Requirements
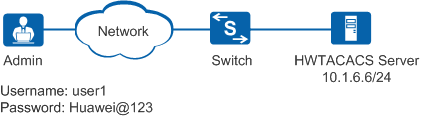
As shown in Figure 1, an HWTACACS server is deployed on an enterprise network. The enterprise requires that the administrator log in to the device through STelnet.
The administrator can log in to the device through STelnet only after entering a correct user name and password.
After the administrator logs in to the device through STelnet, the privilege level 15 is authorized to the administrator, the range of commands that the administrator can execute is limited, and commands that the administrator has executed are recorded.
If the link between the device and server is disconnected, the administrator will be authenticated locally during a login to the device.
Configuration Roadmap
Configure STelnet login on the switch: Set the authentication mode of accessing VTY user interfaces to AAA, enable the STelnet service, and configure the authentication mode and service type for SSH users.
Configure HWTACACS authentication on the switch: Create an HWTACACS server template, configure an AAA scheme, record the scheme, and enable command authorization.
- Configure a local user on the switch: Configure a local user name, password, and privilege level.
Precautions
- Ensure that there are reachable routes between devices.
Ensure that the shared key in the HWTACACS server template is the same as that configured on the HWTACACS server.
- If the login account is created on the switch but not on the HWTACACS server, HWTACACS authentication will fail and local authentication will not be performed. Local authentication will be performed only when the HWTACACS server is Down or does not respond.
- If the accounting mode is set to HWTACACS in an accounting scheme, the administrator will pass local authentication but fail to log in to the device because starting accounting will fail after the link between the device and server is disconnected. To prevent this problem, run the accounting start-fail online command in the accounting scheme view to allow users to go online after initial accounting fails.
- After the authorization scheme containing command authorization is applied in the administrator view, executing the undo authorization-cmd command will cause the administrator unable to execute any command except the quit command. In this case, the administrator needs to log in again.
- When the authorization and command authorization modes are set to hwtacacs local, HWTACACS authorization will be performed before commands are executed if the link between the device and server is disconnected. If the server does not respond, local authorization will be performed. As a result, there is a delay in executing commands.
Procedure
- Configure STelnet login.
# Generate a local key pair on the server.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] dsa local-key-pair create Info: The key name will be: Switch_Host_DSA. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: Info: Generating keys... Info: Succeeded in creating the DSA host keys.
# Set the authentication mode and protocol for accessing VTY user interfaces 0 to 14 to AAA and SSH, respectively.
[Switch] user-interface vty 0 14 [Switch-ui-vty0-14] authentication-mode aaa [Switch-ui-vty0-14] protocol inbound ssh [Switch-ui-vty0-14] quit
# Enable the SSH server function on the device.
[Switch] stelnet server enable
# Set the authentication mode and service type of all SSH users to password authentication and STelnet, respectively.
[Switch] ssh authentication-type default password

If the authentication mode and service type of only a few SSH users are password authentication and STelnet respectively, you can specify the SSH user name to set the authentication mode and service type of a single SSH user. For example, set the authentication mode and service type of an SSH user with the user name admin to password authentication and STelnet, respectively.
[Switch] ssh user admin authentication-type password
[Switch] ssh user admin service-type stelnet
- Configure HWTACACS authentication.
# Create an HWTACACS server template named template1 to enable the device and the HWTACACS server to communicate with each other.
[Switch] hwtacacs enable [Switch] hwtacacs-server template template1 [Switch-hwtacacs-template1] hwtacacs-server authentication 10.1.6.6 49 [Switch-hwtacacs-template1] hwtacacs-server authorization 10.1.6.6 49 [Switch-hwtacacs-template1] hwtacacs-server accounting 10.1.6.6 49 [Switch-hwtacacs-template1] hwtacacs-server shared-key cipher Hello@1234 [Switch-hwtacacs-template1] quit
# Create an authentication scheme named sch1 and set the authentication mode to HWTACACS+local authentication.
[Switch] aaa [Switch-aaa] authentication-scheme sch1 [Switch-aaa-authen-sch1] authentication-mode hwtacacs local [Switch-aaa-authen-sch1] quit
# Create an authorization scheme named sch2, set the authorization mode to HWTACACS+local authorization, and enable command authorization for the level-15 administrator.
