Example for Configuring Attack Defense
Networking Requirements
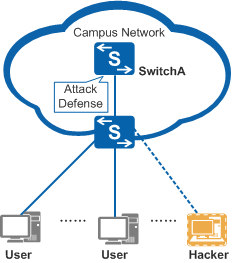
As shown in Figure 1, if a hacker on the LAN initiates malformed packet attacks, packet fragment attacks, and flood attacks to SwitchA, SwitchA may break down. The administrator intends to deploy attack defense measures on SwitchA to provide a secure network environment and ensure normal services.
Configuration Roadmap
The following configurations are performed on SwitchA. The configuration roadmap is as follows:
Enable defense against malformed packet attacks.
Enable defense against packet fragment attacks.
Enable defense against packet flood attacks.
Procedure
- Enable defense against malformed packet attacks.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] anti-attack abnormal enable
- Enable defense against packet fragment attacks and set the rate limit at which packet fragments are received to 15000 bit/s.
[SwitchA] anti-attack fragment enable [SwitchA] anti-attack fragment car cir 15000
- Enable defense against flood attacks.
# Enable defense against TCP SYN flood attacks and set the rate limit at which TCP SYN flood packets are received to 15000 bit/s.
[SwitchA] anti-attack tcp-syn enable [SwitchA] anti-attack tcp-syn car cir 15000
# Enable defense against UDP flood attacks to discard UDP packets sent from specified ports.
[SwitchA] anti-attack udp-flood enable# Enable defense against ICMP flood attacks and set the rate limit at which ICMP flood packets are received to 15000 bit/s.
[SwitchA] anti-attack icmp-flood enable [SwitchA] anti-attack icmp-flood car cir 15000
- Verify the configuration.
# After the configuration is complete, run the display anti-attack statistics command to view attack defense statistics.
[SwitchA] display anti-attack statistics Packets Statistic Information: ------------------------------------------------------------------------------- AntiAtkType TotalPacketNum DropPacketNum PassPacketNum (H) (L) (H) (L) (H) (L) ------------------------------------------------------------------------------- URPF 0 0 0 0 0 0 Abnormal 0 0 0 0 0 0 Fragment 0 0 0 0 0 0 Tcp-syn 0 34 0 28 0 6 Udp-flood 0 0 0 0 0 0 Icmp-flood 0 0 0 0 0 0 -------------------------------------------------------------------------------
SwitchA has statistics on discarded TCP SYN packets, indicating that the attack defense function takes effect.