Overview of MQC
Modular QoS Command-Line Interface (MQC) allows you to classify packets based on packet characteristics and specify the same service for packets of the same type. This allows different types of packets to be provided with differentiated services.
As more services are deployed on a network, service deployment becomes increasingly complex because traffic of different services or users requires differentiated services. Using MQC configuration, you can classify network traffic in a fine-grained way and specify the services provided to different types of traffic according to your needs. MQC enhances serviceability of your network.
MQC Entities
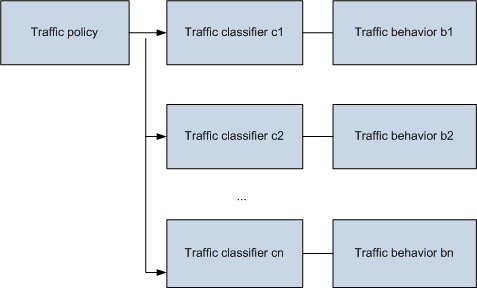
MQC involves three entities: traffic classifier, traffic behavior, and traffic policy.
Traffic classifier
- Name of a traffic classifier
- Traffic classification rule
- Relationship between multiple traffic classification rules in a traffic classifier
Type |
Traffic Classification Rule |
|---|---|
Layer 2 rule |
|
Layer 3 rule |
|
Basic ACL6 rule |
Matching fields in ACL6 2000 to ACL6 2999 |
Advanced ACL6 rule |
Matching fields in ACL6 3000 to ACL6 3999 |
User-defined ACL rule |
Matching fields in ACL 5000 to ACL 5999 |
OR: A packet matches a traffic classifier if it matches one of the rules.
AND: If a traffic classifier contains ACL rules, a packet matches the traffic classifier only if it matches one ACL rule and all the non-ACL rules. If a traffic classifier does not contain ACL rules, a packet matches the traffic classifier only if it matches all the rules in the classifier.
- ACL rules:
- Matching ACL 3000
- Matching ACL 3001
- Non-ACL rules:
- Matching packets tagged with VLAN 10
- Matching packets with the inbound interface being GE0/0/1
If the relationship between rules in traffic classifier c1 is OR, a packet matches traffic classifier c1 if it meets any of the preceding rules.
If the relationship between rules in traffic classifier c1 is AND, a packet matches traffic classifier c1 only when it meets the preceding rules: The VLAN ID is 10, the inbound interface is GE0/0/1, and ACL 3000 or 3001 is matched.
Traffic behavior
- Name of a traffic behavior
- Action in a traffic behavior
- When conflicting actions are defined in the traffic behavior view, the system reports an error, and the command fails to be executed.
- When a traffic policy is applied, the system reports an error, and the traffic policy fails to be applied.
Traffic policy
- Name of a traffic policy
- Association between a traffic classifier and traffic behavior, which specify the actions to be performed for packets matching a traffic classifier
- View in which a traffic policy is applied, for example, interface view, VLAN view, or system view
- Direction in which a traffic policy is applied: When applying a traffic policy, you can specify the inbound or outbound parameter to implement policy control on incoming or outgoing packets.
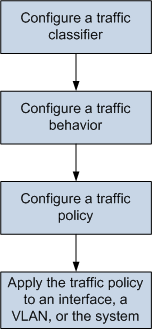
MQC Configuration Process
Configure a traffic classifier. The traffic classifier defines a group of matching rules to classify packets and is the basis for providing differentiated services.
Configure a traffic behavior. The traffic behavior defines a flow control or resource allocation action for packets matching traffic classification rules.
Configure a traffic policy. Create a traffic policy and bind specified traffic classifiers and traffic behaviors to it.
Apply a traffic policy. Apply the traffic policy to the system, an interface, or a VLAN.