Example for Using Basic ACLs to Filter OSPF Routes
Networking Requirements
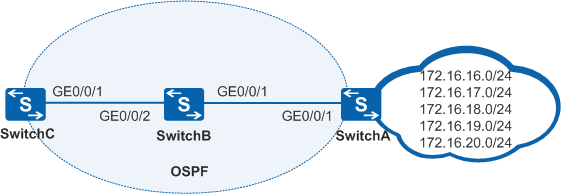
Figure 1 shows how on an OSPF network, SwitchA receives routes from the Internet and provides these routes for the OSPF network. A user wants devices on the OSPF network to access only the network segments 172.16.17.0/24, 172.16.18.0/24, and 172.16.19.0/24, and SwitchC to access only the network segment 172.16.18.0/24.
Device |
Interface |
VLANIF Interface |
IP Address |
|---|---|---|---|
SwitchA |
GE0/0/1 |
VLANIF10 |
192.168.1.1/24 |
SwitchB |
GE0/0/1 |
VLANIF10 |
192.168.1.2/24 |
SwitchB |
GE0/0/2 |
VLANIF20 |
192.168.2.1/24 |
SwitchC |
GE0/0/1 |
VLANIF20 |
192.168.2.2/24 |
Configuration Roadmap
The configuration roadmap is as follows:
Configure an ACL on SwitchA so that SwitchA advertises only the routes 172.16.17.0/24, 172.16.18.0/24, and 172.16.19.0/24 to SwitchB. In this case, the OSPF network can access only 172.16.17.0/24, 172.16.18.0/24, and 172.16.19.0/24.
Configure an ACL on SwitchC so that SwitchC receives only the route 172.16.18.0/24. In this case, the network connected to SwitchC can access only the network segment 172.16.18.0/24.
Procedure
- Add interfaces to VLANs.
# Configure SwitchA. Ensure that the configurations of SwitchB and SwitchC are the same as the configuration of SwitchA.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 10 [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type trunk [SwitchA-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [SwitchA-GigabitEthernet0/0/1] quit
- Assign IP addresses to VLANIF interfaces.
# Configure SwitchA. Ensure that the configurations of SwitchB and SwitchC are the same as the configuration of SwitchA.
[SwitchA] interface vlanif 10 [SwitchA-Vlanif10] ip address 192.168.1.1 24 [SwitchA-Vlanif10] quit
- Configure basic OSPF functions.
# Configure SwitchA.
[SwitchA] ospf [SwitchA-ospf-1] area 0 [SwitchA-ospf-1-area-0.0.0.0] network 192.168.1.0 0.0.0.255 [SwitchA-ospf-1-area-0.0.0.0] quit [SwitchA-ospf-1] quit
# Configure SwitchB.
[SwitchB] ospf [SwitchB-ospf-1] area 0 [SwitchB-ospf-1-area-0.0.0.0] network 192.168.1.0 0.0.0.255 [SwitchB-ospf-1-area-0.0.0.0] network 192.168.2.0 0.0.0.255 [SwitchB-ospf-1-area-0.0.0.0] quit [SwitchB-ospf-1] quit
# Configure SwitchC.
[SwitchC] ospf [SwitchC-ospf-1] area 0 [SwitchC-ospf-1-area-0.0.0.0] network 192.168.2.0 0.0.0.255 [SwitchC-ospf-1-area-0.0.0.0] quit [SwitchC-ospf-1] quit
- Configure five static routes on SwitchA and import these routes
into OSPF.
[SwitchA] ip route-static 172.16.16.0 24 NULL 0 [SwitchA] ip route-static 172.16.17.0 24 NULL 0 [SwitchA] ip route-static 172.16.18.0 24 NULL 0 [SwitchA] ip route-static 172.16.19.0 24 NULL 0 [SwitchA] ip route-static 172.16.20.0 24 NULL 0 [SwitchA] ospf [SwitchA-ospf-1] import-route static [SwitchA-ospf-1] quit
# Check the IP routing table on SwitchB. You can see that the five static routes are imported into OSPF.
[SwitchB] display ip routing-table Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 11 Routes : 11 Destination/Mask Proto Pre Cost Flags NextHop Interface 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 172.16.16.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10 172.16.17.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10 172.16.18.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10 172.16.19.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10 172.16.20.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10 192.168.1.0/24 Direct 0 0 D 192.168.1.2 Vlanif10 192.168.1.2/32 Direct 0 0 D 127.0.0.1 Vlanif10 192.168.2.0/24 Direct 0 0 D 192.168.2.1 Vlanif20 192.168.2.1/32 Direct 0 0 D 127.0.0.1 Vlanif20
- Configure a route advertisement policy.
