ACL Matching
Matching Mechanism
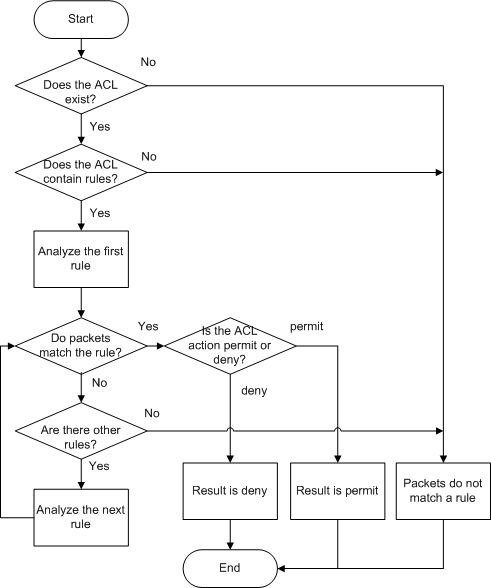
A device stops matching packets against ACL rules as long as a match is found, as detailed in Figure 1.
The packets match a rule in an ACL.
No ACL exists, the ACL contains no rule, or packets do not match any rule in an ACL.
Whether packets are permitted or denied is determined by actions specified in ACL rules and service modules that have ACLs applied. Different service modules process the packets that are filtered by ACL rules in different ways. For example, the Telnet module directly forwards the packets matching a permit rule, whereas the traffic policy module discards the packets matching a permit rule if the configured behavior in the traffic policy is deny. For details about ACL processing on each service module, see Default ACL Actions and Mechanisms of Different Service Modules.
Matching Order
An ACL consists of multiple rules, which may overlap or conflict. For example, an ACL contains two rules:
rule deny ip destination 10.1.0.0 0.0.255.255 //Packets destined for an IP address on the network segment 10.1.0.0/16 are denied. rule permit ip destination 10.1.1.0 0.0.0.255 //Packets destined for an IP address on the network segment 10.1.1.0/24 are permitted, which is smaller than the network segment 10.1.0.0/16.
If the system first matches a packet destined for the IP address 10.1.1.1 against the deny rule, the packet is discarded. However, if the system matches the packet against the permit rule first, the packet is forwarded.
Therefore, if ACL rules overlap or conflict, the matching order decides the matching result.
The device can match packets against ACLs in configuration (config) or automatic order (auto). The default order is config.
Config order
The system matches packets against ACL rules in ascending order of rule IDs. That is, the rule with the smallest ID takes effect first.
If a smaller rule ID is manually specified for a rule, the rule takes effect earlier than those with larger ruler IDs.
If no ID is manually specified for a rule, the system allocates an ID to the rule. This rule ID is the largest in the ACL and has the minimum multiple of the increment. Therefore, this rule is the last one that functions.
Auto order
The system arranges ACL rules based on their precision degree (depth first principle), and checks packets against the rules in descending order of precision. A rule with the highest precision defines strictest conditions, and has the highest priority. Table 1 describes how the auto order is applied to each type of ACL.
ACL Type |
Determining a Prior Rule by Comparing |
|---|---|
Basic ACL and basic ACL6 |
|
Advanced ACL and advanced ACL6 |
|
Layer 2 ACL |
|
User-defined ACL |
A user-defined ACL matches packets against rules in ascending order of rule IDs. |
User ACL and User ACL6 |
|
For details about the ACL matching conditions mentioned in Table 1, see ACLs Supported by Switches and Common Matching Conditions.
If you add a rule to an ACL in auto matching mode, the system automatically identifies the rule priority and assigns a rule ID accordingly.
For example, two rules are added to advanced ACL 3001 in auto mode:
rule deny ip destination 10.1.0.0 0.0.255.255 //Reject the packets destined for network segment 10.1.0.0/16. rule permit ip destination 10.1.1.0 0.0.0.255 //Permit the packets destined for network segment 10.1.1.0/24, which has a smaller range than 10.1.0.0/16.
The two rules specify the identical protocol range and source IP address range but do not specify VPN instances. According to the auto matching order in Table 1, the system compares the destination IP address ranges in the rules. The destination IP address range specified in the permit rule is smaller than that specified in the deny rule, so the permit rule has a higher precision. The system then allocates a smaller ID to the permit rule. Therefore, the system enables the two rules in ACL 3001 to function in the following order:
# acl number 3001 match-order auto rule 5 permit ip destination 10.1.1.0 0.0.0.255 rule 10 deny ip destination 10.1.0.0 0.0.255.255 #
A rule rule deny ip destination 10.1.1.1 0 is added to ACL 3001. (This rule has a higher priority than the previous two rules because the destination IP address is a host address.) The system reassigns IDs to the rules according to the rule priorities. The new order is as follows:
# acl number 3001 match-order auto rule 5 deny ip destination 10.1.1.1 0 rule 10 permit ip destination 10.1.1.0 0.0.0.255 rule 15 deny ip destination 10.1.0.0 0.0.255.255 #
Compared with the config mode, the auto mode is more complex. However, the auto mode is advantageous in some scenarios. For example, to ensure network security, the administrator has configured an ACL in auto mode to discard all IP packets on untrusted network segments. When more services are deployed on the network, some IP packets on these network segments need to be allowed. The auto matching mode allows the administrator to directly add new rules to the ACL, without the need to rearrange the rules.