Example for Configuring MPAC
Networking Requirements
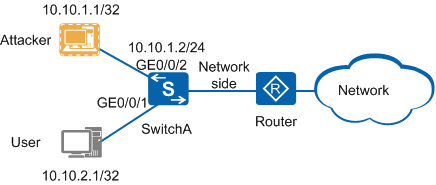
An attacker with a known IP address is detected on an enterprise campus network shown in Figure 1. The attacker sends various TCP/IP packets to attack SwitchA, which may cause SwitchA to break down. To prevent the packets from the attacker from being sent to the CPU, configure an MPAC policy on SwitchA.
Configuration Roadmap
The configuration roadmap is as follows:
Configure the IPv4 MPAC policy test on SwitchA.
Apply the IPv4 MPAC policy test to SwitchA globally.
Apply the IPv4 MPAC policy test to GE0/0/2.
Procedure
- Configure the IPv4 MPAC policy test on SwitchA.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] service-security policy ipv4 test [SwitchA-service-sec-test] rule 10 deny protocol ip source-ip 10.10.1.1 0 [SwitchA-service-sec-test] step 10 [SwitchA-service-sec-test] description rule 10 is deny ip packet which from 10.10.1.1 [SwitchA-service-sec-test] quit
- Apply the IPv4 MPAC policy test to SwitchA globally.
[SwitchA] service-security global-binding ipv4 test - Apply the IPv4 MPAC policy test to GE0/0/2 of SwitchA.
[SwitchA] interface GigabitEthernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] undo portswitch [SwitchA-GigabitEthernet0/0/2] service-security binding ipv4 test [SwitchA-GigabitEthernet0/0/2] quit
- Verify the configuration.
Run the display service-security statistics command to check MPAC information and how many times the IPv4 MPAC rules are matched.
[SwitchA] display service-security statistics ipv4 test Policy Name : test Description : rule 10 is deny ip packet which from 10.10.1.1 Step : 10 rule 10 deny protocol ip source-ip 10.10.1.1 0 (10 times matched)
Configuration Files
SwitchA configuration file
# sysname SwitchA # service-security global-binding ipv4 test # service-security policy ipv4 test description rule 10 is deny ip packet which from 10.10.1.1 step 10 rule 10 deny protocol ip source-ip 10.10.1.1 0 # interface GigabitEthernet0/0/2 undo portswitch service-security binding ipv4 test # return