Example for Configuring an SFTP Client
Networking Requirements
SSH provides a mechanism to authenticate the client and encrypts data bidirectionally, ensuring secure file transfer on insecure networks. The client uses SFTP to securely connect to the SSH server and transfer files.
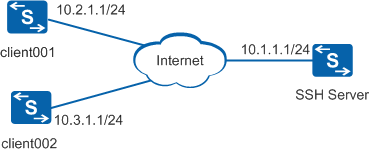
As shown in Figure 1, routes between the SSH server and clients client001 and client002 are reachable. In this example, a Huawei device functions as the SSH server.
Client001 and client002 connect to the SSH server using the password authentication mode and the DSA authentication mode, respectively.
Configuration Roadmap
The configuration roadmap is as follows:
- Generate a local key pair and enable the SFTP server function on the SSH server so that the server and client can securely exchange data.
- Create users client001 and client002 and set their authentication modes on the SSH server.
- Generate a local key pair on client002 and configure the DSA public key of client002 on the SSH server so that the server can authenticate the client when the client connects to the server.
- Log in to the SSH server as users client001 and client002 using SFTP and manage files.
Procedure
- Generate a local key pair and enable the SFTP server function on the SSH server.
<HUAWEI> system-view [HUAWEI] sysname SSH Server [SSH Server] dsa local-key-pair create Info: The key name will be: SSH Server_Host_DSA. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: Info: Generating keys... Info: Succeeded in creating the DSA host keys. [SSH Server] sftp server enable
- Create SSH users on the SSH server.
# Configure the VTY user interface.
[SSH Server] user-interface vty 0 4 [SSH Server-ui-vty0-4] authentication-mode aaa [SSH Server-ui-vty0-4] protocol inbound ssh [SSH Server-ui-vty0-4] user privilege level 3 [SSH Server-ui-vty0-4] quit
# Create an SSH user named client001 user and set the authentication mode to password for the user.
[SSH Server] ssh user client001 [SSH Server] ssh user client001 authentication-type password [SSH Server] ssh user client001 service-type sftp [SSH Server] ssh user client001 sftp-directory flash: [SSH Server] aaa [SSH Server-aaa] local-user client001 password irreversible-cipher Helloworld@6789 [SSH Server-aaa] local-user client001 service-type ssh [SSH Server-aaa] local-user client001 privilege level 3 [SSH Server-aaa] quit
# Create an SSH user named client002 and set the authentication mode to DSA for the user.
[SSH Server] ssh user client002 [SSH Server] ssh user client002 authentication-type dsa [SSH Server] ssh user client002 service-type sftp [SSH Server] ssh user client002 sftp-directory flash:
- Generate a local key pair on client002 and configure the DSA public key of client002 on the SSH server.
# Generate a local key pair on client002.
<HUAWEI> system-view [HUAWEI] sysname client002 [client002] dsa local-key-pair create Info: The key name will be: SSH Server_Host_DSA. Info: The key modulus can be any one of the following : 1024, 2048. Info: If the key modulus is greater than 512, it may take a few minutes. Please input the modulus [default=2048]: Info: Generating keys... Info: Succeeded in creating the DSA host keys. [client002] sftp server enable
