Configuring MAC Address Flapping Prevention to Block User Attacks
When you deploy a Layer 2 network, you can configure MAC address flapping prevention to block attacks from unauthorized users.
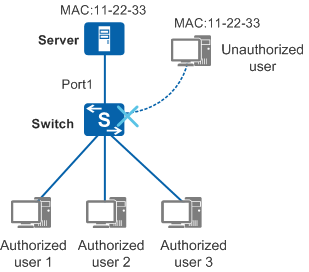
In Figure 1, employees of an enterprise need to access the server connected to Port1 of the switch. If an unauthorized user sends packets using the server's MAC address as the source MAC address, the server's MAC address is learned on another interface of the switch. Subsequently, packets sent by employees to the server are sent to the unauthorized user. As a result, the unauthorized user may intercept data and prevent employees from accessing the server. To prevent unauthorized users from using the server's MAC address to attack the switch, set a higher MAC address learning priority for the interface connected to the server than the interfaces connected to unauthorized users. In this case, MAC address flapping will not occur if unauthorized users attack the switch.