Egress ARP Inspection
Background
ARP Request packets are broadcast. As a result, if a device is connected to many other devices, this may create a lot of traffic and network congestion may occur, worsening network performance and affecting user services.
To decrease the number of ARP broadcast packets in a VLAN, egress ARP inspection (EAI) can be deployed on a device running DHCP snooping. EAI allows the device to query the DHCP snooping table for the outbound interface matching the destination IP address. The device then sends the ARP Request packets directly from the outbound interface. In this way, fewer ARP Request packets are broadcast on the network, reducing impact on the network and ensuring normal service running. In addition, EAI prevents user IP and MAC addresses from being detected by other users, thereby preventing ARP attacks.
Implementation
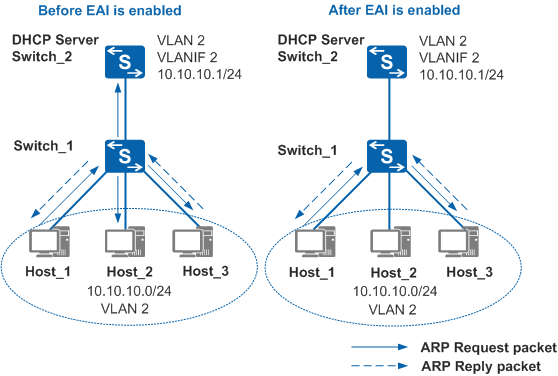
EAI ImplementationIn Figure 1, Switch_1 is connected to hosts that obtain IP addresses through DHCP. To communicate with Host_3, Host_1 in VLAN 2 sends an ARP Request packet to request Host_3's MAC address.
- If EAI is not enabled, Switch_1 broadcasts the received ARP Request packet in the VLAN.
- If EAI is enabled, Switch_1 queries the DHCP snooping table for
the outbound interface matching the destination IP address in the
received ARP Request packet.
- If an outbound interface is found, the device directly sends the packet to the mapping outbound interface. However, if the outbound interface is the same as the inbound interface of the packet, the device discards the packet.
- If no outbound interface is found, the device determines whether
the packet is received from a trusted interface. In DHCP snooping,
the interface connected to a DHCP server is generally configured as
a trusted interface.
- If the packet is received from a trusted interface, the device forwards the packet through another trusted interface. If there are no other trusted interfaces, the device discards the packet.
- If the packet is not received from a trusted interface, the device forwards the packet through a trusted interface.
Host_3 receives the ARP Request packet and then sends a unicast ARP Reply packet destined to Host_1.
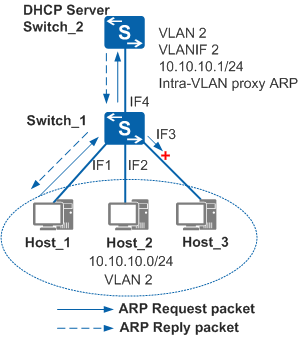
EAI Implementation (Port Isolation Scenario)If port isolation is configured between user-side interfaces, ARP packets cannot be forwarded between the interfaces. For example, in Figure 2, port isolation is configured between IF1 and IF3 on Switch_1. When Switch_1 detects that the outbound interface IF3 is isolated from the inbound interface IF1, it discards the ARP Request packet received from Host_1. As a result, Host_1 and Host_3 cannot communicate.
To solve this problem, enable Switch_1 to forward ARP packets to a trusted interface when the inbound and outbound interfaces are isolated, and configure intra-VLAN proxy ARP on Switch_2. When detecting that the outbound interface IF3 is isolated from the inbound interface IF1, Switch_1 directly forwards the received ARP Request packet to the trusted interface IF4. As Switch_2 is configured with intra-VLAN proxy ARP, it sends an ARP Reply packet after receiving the ARP Request packet. Host_1 and Host_3 can now communicate with each other.