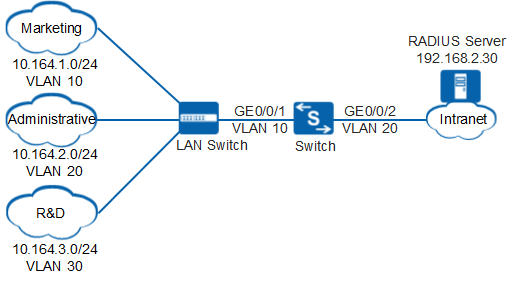
Example for Configuring User Group
Networking Requirements
- Marketing personnel can only access network segment 172.16.104.0/24.
- Administrative personnel can only access network segment 172.16.105.0/24.
- R&D personnel can only access network segment 172.16.106.0/24.
Configuration Roadmap
The configuration roadmap is as follows:
- Create and configure a RADIUS server template, an AAA scheme, and an authentication domain; bind the RADIUS server template and the AAA scheme to the authentication domain. This step implements communication between the Switch and RADIUS server.
- Configure user groups to differentially manage the network access
rights of users.
- Create ACLs.
- Create user groups and bind them to ACLs.
- Enable the user group function.
- Configure 802.1X authentication for users. Only authenticated
users can access the network.
- Enable 802.1X authentication globally and on the interfaces.
- Enable MAC address bypass authentication to authenticate the terminals (such as printers) that cannot install 802.1X authentication client software.

Before configuring this example, ensure that devices can communicate with each other in the network.
Procedure
- Create VLANs and configure the VLAN allowed by the interface
to ensure network communication.
# Create VLAN 10, VLAN 20, VLAN 30, and VLAN 40.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan batch 10 20 30 40
# On the Switch, set GE0/0/1 connecting to users as a trunk interface, and add GE0/0/1 to VLAN 10, VLAN 20, and VLAN 30.
[Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type trunk [Switch-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 20 30 [Switch-GigabitEthernet0/0/1] quit
# On the Switch, set GE0/0/2 connecting to the RADIUS server as an access interface, and add GE0/0/2 to VLAN 40.
[Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] port link-type access [Switch-GigabitEthernet0/0/2] port default vlan 40 [Switch-GigabitEthernet0/0/2] quit
- Create and configure a RADIUS server template, an AAA scheme,
and an authentication domain.
# Create and configure RADIUS server template rd1.
[Switch] radius-server template rd1 [Switch-radius-rd1] radius-server authentication 192.168.2.30 1812 [Switch-radius-rd1] radius-server shared-key cipher Huawei@2012 [Switch-radius-rd1] quit
# Create AAA scheme abc and set the authentication mode to RADIUS.
[Switch] aaa [Switch-aaa] authentication-scheme abc [Switch-aaa-authen-abc] authentication-mode radius [Switch-aaa-authen-abc] quit
# Create authentication domains abc11, abc22, and abc33, and bind the AAA scheme abc and RADIUS server template rd1 to the authentication domains.
[Switch-aaa] domain abc11 [Switch-aaa-domain-abc11] authentication-scheme abc [Switch-aaa-domain-abc11] radius-server rd1 [Switch-aaa-domain-abc11] quit [Switch-aaa] domain abc22 [Switch-aaa-domain-abc22] authentication-scheme abc [Switch-aaa-domain-abc22] radius-server rd1 [Switch-aaa-domain-abc22] quit [Switch-aaa] domain abc33 [Switch-aaa-domain-abc33] authentication-scheme abc [Switch-aaa-domain-abc33] radius-server rd1 [Switch-aaa-domain-abc33] quit [Switch-aaa] quit
- Configure user groups.
# Switch the NAC mode to common mode.
[Switch] undo authentication unified-mode Warning: Switching the authentication mode will take effect after system restart . Some configurations are invalid after the mode is switched. For the invalid co mmands, see the user manual. Save the configuration file and reboot now? [Y/N] y
- By default, the NAC unified mode is used.
- After the unified mode is switched to common mode, you must save the configuration and restart the device to make each function in the new configuration mode take effect.
