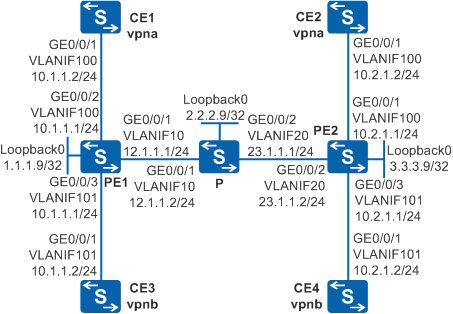
Example for Configuring BGP/MPLS IP VPNs with Overlapping Address Spaces
Networking Requirements
- CE1 connects to the headquarters R&D area of a company, and CE2 connects to the branch R&D area. CE1 and CE2 belong to vpna.
- CE3 connects to the headquarters non-R&D area, and CE4 connects to the branch non-R&D area. CE3 and CE4 belong to vpnb.
- The R&D areas and the non-R&D areas of the headquarters and branch use overlapping address spaces.
The company wants to ensure secure communication between the headquarters and branch and isolate the R&D areas from non-R&D areas, without changing the current network deployment.
Context
The configuration roadmap is as follows:
- Configure OSPF between the P and PEs to ensure IP connectivity on the backbone network.
- Configure basic MPLS capabilities and MPLS LDP on the P and PEs to establish MPLS LSP tunnels for VPN data transmission on the backbone network.
- Configure MP-IBGP on PE1 and PE2 to enable them to exchange VPN routing information.
- Configure VPN instances vpna and vpnb on PE1 and PE2. Set the VPN target of vpna to 100:100 and the VPN target of vpnb to 200:200. This configuration allows users in the same VPN to communicate with each other and isolates users on different VPNs. Bind the PE interfaces connected to CEs to the corresponding VPN instances to provide access for VPN users.
- Configure static routes on the CEs and PEs to exchange VPN routing information.
Procedure
- Configure VLANs on interfaces and assign IP addresses to the VLANIF interfaces and loopback interfaces according to Figure 1.
# Configure PE1. The configuration on PE2, P, and CE1 to CE4 is similar to the configuration on PE1 and is not mentioned here.
<HUAWEI> system-view [HUAWEI] sysname PE1 [PE1] interface loopback 0 [PE1-LoopBack0] ip address 1.1.1.9 32 [PE1-LoopBack0] quit [PE1] vlan batch 10 100 101 [PE1] interface gigabitethernet 0/0/1 [PE1-GigabitEthernet0/0/1] port link-type trunk [PE1-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [PE1-GigabitEthernet0/0/1] quit [PE1] interface gigabitethernet 0/0/2 [PE1-GigabitEthernet0/0/2] port link-type trunk [PE1-GigabitEthernet0/0/2] port trunk allow-pass vlan 100 [PE1-GigabitEthernet0/0/2] quit [PE1] interface gigabitethernet 0/0/3 [PE1-GigabitEthernet0/0/3] port link-type trunk [PE1-GigabitEthernet0/0/3] port trunk allow-pass vlan 101 [PE1-GigabitEthernet0/0/3] quit [PE1] interface vlanif 10 [PE1-Vlanif10] ip address 12.1.1.1 24 [PE1-Vlanif10] quit
- Configure OSPF on the MPLS backbone network so that the PEs and P can communicate with each other.
# Configure PE1.
[PE1] ospf [PE1-ospf-1] area 0 [PE1-ospf-1-area-0.0.0.0] network 1.1.1.9 0.0.0.0 [PE1-ospf-1-area-0.0.0.0] network 12.1.1.0 0.0.0.255 [PE1-ospf-1-area-0.0.0.0] quit [PE1-ospf-1] quit
# Configure P.
[P] ospf [P-ospf-1] area 0 [P-ospf-1-area-0.0.0.0] network 2.2.2.9 0.0.0.0 [P-ospf-1-area-0.0.0.0] network 12.1.1.0 0.0.0.255 [P-ospf-1-area-0.0.0.0] network 23.1.1.0 0.0.0.255 [P-ospf-1-area-0.0.0.0] quit [P-ospf-1] quit
# Configure PE2.
[PE2] ospf [PE2-ospf-1] area 0 [PE2-ospf-1-area-0.0.0.0] network 3.3.3.9 0.0.0.0 [PE2-ospf-1-area-0.0.0.0] network 23.1.1.0 0.0.0.255 [PE2-ospf-1-area-0.0.0.0] quit [PE2-ospf-1] quit
After the configuration is complete, OSPF neighbor relationships are established between PE1 and P, and between PE2 and P. Run the display ospf peer command. The command output shows that the neighbor status is Full. Run the display ip routing-table command. The command output shows that PEs have learned the routes to Loopback0 of each other.
