Logout of MAC Address Authentication Users
When users go offline but the access device and RADIUS server do not detect that the offline events, the following problems may occur:
- The RADIUS server still performs accounting for the users, causing incorrect accounting.
- Unauthorized users may spoof IP addresses and MAC addresses of authorized users to access the network.
- If there are many offline users, these users are still counted as access users of the device. As a result, other users may fail to access the network.
The Access Device Controls User Logout
The access device controls user logout in either of the following ways:- Run the cut access-user command to force a user to go offline.
- Configure user detection to check whether a user is online. If the user does not respond within a specified period, the access device considers the user to be offline and deletes the user entry.
Figure 1 User logout detection process
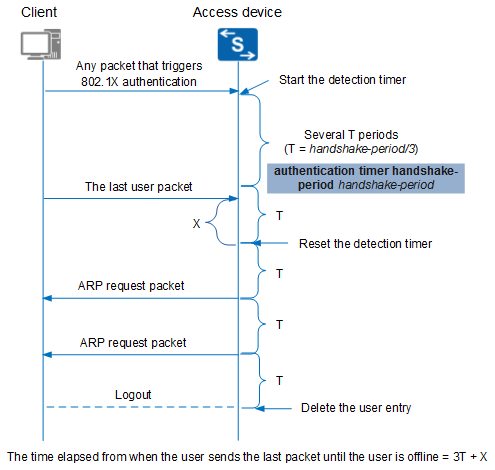
Assume that the handshake period of a user is 3T, which can be set by running the authentication timer handshake-period handshake-period command. Here, T=handshake-period/3.
- The user sends any packet to trigger MAC address authentication, and the detection timer starts.
- Within several T periods, the access device receives traffic from the client and the user keeps online.
- The user sends the last packet. When the current T period expires, the access device determines that the user is online because traffic is still received from the client and resets the detection timer.
- The access device does not receive traffic from the client within a T period, and sends the first ARP request packet. The client does not respond.
- The access device does not receive traffic from the client within another T period, and sends the second ARP request packet. The client does not respond.
- The access device does not receive traffic from the client within a third T period. The access device determines that ARP probing fails and deletes the user entry.
The RADIUS Server Forces a User to Log Out
The RADIUS server controls user logout in either of the following methods:
- Sends a Disconnect Message (DM) to an access device to force a user to go offline.
- Uses the standard RADIUS attributes Session-Timeout and Termination-Action. The Session-Timeout attribute specifies the online duration timer of user. The value of Termination-Action is set to 0, indicating that the user is disconnected by the RADIUS server when the online duration timer expires.