# Create ACLs.
<Switch> system-view [Switch] acl 3001 [Switch-acl-adv-3001] rule permit ip source 10.164.1.0 0.0.0.255 destination 172.16.104.0 0.0.0.255 [Switch-acl-adv-3001] rule deny ip source 10.164.1.0 0.0.0.255 destination any [Switch-acl-adv-3001] quit [Switch] acl 3002 [Switch-acl-adv-3002] rule permit ip source 10.164.2.0 0.0.0.255 destination 172.16.105.0 0.0.0.255 [Switch-acl-adv-3002] rule deny ip source 10.164.2.0 0.0.0.255 destination any [Switch-acl-adv-3002] quit [Switch] acl 3003 [Switch-acl-adv-3003] rule permit ip source 10.164.3.0 0.0.0.255 destination 172.16.106.0 0.0.0.255 [Switch-acl-adv-3003] rule deny ip source 10.164.3.0 0.0.0.255 destination any [Switch-acl-adv-3003] quit
# Create user groups and bind them to ACLs. Allocate marketing personnel to the user group abc1, administrative personnel to the user group abc2, and R&D personnel to the user group abc3.
[Switch] user-group abc1 [Switch-user-group-abc1] acl-id 3001 [Switch-user-group-abc1] quit [Switch] user-group abc2 [Switch-user-group-abc2] acl-id 3002 [Switch-user-group-abc2] quit [Switch] user-group abc3 [Switch-user-group-abc3] acl-id 3003 [Switch-user-group-abc3] quit
# Enable the user group function.[Switch] user-group abc1 enable [Switch] user-group abc2 enable [Switch] user-group abc3 enable
# Bind user groups to authentication domains. The marketing personnel are authenticated in the authentication domain abc11, administrative personnel in the authentication domain abc22, and R&D personnel in the authentication domain abc33.
[Switch] aaa [Switch-aaa] domain abc11 [Switch-aaa-domain-abc11] user-group abc1 [Switch-aaa-domain-abc11] quit [Switch-aaa] domain abc22 [Switch-aaa-domain-abc22] user-group abc2 [Switch-aaa-domain-abc22] quit [Switch-aaa] domain abc33 [Switch-aaa-domain-abc33] user-group abc3 [Switch-aaa-domain-abc33] quit [Switch-aaa] quit
- Configure 802.1X authentication.
# Enable 802.1X authentication globally and on interfaces.
[Switch] dot1x enable [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] dot1x enable
# Configure MAC address bypass authentication.
[Switch-GigabitEthernet0/0/1] dot1x mac-bypass [Switch-GigabitEthernet0/0/1] quit [Switch] quit
- Verify the configuration.
- Run the display user-group, display domain name, and display dot1x commands to check the configured user group, authentication domain, and 802.1X authentication information.
- When an administrative user A (user name userA@abc22) accesses the network, the Switch authenticates the user in the domain abc22 after receiving the authentication request. The authentication domain abc22 is bound to the user group abc2, so user A is granted the network access rights of the user group abc2. After accessing the network, user A can only access network segment 172.16.105.0/24. R&D personnel can only access 172.16.106.0/24 and marketing personnel can only access 172.16.104.0/24.
Configuration File
Switch configuration file
# sysname Switch # vlan batch 10 20 30 40 undo authentication unified-mode # dot1x enable # radius-server template rd1 radius-server shared-key cipher %^%#t67cDelRvAQg;*"4@P/3~q_31Sn{ST\V8'Ci633)%^%# radius-server authentication 192.168.2.30 1812 weight 80 # acl number 3001 rule 5 permit ip source 10.164.1.0 0.0.0.255 destination 172.16.104.0 0.0.0.255 rule 10 deny ip source 10.164.1.0 0.0.0.255 acl number 3002 rule 5 permit ip source 10.164.2.0 0.0.0.255 destination 172.16.105.0 0.0.0.255 rule 10 deny ip source 10.164.2.0 0.0.0.255 acl number 3003 rule 5 permit ip source 10.164.3.0 0.0.0.255 destination 172.16.106.0 0.0.0.255 rule 10 deny ip source 10.164.3.0 0.0.0.255 # aaa authentication-scheme abc authentication-mode radius domain abc11 authentication-scheme abc radius-server rd1 user-group abc1 domain abc22 authentication-scheme abc radius-server rd1 user-group abc2 domain abc33 authentication-scheme abc radius-server rd1 user-group abc3 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 10 20 30 dot1x mac-bypass # interface GigabitEthernet0/0/2 port link-type access port default vlan 40 # user-group abc1 acl-id 3001 user-group abc1 enable # user-group abc2 acl-id 3002 user-group abc2 enable # user-group abc3 acl-id 3003 user-group abc3 enable # return