File Management Modes
The device can function as a server or client to manage files.
- When the device functions as a server, you can access the device from a terminal to manage files on the device and transfer files between the device and the terminal.
- When the device functions as a client, you can use the device to manage files on other devices and transfer files between the device and other devices.
In Trivial File Transfer Protocol (TFTP) mode, the device can function only as a client. In File Transfer Protocol (FTP), Secure File Transfer Protocol (SFTP), Secure Copy Protocol (SCP), or File Transfer Protocol over SSL (FTPS) mode, the device can function both as a server and a client.
Table 1 describes the advantages and disadvantages of different file management modes. You can select one mode based on actual requirements.
Mode |
Application Scenario | Advantage | Disadvantage |
|---|---|---|---|
| Device login | In the scenario of managing storage media, directories, and files, log in to the device through the console port, Telnet, or STelnet. This login mode is mandatory for storage medium management. |
You can log in to the device directly to manage storage media, directories, and files. |
Only files on the local device can be managed. File transfer is not supported. |
| FTP | The FTP mode is applicable to the file transfer scenario with low network security requirements. The FTP mode is widely used in version upgrade. |
|
In FTP mode, data is transmitted in plain text, causing security risks. |
| TFTP | On the LAN of a lab, the TFTP mode can be used to load or upgrade versions online. The TFTP mode is applicable to the environment without complicated interactions between a client and a server. |
Compared with FTP mode, TFTP mode consumes less memory usage. |
|
| SFTP | The SFTP mode is applicable to the scenario with high network security requirements. The SFTP mode is widely used in log download and file backup. |
|
Configurations are complicated. |
| SCP | The SCP mode is applicable to the highly-efficient file upload and download scenarios with high network security requirements. |
|
Configurations are complicated (similar to SFTP configurations), and interactions are not supported. |
| FTPS | The FTPS mode is applicable to scenarios with high network requirements and no FTP function. | The FTPS mode uses the data encryption, user identity authentication, and message integrity check mechanisms to ensure the security of the TCP-based application-layer protocols. |
|
Device login, FTP, and TFTP are easy to learn and configure. The following section describes the remaining modes in more detail.
SFTP Mode
As a part of Secure Shell (SSH), SFTP allows remote users to securely log in to the device and perform file management and transmission through the security channel provided by SSH. Therefore, SFTP improves data transmission security. In addition, the device can function as the SSH client to connect to the remote SSH server for secure file transmission.
SSH security features:
- Encrypted transmission: When an SSH connection is set up, two devices negotiate an encryption algorithm and a session key to ensure secure communications between them.
- Public key-based authentication: The device supports the RSA, DSA, or ECC authentication mode.
- Server authentication: The SSH protocol authenticates a server based on the public key to defend against attacks from bogus servers.
- Interaction data check: The SSH protocol uses the CRC (for SSH1.5) or MD5-based MAC algorithm (for SSH2.0) to check the data integrity and authenticity. This mechanism protects the system from man-in-the-middle attacks.
Establishment of an SSH connection:
- Negotiate the SSH version.
The client and the server negotiate an SSH version by exchanging character strings that specify the SSH version.
- Negotiate the algorithm.
The server and the client negotiate the key exchange algorithm, encryption algorithm, and MAC algorithm for subsequent communications.
- Exchange keys.
Based on the key exchange algorithm, the server and the client obtain the same session key and session ID after calculation.
- Authenticate users.
The client sends an authentication request containing the user identity information to the server. If the authentication succeeds or expires, the client is disconnected from the server.
The public key-based and password-based authentication modes are supported.
- In public key-based (RSA, DSA, or ECC) authentication mode, the client must generate the RSA, DSA, or ECC key and send it to the server. When a user initiates an authentication request, the client randomly generates a text that is encrypted with the private key and sends it to the server. The server decrypts the text by using the public key. If decryption succeeds, the server considers this user trusted and grants this user access rights. If decryption fails, the client is disconnected from the server.
- Password-based authentication is implemented by the Authentication, Authorization and Accounting (AAA). Similar to Telnet and FTP, SSH supports local database authentication and remote RADIUS server authentication. The SSH server compares the user name and password of an SSH client with the preset ones. Authentication succeeds if both match.
- Request a session.
After user authentication is complete, the client sends a session request to the server. After receiving the request, the server processes it.
- Enter the interactive session.
After the session request is accepted, the SSH connection enters the interactive session mode. In this mode, data is transmitted bidirectionally.

Before an SSH connection is set up, the local key pair (RSA, DSA, or ECC key pair) must be generated on the server. The key pair is used to generate the session key and session ID and authenticate the server. This step is the key to SSH server configuration.
SCP Mode
Based on the SSH remote file copy function, SCP is used to copy, upload, and download files. SCP commands are easy to use, improving network maintenance efficiency.
FTPS Mode
FTPS combines FTP and Secure Sockets Layer (SSL). A client and server use SSL to authenticate each other and encrypt data to be transmitted. SSL ensures secure connections to FTP servers and greatly improves security of common FTP servers, enabling files of the device to be managed securely.
Concepts to learn before configuring the FTPS mode:
CA
CA is an entity that issues, manages, and abolishes digital certificates, and it authenticates identities of digital certificate owners. Root CAs are widely trusted in the world and authorize other lower-level CAs. CA identity information is provided in the file of a trusted CA.
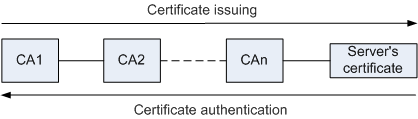
For example, CA1 is a root CA that issues a certificate to lower-level CA2, and CA2 issues the certificate to lower-level CA3. The certificate used by the server is issued by the lowest-level CA.
If the certificate of the server is issued by CA3, the certificate is authenticated as follows: CA3 authenticates the certificate of the server. If the authentication succeeds, CA2 authenticates the certificate of CA3. If the authentication succeeds, the root CA authenticates the certificate of CA2. Only when the root authentication succeeds, the certificate used by the server is valid.
Figure 1 shows the certificate issuing process and certificate authentication process.
Digital certificate
A digital certificate is an electronic document which uses a digital signature to bind a public key with an identity. The digital certificate contains information such as the name of a person or an organization and the address. The certificate can be used to verify that a public key belongs to an individual.
Users must obtain the public key of the message sending party to decode messages, and obtain the CA certificate of the message sending party to authenticate its identity.
CRL
The CA issues the Certificate Revocation List (CRL), containing a set of certificates that the CA regards as invalid.
The CA can shorten the validity period of a certificate using a CRL. The certificate validity period specified by the CRL is shorter than the original certificate validity period. If the CA revokes a certificate in the CRL, the declaration about authorized key pair is revoked before the certificate expires. When the certificate expires, data related to the certificate is cleared from the CRL to shorten the CRL.
Accessing a device functioning as the server or client:
- Access the device that functions as the FTP server on a terminal
Configure an SSL policy, load the digital certificate, and enable the FTPS server function on the device that functions as the FTP server. Users can use the FTP client that supports SSL to access the FTP server to manage files.
- Access the FTP server using the device that functions as an FTP client
Configure an SSL policy on the device that functions as the FTP client and load the trusted CA certificate to check the owner's identity.