# Configure ACL 2002 on SwitchA to allow only 172.16.17.0/24, 172.16.18.0/24, and 172.16.19.0/24 to pass.
[SwitchA] acl number 2002 [SwitchA-acl-basic-2002] rule permit source 172.16.17.0 0.0.0.255 [SwitchA-acl-basic-2002] rule permit source 172.16.18.0 0.0.0.255 [SwitchA-acl-basic-2002] rule permit source 172.16.19.0 0.0.0.255 [SwitchA-acl-basic-2002] quit
# Configure a route advertisement policy on SwitchA and associate ACL 2002 with the policy to filter routes.
[SwitchA] ospf [SwitchA-ospf-1] filter-policy 2002 export static [SwitchA-ospf-1] quit
# View the IP routing table on SwitchB. SwitchB has received only the three routes defined in ACL 2002.
[SwitchB] display ip routing-table Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 9 Routes : 9 Destination/Mask Proto Pre Cost Flags NextHop Interface 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 172.16.17.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10 172.16.18.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10 172.16.19.0/24 O_ASE 150 1 D 192.168.1.1 Vlanif10 192.168.1.0/24 Direct 0 0 D 192.168.1.2 Vlanif10 192.168.1.2/32 Direct 0 0 D 127.0.0.1 Vlanif10 192.168.2.0/24 Direct 0 0 D 192.168.2.1 Vlanif20 192.168.2.1/32 Direct 0 0 D 127.0.0.1 Vlanif20
- Configure a route receiving policy.
# Configure ACL 2003 on SwitchC to allow only 172.16.18.0/24 to pass.
[SwitchC] acl number 2003 [SwitchC-acl-basic-2003] rule permit source 172.16.18.0 0.0.0.255 [SwitchC-acl-basic-2003] quit
# Configure a route receiving policy on SwitchC and associate ACL 2003 with the policy to filter routes.
[SwitchC] ospf [SwitchC-ospf-1] filter-policy 2003 import [SwitchC-ospf-1] quit
# View the IP routing table on SwitchC. SwitchC has received only the route defined in ACL 2003.
[SwitchC] display ip routing-table Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 5 Routes : 5 Destination/Mask Proto Pre Cost Flags NextHop Interface 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 172.16.18.0/24 O_ASE 150 1 D 192.168.2.1 Vlanif20 192.168.2.0/24 Direct 0 0 D 192.168.2.2 Vlanif20 192.168.2.2/32 Direct 0 0 D 127.0.0.1 Vlanif20
Configuration Files
Configuration file of SwitchA
# sysname SwitchA # vlan batch 10 # acl number 2002 rule 5 permit source 172.16.17.0 0.0.0.255 rule 10 permit source 172.16.18.0 0.0.0.255 rule 15 permit source 172.16.19.0 0.0.0.255 # interface Vlanif10 ip address 192.168.1.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # ospf 1 filter-policy 2002 export static import-route static area 0.0.0.0 network 192.168.1.0 0.0.0.255 # ip route-static 172.16.16.0 255.255.255.0 NULL0 ip route-static 172.16.17.0 255.255.255.0 NULL0 ip route-static 172.16.18.0 255.255.255.0 NULL0 ip route-static 172.16.19.0 255.255.255.0 NULL0 ip route-static 172.16.20.0 255.255.255.0 NULL0 # return
Configuration file of SwitchB
# sysname SwitchB # vlan batch 10 20 # interface Vlanif10 ip address 192.168.1.2 255.255.255.0 # interface Vlanif20 ip address 192.168.2.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 # ospf 1 area 0.0.0.0 network 192.168.1.0 0.0.0.255 network 192.168.2.0 0.0.0.255 # return
Configuration file of SwitchC
# sysname SwitchC # vlan batch 20 # acl number 2003 rule 5 permit source 172.16.18.0 0.0.0.255 # interface Vlanif20 ip address 192.168.2.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 20 # ospf 1 filter-policy 2003 import area 0.0.0.0 network 192.168.2.0 0.0.0.255 # return