The information displayed on PE1 is used as an example.
[PE1] display ip routing-table Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: Public Destinations : 8 Routes : 8 Destination/Mask Proto Pre Cost Flags NextHop Interface 1.1.1.9/32 Direct 0 0 D 127.0.0.1 LoopBack0 2.2.2.9/32 OSPF 10 1 D 12.1.1.2 Vlanif10 3.3.3.9/32 OSPF 10 2 D 12.1.1.2 Vlanif10 12.1.1.0/24 Direct 0 0 D 12.1.1.1 Vlanif10 12.1.1.1/32 Direct 0 0 D 127.0.0.1 Vlanif10 23.1.1.0/24 OSPF 10 2 D 12.1.1.2 Vlanif10 127.0.0.0/8 Direct 0 0 D 127.0.0.1 InLoopBack0 127.0.0.1/32 Direct 0 0 D 127.0.0.1 InLoopBack0 - Configure basic MPLS capabilities and MPLS LDP on the MPLS backbone network to establish LDP LSPs.
# Configure PE1.
[PE1] mpls lsr-id 1.1.1.9 [PE1] mpls [PE1-mpls] quit [PE1] mpls ldp [PE1-mpls-ldp] quit [PE1] interface vlanif 10 [PE1-Vlanif10] mpls [PE1-Vlanif10] mpls ldp [PE1-Vlanif10] quit
# Configure P.
[P] mpls lsr-id 2.2.2.9 [P] mpls [P-mpls] quit [P] mpls ldp [P-mpls-ldp] quit [P] interface vlanif 10 [P-Vlanif10] mpls [P-Vlanif10] mpls ldp [P-Vlanif10] quit [P] interface vlanif 20 [P-Vlanif20] mpls [P-Vlanif20] mpls ldp [P-Vlanif20] quit
# Configure PE2.
[PE2] mpls lsr-id 3.3.3.9 [PE2] mpls [PE2-mpls] quit [PE2] mpls ldp [PE2-mpls-ldp] quit [PE2] interface vlanif 20 [PE2-Vlanif20] mpls [PE2-Vlanif20] mpls ldp [PE2-Vlanif20] quit
After the configuration is complete, LDP sessions are established between PE1 and the P and between the P and PE2. Run the display mpls ldp session command. The command output shows that the Status field is Operational. Run the display mpls ldp lsp command. Information about the established LDP LSPs is displayed.
The information displayed on PE1 is used as an example.
[PE1] display mpls ldp session LDP Session(s) in Public Network Codes: LAM(Label Advertisement Mode), SsnAge Unit(DDDD:HH:MM) A '*' before a session means the session is being deleted. ------------------------------------------------------------------------------ PeerID Status LAM SsnRole SsnAge KASent/Rcv ------------------------------------------------------------------------------ 2.2.2.9:0 Operational DU Passive 0000:00:01 6/6 ------------------------------------------------------------------------------ TOTAL: 1 session(s) Found.
[PE1] display mpls ldp lsp LDP LSP Information ------------------------------------------------------------------------------- Flag after Out IF: (I) - LSP Is Only Iterated by RLFA ------------------------------------------------------------------------------- DestAddress/Mask In/OutLabel UpstreamPeer NextHop OutInterface ------------------------------------------------------------------------------- 1.1.1.9/32 3/NULL 2.2.2.9 127.0.0.1 InLoop0 *1.1.1.9/32 Liberal/1024 DS/2.2.2.9 2.2.2.9/32 NULL/3 - 12.1.1.2 Vlanif10 2.2.2.9/32 1024/3 2.2.2.9 12.1.1.2 Vlanif10 3.3.3.9/32 NULL/1025 - 12.1.1.2 Vlanif10 3.3.3.9/32 1025/1025 2.2.2.9 12.1.1.2 Vlanif10 ------------------------------------------------------------------------------- TOTAL: 5 Normal LSP(s) Found. TOTAL: 1 Liberal LSP(s) Found. TOTAL: 0 Frr LSP(s) Found. A '*' before an LSP means the LSP is not established A '*' before a Label means the USCB or DSCB is stale A '*' before a UpstreamPeer means the session is stale A '*' before a DS means the session is stale A '*' before a NextHop means the LSP is FRR LSP - Configure VPN instances on PEs and bind the interfaces connected to CEs to the VPN instances.
