Understanding ECA
Basic Concepts of ECA
Intelligent Awareness Engine (IAE)
An IAE is an integrated content security service processing framework and a set of security features or components. On a switch, the IAE identifies applications, detects encrypted traffic, and works with the big data security analytics function of the CIS server to implement security protection.
SA
SA serves the following purposes:- Identify whether traffic of an application is encrypted, obtain application information of the traffic, and collect and display statistics on the traffic through the application identification signature database (SA-SDB) embedded in the switches. (If traffic is encrypted, only the protocol type, for example, HTTPS, can be identified.) Therefore, the SA-SDB must be updated in a timely manner to improve the SA capability of switches.
- Identify application-layer information in a packet. The application-layer information is vital for generating metadata and analyzing encrypted traffic.
Encrypted traffic identification
If traffic of an application is identified as encrypted, the encrypted traffic needs to be further analyzed to extract the following encrypted traffic features without decrypting the traffic: TLS information (cipher suite, extended fields, and server-returned certificate), TCP information (byte distribution, packet length change, and interval between received data packets), DNS information (number of returned IP packets and requested IP domain names), and other traffic features.
ECA traffic probe
The traffic probe is an information collector that selectively collects network-, transmission-, and application-layer information from traffic. The ECA traffic probe is responsible for collecting encrypted traffic features extracted through SA and encrypted traffic identification, generating metadata using the extracted information, and sending the metadata to the CIS server using the configured parameters for the interconnection between the switch and CIS server.
CIS server
The CIS server establishes a threat detection model using big data analytics and machine learning to analyze the metadata reported by switches and identify abnormal traffic and behavior. There may be differences between normal and malicious encrypted traffic in terms of the encryption algorithm, byte distribution, data packet time sequence, and other aspects. These differences can be extracted by the CIS server using the machine learning algorithm model to distinguish between normal encrypted traffic and malicious encrypted traffic.
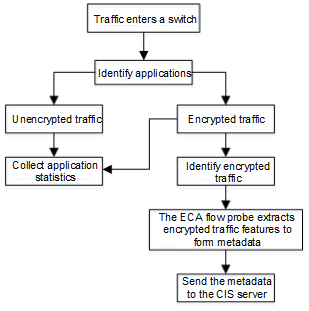
ECA Implementation
As shown in Figure 1, after network traffic enters the switch, the switch distinguishes between encrypted traffic and unencrypted traffic by obtaining and collecting statistics on application information of the traffic using SA. The switch then further identifies the encrypted traffic by extracting encrypted traffic features through the ECA traffic probe and sending the features to the CIS server for malicious traffic detection.