Example for Configuring MAC Address Flapping Prevention
Networking Requirements
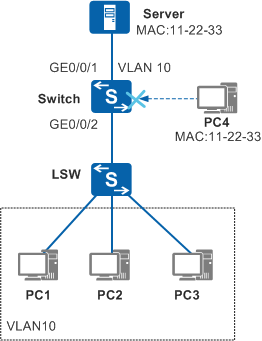
In Figure 1, employees of an enterprise need to visit the server connected to a switch interface. If an unauthorized user uses the server's MAC address as the source MAC address to send packets to another interface, the server's MAC address is learned on the interface. Subsequently, packets sent from employees to the server are forwarded to the unauthorized user. As a result, employees cannot access the server, and data may be intercepted by the unauthorized user.
MAC address flapping prevention can be configured to protect the server against attacks from unauthorized users.
Configuration Roadmap
The configuration roadmap is as follows:
Create a VLAN and add interfaces to the VLAN to implement Layer 2 forwarding.
Configure MAC address flapping prevention on the server-facing interface.
Procedure
- Create a VLAN and add interfaces to the VLAN.
# Add GigabitEthernet0/0/1 and GigabitEthernet0/0/2 to VLAN 10.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan 10 [Switch-vlan10] quit [Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type trunk [Switch-GigabitEthernet0/0/2] port trunk allow-pass vlan 10 [Switch-GigabitEthernet0/0/2] quit [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type hybrid [Switch-GigabitEthernet0/0/1] port hybrid pvid vlan 10 [Switch-GigabitEthernet0/0/1] port hybrid untagged vlan 10
- Set the MAC address learning priority of GigabitEthernet0/0/1 to 2.
[Switch-GigabitEthernet0/0/1] mac-learning priority 2 [Switch-GigabitEthernet0/0/1] quit
- Verify the configuration.
# Run the display current-configuration command in any view to check whether the MAC address learning priority is set correctly.
[Switch] display current-configuration interface gigabitethernet 0/0/1 # interface GigabitEthernet0/0/1 port link-type hybrid port hybrid pvid vlan 10 port hybrid untagged vlan 10 mac-learning priority 2 # return
Configuration Files
Switch configuration file
# sysname Switch # vlan batch 10 # interface GigabitEthernet0/0/1 port link-type hybrid port hybrid pvid vlan 10 port hybrid untagged vlan 10 mac-learning priority 2 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 10 # return