# Configure PE1.
[PE1] ip vpn-instance vpna [PE1-vpn-instance-vpna] ipv4-family [PE1-vpn-instance-vpna-af-ipv4] route-distinguisher 100:100 [PE1-vpn-instance-vpna-af-ipv4] vpn-target 100:100 export-extcommunity [PE1-vpn-instance-vpna-af-ipv4] vpn-target 100:100 import-extcommunity [PE1-vpn-instance-vpna-af-ipv4] quit [PE1-vpn-instance-vpna] quit [PE1] ip vpn-instance vpnb [PE1-vpn-instance-vpnb] ipv4-family [PE1-vpn-instance-vpnb-af-ipv4] route-distinguisher 300:300 [PE1-vpn-instance-vpnb-af-ipv4] vpn-target 200:200 export-extcommunity [PE1-vpn-instance-vpnb-af-ipv4] vpn-target 200:200 import-extcommunity [PE1-vpn-instance-vpnb-af-ipv4] quit [PE1-vpn-instance-vpnb] quit [PE1] interface vlanif 100 [PE1-Vlanif100] ip binding vpn-instance vpna [PE1-Vlanif100] ip address 10.1.1.1 255.255.255.0 [PE1-Vlanif100] quit [PE1] interface vlanif 101 [PE1-Vlanif101] ip binding vpn-instance vpnb [PE1-Vlanif101] ip address 10.1.1.1 255.255.255.0 [PE1-Vlanif101] quit
# Configure PE2.
[PE2] ip vpn-instance vpna [PE2-vpn-instance-vpna] ipv4-family [PE2-vpn-instance-vpna-af-ipv4] route-distinguisher 200:200 [PE2-vpn-instance-vpna-af-ipv4] vpn-target 100:100 export-extcommunity [PE2-vpn-instance-vpna-af-ipv4] vpn-target 100:100 import-extcommunity [PE2-vpn-instance-vpna-af-ipv4] quit [PE2-vpn-instance-vpna] quit [PE2] ip vpn-instance vpnb [PE2-vpn-instance-vpnb] ipv4-family [PE2-vpn-instance-vpnb-af-ipv4] route-distinguisher 400:400 [PE2-vpn-instance-vpnb-af-ipv4] vpn-target 200:200 export-extcommunity [PE2-vpn-instance-vpnb-af-ipv4] vpn-target 200:200 import-extcommunity [PE2-vpn-instance-vpnb-af-ipv4] quit [PE2-vpn-instance-vpnb] quit [PE2] interface vlanif 100 [PE2-Vlanif100] ip binding vpn-instance vpna [PE2-Vlanif100] ip address 10.2.1.1 255.255.255.0 [PE2-Vlanif100] quit [PE2] interface vlanif 101 [PE2-Vlanif101] ip binding vpn-instance vpnb [PE2-Vlanif101] ip address 10.2.1.1 255.255.255.0 [PE2-Vlanif101] quit
# Assign IP addresses to the interfaces on the CEs according to Figure 1. The configuration procedure is not provided here.
After the configuration is complete, run the display ip vpn-instance verbose command on the PEs to check the configuration of VPN instances. Each PE can ping its connected CE.
PE1 and CE1 are used as an example.
[PE1] display ip vpn-instance verbose Total VPN-Instances configured : 2 Total IPv4 VPN-Instances configured : 2 Total IPv6 VPN-Instances configured : 0 VPN-Instance Name and ID : vpna, 1 Interfaces : Vlanif100 Address family ipv4 Create date : 2014-11-03 02:39:34+00:00 Up time : 0 days, 22 hours, 24 minutes and 53 seconds Route Distinguisher : 100:100 Export VPN Targets : 100:100 Import VPN Targets : 100:100 Label Policy : label per instance Per-Instance Label : 4098 Log Interval : 5 VPN-Instance Name and ID : vpnb, 2 Interfaces : Vlanif101 Address family ipv4 Create date : 2014-11-03 02:39:34+00:00 Up time : 0 days, 22 hours, 24 minutes and 53 seconds Route Distinguisher : 300:300 Export VPN Targets : 200:200 Import VPN Targets : 200:200 Label Policy : label per instance Per-Instance Label : 4098 Log Interval : 5
[PE1] ping -vpn-instance vpna 10.1.1.2 PING 10.1.1.2: 56 data bytes, press CTRL_C to break Reply from 10.1.1.2: bytes=56 Sequence=1 ttl=255 time=5 ms Reply from 10.1.1.2: bytes=56 Sequence=2 ttl=255 time=3 ms Reply from 10.1.1.2: bytes=56 Sequence=3 ttl=255 time=3 ms Reply from 10.1.1.2: bytes=56 Sequence=4 ttl=255 time=3 ms Reply from 10.1.1.2: bytes=56 Sequence=5 ttl=255 time=16 ms --- 10.1.1.2 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 3/6/16 ms - Establish MP-IBGP peer relationships between PEs.
