Application Scenarios for Port Security
Port security usually applies to the following scenarios:
- An access switch configured with port security can defend against attacks initiated by an unauthorized user using another interface.
- An aggregation switch configured with port security can limit the number of access users.
Configuring Port Security at the Access Layer
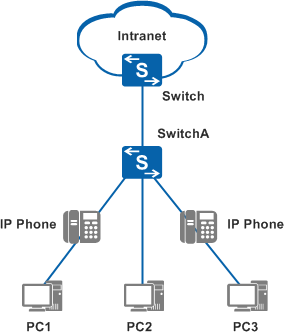
In Figure 1, PC1 and PC3 connect to SwitchA through IP phones, and PC2 directly connects to SwitchA. To ensure security of the access switch and defend against attacks from unauthorized users, configure port security on the interface of SwitchA.
- If access users frequently change location, you can configure port security to convert dynamic MAC addresses into dynamic secure MAC addresses. This ensures that bound MAC address entries are deleted immediately when users change location.
- If access users seldom change location, you can configure port security to convert dynamic MAC addresses into sticky MAC addresses. This ensures that bound MAC address entries will not be lost after a device is reset.
- If a few access users seldom change location, you can configure static secure MAC addresses.
Configuring Port Security at the Aggregation Layer
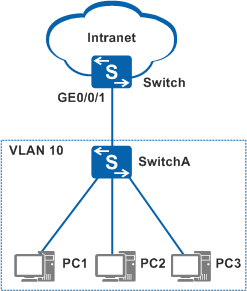
In Figure 2, multiple PCs communicate with the Switch (an aggregation switch) through SwitchA on a tree network. To ensure security of the aggregation switch and limit the number of access users, configure port security on the aggregation switch and set the maximum number of secure MAC addresses.