[Switch-aaa] authorization-scheme sch2 [Switch-aaa-author-sch2] authorization-mode hwtacacs local [Switch-aaa-author-sch2] authorization-cmd 15 hwtacacs local [Switch-aaa-author-sch2] quit
# Create a recording scheme named sch0 to record commands that the administrator has executed.
[Switch-aaa] recording-scheme sch0 [Switch-aaa-recording-sch0] recording-mode hwtacacs template1 [Switch-aaa-recording-sch0] quit [Switch-aaa] cmd recording-scheme sch0
# Create an accounting scheme named sch3 and set the accounting mode to HWTACACS accounting.
[Switch-aaa] accounting-scheme sch3 [Switch-aaa-accounting-sch3] accounting-mode hwtacacs [Switch-aaa-accounting-sch3] accounting start-fail online [Switch-aaa-accounting-sch3] quit
# Apply the HWTACACS server template and AAA scheme to the domain huawei.com.
[Switch-aaa] domain huawei.com [Switch-aaa-domain-huawei.com] hwtacacs-server template1 [Switch-aaa-domain-huawei.com] authentication-scheme sch1 [Switch-aaa-domain-huawei.com] authorization-scheme sch2 [Switch-aaa-domain-huawei.com] accounting-scheme sch3 [Switch-aaa-domain-huawei.com] quit [Switch-aaa] quit
# Specify the domain huawei.com as a global default administrative domain.
[Switch] domain huawei.com admin
- Configure local authentication.
# Set the local account to user1, password to Huawei@123, and privilege level to 15.
[Switch] aaa [Switch-aaa] local-user user1 password irreversible-cipher Huawei@123 [Switch-aaa] local-user user1 service-type ssh [Switch-aaa] local-user user1 privilege level 15 [Switch-aaa] return
- Configure an HWTACACS server. Here, the Secure ACS is used as an example.
The configuration includes adding a device, adding an administrator account, setting the administrator level to 15, and configuring command authorization. Note that the reset hwtacacs-server statistics all command cannot be configured.
You can check logs recording command execution successes and failures of all users including non-HWTACACS-authenticated users under Reports and Activity > TACACS+ Administration.
- Verify the configuration.
- Check whether the administrator can successfully log in to the switch through STelnet.
Enter the user name user1@huawei.com and password Huawei@1234 configured on the HWTACACS server. The administrator is then successfully authenticated and logs in to the switch through STelnet.
- When the link between the switch and server is working properly, run the display access-user username user-name detail command on the switch to check information about the user user1.
In the command output, the values of User access type, User Privilege, User authentication type, Current authentication method, Current authorization method, and Current accounting method indicate that the login mode is SSH, the privilege level is 15, the authentication type is administrator authentication, and the authentication, authorization, as well as accounting modes are HWTACACS.
<Switch> display access-user username user1 detail ------------------------------------------------------------------------------ Basic: User ID : 11 User name : user1 Domain-name : huawei.com User MAC : - User IP address : 10.1.1.10 User IPv6 address : - User access time : 2019/07/10 09:15:02 User accounting session ID : huawei255255000000000f****2016009 Option82 information : - User access type : SSH User Privilege : AAA: User authentication type : Administrator authentication Current authentication method : HWTACACS Current authorization method : HWTACACS Current accounting method : HWTACACS ------------------------------------------------------------------------------ - After the administrator logs in to the switch, run the reset hwtacacs-server statistics all command. The system displays the message "Error: Failed to pass the authorization.", indicating command authorization succeeds.
<Switch> reset hwtacacs-server statistics all Error: Failed to pass the authorization.
- Check whether the administrator can successfully log in to the switch through STelnet.
Configuration Files
Switch configuration file
# sysname Switch # hwtacacs-server template template1 hwtacacs-server authentication 10.1.6.6 hwtacacs-server authorization 10.1.6.6 hwtacacs-server accounting 10.1.6.6 hwtacacs-server shared-key cipher %^%#)@1e81]jJP9}9O9|W>MT|TWbI,\rL4[.BT&@);rU%^%# # aaa authentication-scheme sch1 authentication-mode hwtacacs local authorization-scheme sch2 authorization-mode hwtacacs local authorization-cmd 15 hwtacacs local accounting-scheme sch3 accounting-mode hwtacacs accounting start-fail online recording-scheme sch0 recording-mode hwtacacs template1 cmd recording-scheme sch0 domain huawei.com authentication-scheme sch1 accounting-scheme sch3 authorization-scheme sch2 hwtacacs-server template1 local-user user1 password irreversible-cipher $1a$&YTv-xg$H<$Rj=5*sUqT+0i<B<0lAELMMraNPQAp'cD1!N~mjNI$ local-user user1 privilege level 15 local-user user1 service-type ssh # user-interface vty 0 14 authentication-mode aaa # stelnet server enable # return