# Configure PE1.
[PE1] bgp 100 [PE1-bgp] peer 3.3.3.9 as-number 100 [PE1-bgp] peer 3.3.3.9 connect-interface loopback0 [PE1-bgp] ipv4-family vpnv4 [PE1-bgp-af-vpnv4] peer 3.3.3.9 enable [PE1-bgp-af-vpnv4] quit [PE1-bgp] ipv4-family vpn-instance vpna [PE1-bgp-vpna] import-route direct [PE1-bgp-vpna] quit [PE1-bgp] ipv4-family vpn-instance vpnb [PE1-bgp-vpnb] import-route direct [PE1-bgp-vpnb] quit [PE1-bgp] quit
# Configure PE2.
[PE2] bgp 100 [PE2-bgp] peer 1.1.1.9 as-number 100 [PE2-bgp] peer 1.1.1.9 connect-interface loopback0 [PE2-bgp] ipv4-family vpnv4 [PE2-bgp-af-vpnv4] peer 1.1.1.9 enable [PE2-bgp-af-vpnv4] quit [PE2-bgp] ipv4-family vpn-instance vpna [PE2-bgp-vpna] import-route direct [PE2-bgp-vpna] quit [PE2-bgp] ipv4-family vpn-instance vpnb [PE2-bgp-vpnb] import-route direct [PE2-bgp-vpnb] quit [PE2-bgp] quit
After the configuration is complete, run the display bgp peer command on the PEs. The command output shows that a BGP peer relationship has been established between the PEs.
[PE1] display bgp peer BGP local router ID : 1.1.1.9 Local AS number : 100 Total number of peers : 1 Peers in established state : 1 Peer V AS MsgRcvd MsgSent OutQ Up/Down State PrefRcv 3.3.3.9 4 100 3 3 0 00:01:08 Established 0
- On CE1, CE2, CE3, and CE4, configure static routes to their connected PEs.
# Configure CE1. The configuration on CE2, CE3, and CE4 is similar to the configuration on CE1 and is not mentioned here.
[CE1] ip route-static 0.0.0.0 0.0.0.0 vlanif 100 10.1.1.1
- Verify the configurations.
Run the display ip routing-table vpn-instance command on the PEs to view the routes to the remote CEs.
The information displayed on PE1 is used as an example.
[PE1] display ip routing-table vpn-instance vpna Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: vpna Destinations : 3 Routes : 3 Destination/Mask Proto Pre Cost Flags NextHop Interface 10.1.1.0/24 Direct 0 0 D 10.1.1.1 Vlanif100 10.1.1.1/32 Direct 0 0 D 127.0.0.1 Vlanif100 10.2.1.0/24 IBGP 255 0 RD 3.3.3.9 Vlanif10[PE1] display ip routing-table vpn-instance vpnb Route Flags: R - relay, D - download to fib, T - to vpn-instance ------------------------------------------------------------------------------ Routing Tables: vpnb Destinations : 3 Routes : 3 Destination/Mask Proto Pre Cost Flags NextHop Interface 10.1.1.0/24 Direct 0 0 D 10.1.1.1 Vlanif101 10.1.1.1/32 Direct 0 0 D 127.0.0.1 Vlanif101 10.2.1.0/24 IBGP 255 0 RD 3.3.3.9 Vlanif10Run the ping 10.2.1.1 command on CE1, and the ping succeeds. Run the display interface command on PE2 to view traffic statistics on GE0/0/1 and GE0/0/3. The command output shows that there are packets passing through GE0/0/1 but no packet passing through GE0/0/3. This indicates that two VPN instances have overlapping address spaces but they are isolated from each other.
