Example for Applying the Keychain to RIP
Networking Requirements
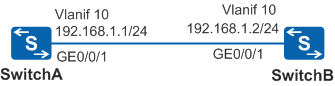
As shown in Figure 1, SwitchA and SwitchB are connected using RIP-2.
The RIP connection needs to be retained during data transmission.
Configuration Roadmap
To ensure stable RIP connections, RIP protocol packets must be correctly transmitted. You are advised to authenticate and encrypt the packets to ensure transmission security. In addition, to prevent unauthorized users from forging algorithms and key strings used in authentication and encryption, you are advised to dynamically change algorithms and key strings to ensure secure RIP packet transmission. Therefore, the keychain protocol is used to ensure stability of RIP connections.
The configuration roadmap is as follows:
Configure basic RIP functions.
Configure a keychain.
Apply the keychain to RIP.
Procedure
- Configure basic RIP functions.
# Configure Switch A.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] rip 1 [SwitchA-rip-1] version 2 [SwitchA-rip-1] network 192.168.1.0 [SwitchA-rip-1] quit
# Configure Switch B.
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] rip 1 [SwitchB-rip-1] version 2 [SwitchB-rip-1] network 192.168.1.0 [SwitchB-rip-1] quit
- Configure a keychain.
# Configure Switch A.
[SwitchA] keychain huawei mode absolute [SwitchA-keychain-huawei] receive-tolerance 100 [SwitchA-keychain-huawei] key-id 1 [SwitchA-keychain-huawei-keyid-1] algorithm hmac-sha-256 [SwitchA-keychain-huawei-keyid-1] key-string cipher Huawei@1234 [SwitchA-keychain-huawei-keyid-1] send-time 0:00 2016-01-01 to 23:59 2016-05-01 [SwitchA-keychain-huawei-keyid-1] receive-time 0:00 2016-01-01 to 23:59 2016-05-01 [SwitchA-keychain-huawei-keyid-1] default send-key-id [SwitchA-keychain-huawei-keyid-1] quit [SwitchA-keychain-huawei] quit
# Configure Switch B.
[SwitchB] keychain huawei mode absolute [SwitchB-keychain-huawei] receive-tolerance 100 [SwitchB-keychain-huawei] key-id 1 [SwitchB-keychain-huawei-keyid-1] algorithm hmac-sha-256 [SwitchB-keychain-huawei-keyid-1] key-string cipher Huawei@1234 [SwitchB-keychain-huawei-keyid-1] send-time 0:00 2016-01-01 to 23:59 2016-05-01 [SwitchB-keychain-huawei-keyid-1] receive-time 0:00 2016-01-01 to 23:59 2016-05-01 [SwitchB-keychain-huawei-keyid-1] default send-key-id [SwitchB-keychain-huawei-keyid-1] quit [SwitchB-keychain-huawei] quit
- Apply the keychain to RIP.
# Configure Switch A.
[SwitchA] vlan 10 [SwitchA-vlan10] quit [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type hybrid [SwitchA-GigabitEthernet0/0/1] port hybrid pvid vlan 10 [SwitchA-GigabitEthernet0/0/1] port hybrid untagged vlan 10 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface vlanif 10 [SwitchA-Vlanif10] ip address 192.168.1.1 24 [SwitchA-Vlanif10] rip authentication-mode hmac-sha256 cipher huawei 1 [SwitchA-Vlanif10] quit [SwitchA] quit
# Configure Switch B.
[SwitchB] vlan 10 [SwitchB-vlan10] quit [SwitchB] interface gigabitethernet 0/0/1 [SwitchB-GigabitEthernet0/0/1] port link-type hybrid [SwitchB-GigabitEthernet0/0/1] port hybrid pvid vlan 10 [SwitchB-GigabitEthernet0/0/1] port hybrid untagged vlan 10 [SwitchB-GigabitEthernet0/0/1] quit [SwitchB] interface vlanif 10 [SwitchB-Vlanif10] ip address 192.168.1.2 24 [SwitchB-Vlanif10] rip authentication-mode hmac-sha256 cipher huawei 1 [SwitchB-Vlanif10] quit [SwitchB] quit
- Verify the configuration.
# Run the display keychain keychain-name command to check the key-id status of the keychain.
<SwitchA> display keychain huawei Keychain Information: --------------------- Keychain Name : huawei Timer Mode : Absolute Time Type : Lmt Receive Tolerance(min) : 100 TCP Kind : 254 TCP Algorithm IDs : HMAC-MD5 : 5 HMAC-SHA1-12 : 2 HMAC-SHA1-20 : 6 HMAC-SHA-256 : 7 SHA-256 : 8 MD5 : 3 SHA1 : 4 Number of Key IDs : 1 Active Send Key ID : 1 Active Receive Key IDs : 01 Default send Key ID : 1 Default send Key Status : Inactive Key ID Information: ------------------- Key ID : 1 Key string : ****** Algorithm : HMAC-SHA-256 SEND TIMER : Start time : 2016-01-01 00:00 End time : 2016-05-01 23:59 Status : Active RECEIVE TIMER : Start time : 2016-01-01 00:00 End time : 2016-05-01 23:59 Status : Active# After the keychain is applied to RIP, run the display rip process-id interface verbose command to check the authentication mode of RIP packets. The display on Switch A is used as an example.
<SwitchA> display rip 1 interface verbose Vlanif10(192.168.1.1) State : UP MTU : 500 Metricin : 0 Metricout : 1 Input : Enabled Output : Enabled Protocol : RIPv2 Multicast Send version : RIPv2 Multicast Packets Receive version : RIPv2 Multicast and Broadcast Packets Poison-reverse : Disabled Split-Horizon : Enabled Authentication type : SHA256 (HMAC - Password) Last Sequence Number Sent : 0x0 Replay Protection : Disabled
Configuration Files
Switch A configuration file
# sysname SwitchA # vlan batch 10 # keychain huawei mode absolute receive-tolerance 100 key-id 1 algorithm hmac-sha-256 key-string cipher %^%#Vj-D<jJ%aNGasyD!w#hVP]6xEn`_l(7bf6%m;P3P%^%# send-time 00:00 2016-01-01 to 23:59 2016-05-01 receive-time 00:00 2016-01-01 to 23:59 2016-05-01 default send-key-id # interface Vlanif10 ip address 192.168.1.1 255.255.255.0 rip authentication-mode hmac-sha256 cipher %^%#*@UfXt!vp3dob9:(f5V;{PO1/:#Fd"9P<6*aJ{lJ%^%# 1 # interface GigabitEthernet0/0/1 port link-type hybrid port hybrid pvid vlan 10 port hybrid untagged vlan 10 # rip 1 version 2 network 192.168.1.0 # return
Configuration file of Switch B
# sysname SwitchB # vlan batch 10 # keychain huawei mode absolute receive-tolerance 100 key-id 1 algorithm hmac-sha-256 key-string cipher %^%#Dvqg<X&x>"h`1&Q\1RAT>0\TVnbc<FJyVlAy=p<#%^%# send-time 00:00 2016-01-01 to 23:59 2016-05-01 receive-time 00:00 2016-01-01 to 23:59 2016-05-01 default send-key-id # interface Vlanif10 ip address 192.168.1.2 255.255.255.0 rip authentication-mode hmac-sha256 cipher %^%#*@UfXt!vp3dob9:(f5V;{PO1/:#Fd"9P<6*aJ{lJ%^%# 1 # interface GigabitEthernet0/0/1 port link-type hybrid port hybrid pvid vlan 10 port hybrid untagged vlan 10 # rip 1 version 2 network 192.168.1.0 # return