Application Scenarios for NAC
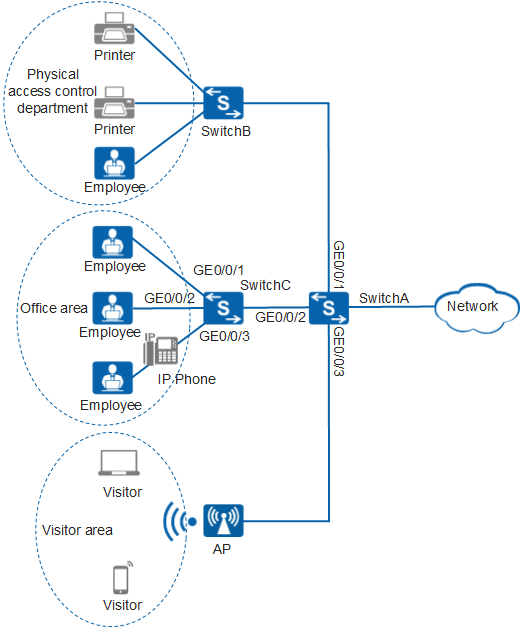
On the network shown in Figure 1, the physical access control department of an enterprise is connected to SwitchA through SwitchB, the office area is connected to SwitchA through SwitchC, and the visitor area is connected to SwitchA through an AP. To ensure security of the enterprise intranet, network access of the users needs to be controlled. Only the users who pass authentication are authorized to access specified network resources.
In the physical access control department, there are terminals of multiple types and the number of printers is greatly more than that of employees. Therefore, deploy 802.1X authentication and MAC address authentication (triggered first) on GE0/0/1 of SwitchA, and configure the user access mode to multi-authen.
The office area has high security requirements. Therefore, deploy 802.1X authentication on SwitchC's GE0/0/1 and GE0/0/2 connected only to PCs, and configure the user access mode to single-terminal. At the same time, deploy 802.1X authentication and MAC address authentication on GE0/0/3 connected to IP phones and PCs, and configure the user access mode to single-voice-with-data.
In the visitor area, users move frequently and have low network access rights. Therefore, deploy Portal authentication on GE0/0/3 of SwitchA, and configure the user access mode to multi-share.