# Check the DSA public key of the client.
[client002] display dsa local-key-pair public ===================================================== Time of Key pair created: 2014-03-03 19:11:04+00:00 Key name: client002_Host Key type: DSA encryption Key ===================================================== Key code: 30820109 02820100 C7D92E27 E88745D4 933AB1F5 DA692AC4 1D544BDC 8EA252B0 E90A5001 1F2567C6 3952DEFD 95EF93C2 D77E8CDF B36E7F43 57C1D7BA 0978DD7A 2F7F7187 04FD6A03 C4FFDB58 04B3A0C4 B6E50528 AAE56FF9 5F66EE00 8E4702DB AA764006 322E6F72 CC9C1A39 462DBCD0 EA934441 1678BA23 40473EC4 58DF84FA 20C9CB60 98E5ACDA 2E98B55A 0299FBAB FE91EFA3 E155E065 7C7FFCD4 4EAB71EC A7A73DD7 AC8474B7 2DD37D1C 710C6E14 57DA200C 477E45BC 38AC7685 BD8D6325 CCBE3F32 85435E5B EB6A08DF 752B7EBD CE21CFCB F3AC0C35 671E5ACC AFC36F0B 54E646F6 D12B4BA3 6E9EF69F A5BED377 954709EB CE29A923 04B347D7 29296E7D 3D5F69AB 4365AA2F 0203 010001 Host public key for PEM format code: ---- BEGIN SSH2 PUBLIC KEY ---- AAAAB3NzaC1yc2EAAAADAQABAAABAQDH2S4n6IdF1JM6sfXaaSrEHVRL3I6iUrDp ClABHyVnxjlS3v2V75PC136M37Nuf0NXwde6CXjdei9/cYcE/WoDxP/bWASzoMS2 5QUoquVv+V9m7gCORwLbqnZABjIub3LMnBo5Ri280OqTREEWeLojQEc+xFjfhPog yctgmOWs2i6YtVoCmfur/pHvo+FV4GV8f/zUTqtx7KenPdeshHS3LdN9HHEMbhRX 2iAMR35FvDisdoW9jWMlzL4/MoVDXlvragjfdSt+vc4hz8vzrAw1Zx5azK/DbwtU 5kb20StLo26e9p+lvtN3lUcJ684pqSMEs0fXKSlufT1faatDZaov ---- END SSH2 PUBLIC KEY ---- Public key code for pasting into OpenSSH authorized_keys file : ssh-dsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDH2S4n6IdF1JM6sfXaaSrEHVRL3I6iUrDpClABHyVnxjlS3v2V75PC136M37Nuf0NXwde6CXjdei9/cYcE/WoDxP/bWASz oMS25QUoquVv+V9m7gCORwLbqnZABjIub3LMnBo5Ri280OqTREEWeLojQEc+xFjfhPogyctgmOWs2i6YtVoCmfur/pHvo+FV4GV8f/zUTqtx7KenPdeshHS3LdN9HHEMbhRX 2iAMR35FvDisdoW9jWMlzL4/MoVDXlvragjfdSt+vc4hz8vzrAw1Zx5azK/DbwtU5kb20StLo26e9p+lvtN3lUcJ684pqSMEs0fXKSlufT1faatDZaov= dsa-key
# Configure the DSA public key of client002 on the SSH server. (Information in bold in the display command output is the DSA public key of client002. Copy the information to the server.)[SSH Server] dsa peer-public-key dsakey001 encoding-type der [SSH Server-dsa-public-key] public-key-code begin [SSH Server-dsa-key-code] 30820109 [SSH Server-dsa-key-code] 02820100 [SSH Server-dsa-key-code] C7D92E27 E88745D4 933AB1F5 DA692AC4 1D544BDC [SSH Server-dsa-key-code] 8EA252B0 E90A5001 1F2567C6 3952DEFD 95EF93C2 [SSH Server-dsa-key-code] D77E8CDF B36E7F43 57C1D7BA 0978DD7A 2F7F7187 [SSH Server-dsa-key-code] 04FD6A03 C4FFDB58 04B3A0C4 B6E50528 AAE56FF9 [SSH Server-dsa-key-code] 5F66EE00 8E4702DB AA764006 322E6F72 CC9C1A39 [SSH Server-dsa-key-code] 462DBCD0 EA934441 1678BA23 40473EC4 58DF84FA [SSH Server-dsa-key-code] 20C9CB60 98E5ACDA 2E98B55A 0299FBAB FE91EFA3 [SSH Server-dsa-key-code] E155E065 7C7FFCD4 4EAB71EC A7A73DD7 AC8474B7 [SSH Server-dsa-key-code] 2DD37D1C 710C6E14 57DA200C 477E45BC 38AC7685 [SSH Server-dsa-key-code] BD8D6325 CCBE3F32 85435E5B EB6A08DF 752B7EBD [SSH Server-dsa-key-code] CE21CFCB F3AC0C35 671E5ACC AFC36F0B 54E646F6 [SSH Server-dsa-key-code] D12B4BA3 6E9EF69F A5BED377 954709EB CE29A923 [SSH Server-dsa-key-code] 04B347D7 29296E7D 3D5F69AB 4365AA2F [SSH Server-dsa-key-code] 0203 [SSH Server-dsa-key-code] 010001 [SSH Server-dsa-key-code] public-key-code end [SSH Server-dsa-public-key] peer-public-key end
# Bind the DSA public key to the SSH user client002.
[SSH Server] ssh user client002 assign dsa-key dsakey001
- Connect SFTP clients to the SSH server.