Configuration Files
PE1 configuration file
# sysname PE1 # vlan batch 10 100 to 101 # ip vpn-instance vpna ipv4-family route-distinguisher 100:100 vpn-target 100:100 export-extcommunity vpn-target 100:100 import-extcommunity # ip vpn-instance vpnb ipv4-family route-distinguisher 300:300 vpn-target 200:200 export-extcommunity vpn-target 200:200 import-extcommunity # mpls lsr-id 1.1.1.9 mpls # mpls ldp # interface Vlanif10 ip address 12.1.1.1 255.255.255.0 mpls mpls ldp # interface Vlanif100 ip binding vpn-instance vpna ip address 10.1.1.1 255.255.255.0 # interface Vlanif101 ip binding vpn-instance vpnb ip address 10.1.1.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 100 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 101 # interface LoopBack0 ip address 1.1.1.9 255.255.255.255 # bgp 100 peer 3.3.3.9 as-number 100 peer 3.3.3.9 connect-interface LoopBack0 # ipv4-family unicast undo synchronization peer 3.3.3.9 enable # ipv4-family vpnv4 policy vpn-target peer 3.3.3.9 enable # ipv4-family vpn-instance vpna import-route direct # ipv4-family vpn-instance vpnb import-route direct # ospf 1 area 0.0.0.0 network 1.1.1.9 0.0.0.0 network 12.1.1.0 0.0.0.255 # return
P configuration file
# sysname P # vlan batch 10 20 # mpls lsr-id 2.2.2.9 mpls # mpls ldp # interface Vlanif10 ip address 12.1.1.2 255.255.255.0 mpls mpls ldp # interface Vlanif20 ip address 23.1.1.1 255.255.255.0 mpls mpls ldp # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 # interface LoopBack0 ip address 2.2.2.9 255.255.255.255 # ospf 1 area 0.0.0.0 network 2.2.2.9 0.0.0.0 network 12.1.1.0 0.0.0.255 network 23.1.1.0 0.0.0.255 # return
PE2 configuration file
# sysname PE2 # vlan batch 20 100 to 101 # ip vpn-instance vpna ipv4-family route-distinguisher 200:200 vpn-target 100:100 export-extcommunity vpn-target 100:100 import-extcommunity # ip vpn-instance vpnb ipv4-family route-distinguisher 400:400 vpn-target 200:200 export-extcommunity vpn-target 200:200 import-extcommunity # mpls lsr-id 3.3.3.9 mpls # mpls ldp # interface Vlanif20 ip address 23.1.1.2 255.255.255.0 mpls mpls ldp # interface Vlanif100 ip binding vpn-instance vpna ip address 10.2.1.1 255.255.255.0 # interface Vlanif101 ip binding vpn-instance vpnb ip address 10.2.1.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 20 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 101 # interface LoopBack0 ip address 3.3.3.9 255.255.255.255 # bgp 100 peer 1.1.1.9 as-number 100 peer 1.1.1.9 connect-interface LoopBack0 # ipv4-family unicast undo synchronization peer 1.1.1.9 enable # ipv4-family vpnv4 policy vpn-target peer 1.1.1.9 enable # ipv4-family vpn-instance vpna import-route direct # ipv4-family vpn-instance vpnb import-route direct # ospf 1 area 0.0.0.0 network 3.3.3.9 0.0.0.0 network 23.1.1.0 0.0.0.255 # return
CE1 configuration file
# sysname CE1 # vlan batch 100 # interface Vlanif100 ip address 10.1.1.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 # ip route-static 0.0.0.0 0.0.0.0 Vlanif100 10.1.1.1 # return
CE2 configuration file
# sysname CE2 # vlan batch 100 # interface Vlanif100 ip address 10.2.1.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 100 # ip route-static 0.0.0.0 0.0.0.0 Vlanif100 10.2.1.1 # return
CE3 configuration file
# sysname CE3 # vlan batch 101 # interface Vlanif101 ip address 10.1.1.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 101 # ip route-static 0.0.0.0 0.0.0.0 Vlanif101 10.1.1.1 # return
CE4 configuration file
# sysname CE4 # vlan batch 101 # interface Vlanif101 ip address 10.2.1.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 101 # ip route-static 0.0.0.0 0.0.0.0 Vlanif101 10.2.1.1 # return