Overview of ACLs
Definition
Access Control Lists (ACLs) filter packets based on an ordered set of rules that define the packet filtering conditions, such as the source address, destination address, and port number of packets.
An ACL is a packet filter, while ACL rules are the filter elements. When receiving a packet, a device checks the packet against ACL rules. If a match is found, the device forwards or discards the packet according to the policy used by a service module where the ACL is applied.
ACLs take effect only after they are applied to specific service modules, such as Telnet, FTP, and routing. A simple use case is to apply an ACL to a traffic policy or simplified traffic policy. This enables the device to deliver ACL rules globally, in a VLAN, or on an interface to filter packets to be forwarded. The service modules use different actions and mechanisms to process the packets matching ACLs. For details, see Default ACL Actions and Mechanisms of Different Service Modules.
Purpose
ACLs accurately identify and control packets on a network to manage network access behaviors, prevent network attacks, and improve bandwidth use efficiency. In this way, ACLs ensure security and high service quality on networks.
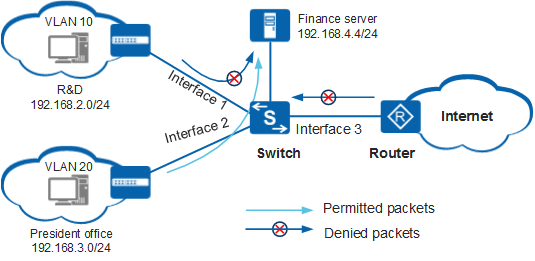
Figure 1 shows a typical network where ACLs are applied.
For financial data security, an enterprise requires that the finance server be accessible to the president office but block access from users in the R&D department. To achieve this, on Interface 1 of the switch, apply an ACL on the inbound direction so that the packets from the R&D department to the finance server are denied on the interface. On Interface 2, apply no ACL so that the interface can successfully forward the packets destined the finance server.
Additionally, to protect the enterprise intranet against viruses from the Internet, apply an ACL on the inbound direction of Interface 3 on the switch.