Understanding MPAC
On an enterprise network shown in Figure 1, user-side interfaces need to send a large number of packets to the CPUs of network devices. Some packets are attack packets targeting at CPUs.
Packets from user-side interfaces have two types of impact on network devices:
- Excess packets cause a high CPU usage and degrade CPU performance. Therefore, services cannot be processed in a timely manner.
- Malicious attack packets cause a system breakdown.
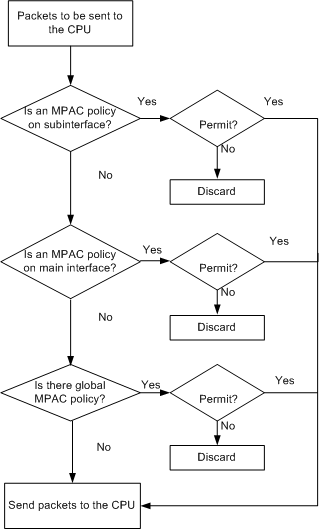
An MPAC policy can be configured on subinterfaces, main
interfaces, or globally to prevent CPU resource exhaustion and ensure
nonstop network operations. The MPAC policy contains the rules that
permit or deny the packets of some protocols and the packets with
certain source/destination addresses:
- When protocol packets match the policy in which the rule is permit, the packets are sent to the CPU for processing.
- When protocol packets match the policy in which the rule is deny, the packets are discarded.
- When protocol packets do not match the policy, the packets are sent to the CPU for processing.
Figure 2 shows the packet processing on a device with an MPAC policy configured. The MPAC policy can be configured according to service requirements.