Example for Configuring IPv6 RA Guard
Networking Requirements
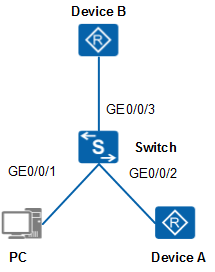
In Figure 1, GE0/0/1, GE0/0/2, and GE0/0/3 on the switch are connected to the PC, Device A, and Device B respectively. To prevent RA attacks, IPv6 RA guard needs to be configured on the three interfaces.
- GE0/0/1 is connected to a PC, so the RA messages received by GE0/0/1 can be discarded immediately.
- GE0/0/2 is connected to Device A, which is a router, so the RA messages received by GE0/0/2 can be forwarded immediately.
- GE0/0/3 is connected to Device B, which is an unknown device. You need to configure an IPv6 RA guard policy on GE0/0/3 to filter the RA messages received by GE0/0/3.
Procedure
- Set the interface role of GE0/0/1 as a host interface.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] nd raguard role host [Switch-GigabitEthernet0/0/1] quit
- Set the interface role of GE0/0/2 as a router interface.
[Switch] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] nd raguard role router [Switch-GigabitEthernet0/0/2] quit
- Create and apply the IPv6 RA guard policy p1 to GE0/0/3 to allow GE0/0/3 to forward only the RA messages in which the IPv6 prefix is fc00:1::/64, the M flag is set to 1, and the O flag is set to 1.
[Switch] acl ipv6 2000 [Switch-acl6-basic-2000] rule 1 permit source fc00:1:: 64 [Switch-acl6-basic-2000] quit [Switch] nd raguard policy p1 [Switch-nd-raguard-policy-p1] if-match prefix acl 2000 [Switch-nd-raguard-policy-p1] managed-address-flag on [Switch-nd-raguard-policy-p1] other-config-flag on [Switch-nd-raguard-policy-p1] quit [Switch] interface gigabitethernet 0/0/3 [Switch-GigabitEthernet0/0/3] nd raguard attach-policy p1 [Switch-GigabitEthernet0/0/3] quit