(Optional) Configuring NAT Traversal
Context
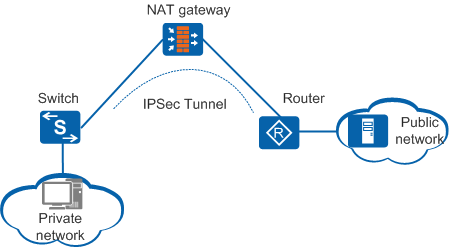
During IPSec VPN deployment, the initiator on a private network may need to establish an IPSec tunnel with the responder on a public network. To ensure that an IPSec tunnel can be established when a network address translation (NAT) device exists, NAT traversal is required, as shown in Figure 1.
During Encapsulating Security Payload (ESP) integrity check, an outer IP header is not checked. If only address translation is performed, ESP can work properly. ESP is a Layer 3 protocol and does not support port setting, so there is also a problem in ESP when NAT port translation is used. To address this issue, NAT traversal encapsulates ESP packets with a UDP header. In transport mode, a standard UDP header is inserted between the original IP header and an ESP header during NAT traversal. In tunnel mode, a standard UDP header is inserted between the new IP header and an ESP header during NAT traversal. When ESP packets pass through a NAT device, the NAT device translates the IP address and port number of the outer IP header and inserted UDP header. After the translated packets reach the remote end of the IPSec tunnel, the remote end processes these packets in the same manner as IPSec packets.
If no IPSec packets are transmitted on an IPSec tunnel in a period of time, NAT session entries may be aged out and deleted because the NAT session entries have the keepalive time. As a result, the IPSec tunnel cannot transmit IPSec packets between the NAT device and the IKE peer connected to the public network. To prevent NAT session entries from being aged, an IKE SA on the private network side of the NAT device sends NAT Keepalive packets to its remote end at an interval to maintain the NAT session.

By default, NAT traversal is enabled.