# If the clients connect to the SSH server for the first time, enable the initial authentication function on the clients.
Enable the initial authentication function on client001.
<HUAWEI> system-view [HUAWEI] sysname client001 [client001] ssh client first-time enable
Enable the initial authentication function on client002.
[client002] ssh client first-time enable
# Log in to the SSH server from client001 in password authentication mode.
[client002] sftp 10.1.1.1 Please input the username:client002 Trying 10.1.1.1 ... Press CTRL+K to abort Connected to 10.1.1.1 ... password:SSH_SERVER_CODE Please select public key type for user authentication [R for RSA; D for DSA; Enter for Skip publickey authentication; Ctrl_C for Cancel], Please select [R, D, Enter or Ctrl_C]:D sftp-client># Log in to the SSH server from client002 in DSA authentication mode.
[client002] sftp 10.1.1.1 Please input the username:client002 Trying 10.1.1.1 ... Press CTRL+K to abort Connected to 10.1.1.1 ... password:SSH_SERVER_CODE Please select public key type for user authentication [R for RSA; D for DSA; Enter for Skip publickey authentication; Ctrl_C for Cancel], Please select [R, D, Enter or Ctrl_C]:D sftp-client> - Verify the configuration.
Run the display ssh server status command to check that the SFTP service has been enabled. Run the display ssh user-information command to view information about the configured SSH users.
# Check the SSH server status.
[SSH Server] display ssh server status SSH version :1.99 SSH connection timeout :60 seconds SSH server key generating interval :0 hours SSH authentication retries :3 times SFTP server :Enable Stelnet server :Disable Scp server :Disable SSH server source :0.0.0.0 ACL4 number :0 ACL6 number :0# Check information about SSH users.
[SSH Server] display ssh user-information User 1: User Name : client001 Authentication-type : password User-public-key-name : - User-public-key-type : - Sftp-directory : flash: Service-type : sftp Authorization-cmd : No User 2: User Name : client002 Authentication-type : dsa User-public-key-name : dsakey001 User-public-key-type : dsa Sftp-directory : flash: Service-type : sftp Authorization-cmd : No
Configuration File
SSH server configuration file
# sysname SSH Server # dsa peer-public-key dsakey001 encoding-type der public-key-code begin 30820109 02820100 C7D92E27 E88745D4 933AB1F5 DA692AC4 1D544BDC 8EA252B0 E90A5001 1F2567C6 3952DEFD 95EF93C2 D77E8CDF B36E7F43 57C1D7BA 0978DD7A 2F7F7187 04FD6A03 C4FFDB58 04B3A0C4 B6E50528 AAE56FF9 5F66EE00 8E4702DB AA764006 322E6F72 CC9C1A39 462DBCD0 EA934441 1678BA23 40473EC4 58DF84FA 20C9CB60 98E5ACDA 2E98B55A 0299FBAB FE91EFA3 E155E065 7C7FFCD4 4EAB71EC A7A73DD7 AC8474B7 2DD37D1C 710C6E14 57DA200C 477E45BC 38AC7685 BD8D6325 CCBE3F32 85435E5B EB6A08DF 752B7EBD CE21CFCB F3AC0C35 671E5ACC AFC36F0B 54E646F6 D12B4BA3 6E9EF69F A5BED377 954709EB CE29A923 04B347D7 29296E7D 3D5F69AB 4365AA2F 0203 010001 public-key-code end peer-public-key end # aaa local-user client001 password irreversible-cipher $1a$P2m&M5d"'JHR7b~SrcHF\Z\,2R"t&6V|zOLh9y$>M\bjG$D>%@Ug/<3I$+=Y$ local-user client001 privilege level 3 local-user client001 service-type ssh # sftp server enable ssh user client001 ssh user client001 authentication-type password ssh user client001 service-type sftp ssh user client001 sftp-directory flash: ssh user client002 ssh user client002 authentication-type dsa ssh user client002 assign dsa-key dsakey001 ssh user client002 service-type sftp ssh user client002 sftp-directory flash: # user-interface vty 0 4 authentication-mode aaa user privilege level 3 # returnClient001 configuration file
# sysname client001 # ssh client first-time enable # return
Client002 configuration file
# sysname client002 # ssh client first-time enable # return