Application Scenarios for IPSG
IPSG is used on campus networks to prevent network access from hosts using stolen IP addresses.
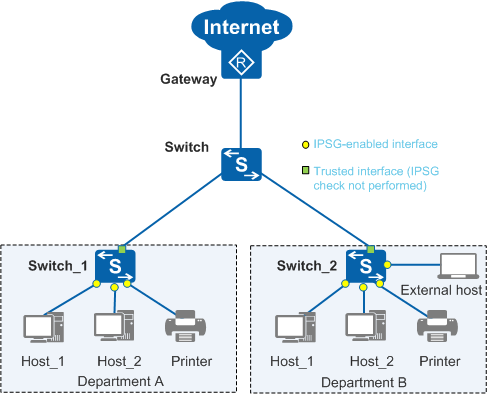
Figure 1 shows a typical campus network. Generally:
- If a campus network is small, the hosts and printers use static IP addresses.
- If a campus network is large, the hosts obtain IP addresses through DHCP, and some printers use static IP addresses.
IPSG is configured on the switches (Switch_1 and Switch_2) to which users connect.
Scenario 1: IPSG Prevents Access from the Hosts That Change Their IP Addresses
- Hosts are permitted to access the network using only the IP addresses allocated by the DHCP server or static IP addresses configured by the administrator. If a host changes its IP address without permission, the host cannot access the network. This prevents hosts from obtaining network rights without permission.
- Static IP addresses configured for printers can be used only by the printers, and cannot be used by hosts to access the network.
Scenario 2: IPSG Prevents Access from Unauthorized Hosts (Static IP Addresses Are Used on the Network)
- Each host can connect only to a fixed port and cannot change the access location. The traffic rate on ports is limited.
- Users cannot access the intranet with their own computers. This prevents intranet resource leaks.
If hosts obtain IP addresses through DHCP, NAC (such as Portal or 802.1X authentication) can be configured to prevent unauthorized host access.