ACL Fundamentals
ACLs match packets against a sequential collection of rules, which can be implemented on software or hardware.
ACL Structure
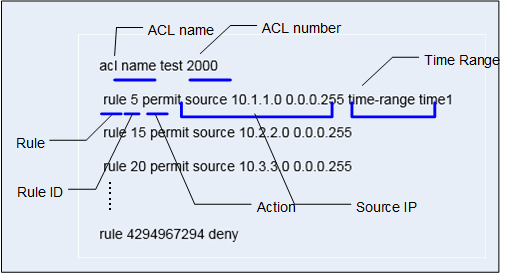
Figure 1 shows the structure of an ACL.
ACL name: identifies a named ACL, which is similar to representing IP addresses with domain names.
After creation, the name of a named ACL cannot be modified.
Repeated ACL names can only be used between basic ACL and basic ACL6, and between advanced ACL and advanced ACL6.
When defining a named ACL, you can add a number. If no number is specified, the system automatically allocates the largest number among the available number range based on the ACL type to the ACL's name.
ACL number: identifies a numbered ACL when it is defined separately.
For numbered ACLs, the number range varies depending on the ACL type.
Rule: describes packet matching conditions.
Rule ID: identifies an ACL rule, which can be manually configured or automatically allocated by the system.
ACL rule IDs range from 0 to 4294967294. Packets are matched against ACL rules in ascending order of the rule ID. The device stops matching a packet as long as a match is found.
Action: indicates how packets are processed, including permit and deny.
Matching condition: indicates criteria that packet must meet to match a rule. ACLs support a diverse array of matching conditions. In addition to the source IP address and time range in Figure 1, other matching conditions include Layer 2 Ethernet frame header information (source MAC, destination MAC, and Ethernet protocol type), Layer 3 packet information (destination IP address and protocol type), and Layer 4 packet information (TCP or UDP port number). For details about ACL matching conditions, see ACLs Supported by Switches and Common Matching Conditions.
ACL Implementation
ACLs can be implemented in hardware or software.
Software-based ACL: filters the interactive protocol packets destined for the local device, which must be sent to the CPU, for example, FTP, TFTP, Telnet, SNMP, HTTP, routing, and multicast protocol packets.
Hardware-based ACL: filters all packets by delivering ACL resources. Such ACLs include the ACL referenced by a traffic policy or simplified traffic policy, user group ACL, and ACL for adding outer VLAN tags to the packets received on interfaces.
They filter different types of packets. A software-based ACL filters the packets that must be sent to the CPU for processing, whereas a hardware-based ACL filters all packets.
They filter packets in different ways. A software-based ACL is referenced by upper-layer software to filter packets, which consumes CPU resources. A hardware-based ACL is delivered to hardware for packet filtering, which consumes hardware resources. Packet filtering is faster using a hardware-based ACL.
They take different actions on the packets that match no ACL rule. When packets do not match any ACL rule, a software-based ACL rejects the packets, whereas a hardware-ACL permits the packets.