Example for Configuring the SAVI Function in a DHCPv6+SLAAC Scenario
Networking Requirements
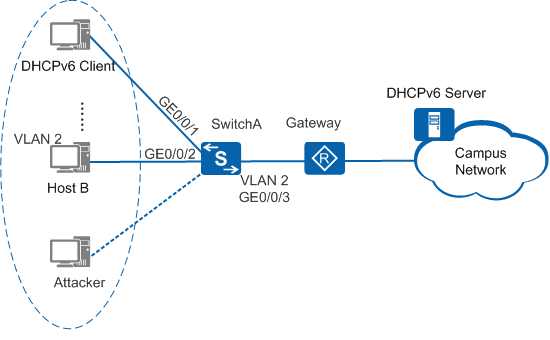
As shown in Figure 1, SwitchA functions as an access device to connect to hosts in an enterprise department. Some hosts in the department obtain IPv6 addresses using SLAAC, and other hosts obtain IPv6 addresses using DHCPv6. If an attacker sends a large number of invalid ND protocol packets, invalid DHCPv6 protocol packets, or invalid IPv6 data packets, communication of authorized users may be interrupted, and user accounts and passwords may be embezzled. To prevent these problems, the administrator wants to configure SwitchA to defend against invalid ND protocol packets, invalid DHCPv6 protocol packets, and invalid IPv6 data packets (with invalid source addresses) and provides users with stable services on a secure network.
Configuration Roadmap
The configuration roadmap is as follows:
Configure DHCPv6 snooping so that bindings between address and ports can be generated for validity of the source addresses in DHCPv6 protocol packets and IPv6 data packets.
Configure ND snooping so that bindings between address and ports can be generated for validity of the source addresses in ND protocol packets and IPv6 data packets.
Enable the SAVI function so that the device can check the validity of the source addresses in DHCPv6 protocol packets and ND protocol packets based on the DHCPv6 snooping and ND snooping binding entries and filter out invalid packets.
Enable IP source guard so that the device can check the validity of the source addresses in IPv6 data packets based on the DHCPv6 snooping and ND snooping binding entries and filter out invalid packets.
Procedure
- Enable the SAVI function.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] savi enable
- Create VLAN 2.
[SwitchA] vlan batch 2 - Add GE0/0/1, GE0/0/2, and GE0/0/3 to VLAN 2.
[SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type access [SwitchA-GigabitEthernet0/0/1] port default vlan 2 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] port link-type access [SwitchA-GigabitEthernet0/0/2] port default vlan 2 [SwitchA-GigabitEthernet0/0/2] quit [SwitchA] interface gigabitethernet 0/0/3 [SwitchA-GigabitEthernet0/0/3] port link-type trunk [SwitchA-GigabitEthernet0/0/3] port trunk allow-pass vlan 2 [SwitchA-GigabitEthernet0/0/3] quit
- Configure DHCPv6 snooping.
# Enable DHCPv6 snooping globally.
[SwitchA] dhcp enable [SwitchA] dhcp snooping enable
# Enable DHCPv6 snooping for VLAN 2.
[SwitchA] vlan 2 [SwitchA-vlan2] dhcp snooping enable
# Enable DHCPv6 protocol packet validity check against the DHCPv6 snooping binding table in VLAN 2.
[SwitchA-vlan2] dhcp snooping check dhcp-request enable [SwitchA-vlan2] quit
# Configure GE0/0/3 connecting to the DHCP server as a trusted interface.
[SwitchA] interface gigabitethernet 0/0/3 [SwitchA-GigabitEthernet0/0/3] dhcp snooping trusted [SwitchA-GigabitEthernet0/0/3] quit
- Configure ND snooping.
# Enable ND snooping globally.
[SwitchA] nd snooping enable# Enable ND snooping for VLAN 2.
[SwitchA] vlan 2 [SwitchA-vlan2] nd snooping enable
# Enable validity check for NA and NS packets in VLAN 2.
[SwitchA-vlan2] nd snooping check na enable [SwitchA-vlan2] nd snooping check ns enable [SwitchA-vlan2] quit
# Configure GE0/0/3 connecting to the ND server as a trusted interface.
[SwitchA] interface gigabitethernet 0/0/3 [SwitchA-GigabitEthernet0/0/3] nd snooping trusted [SwitchA-GigabitEthernet0/0/3] quit
- Enable IP source guard for VLAN 2.
[SwitchA] vlan 2 [SwitchA-vlan2] ip source check user-bind enable [SwitchA-vlan2] quit
- Verify the configuration.
# Run the display this command in the system view to verify that the SAVI function, DHCPv6 snooping, and ND snooping are enabled globally.
[SwitchA] display this ... # dhcp enable # dhcp snooping enable # nd snooping enable savi enable # ...# Run the display this command in the VLAN view. The command output shows that DHCPv6 snooping, DHCPv6 protocol packet validity check against the DHCPv6 snooping binding table, ND snooping, ND protocol packet validity check, and IP source guard have been enabled in VLAN 2.[SwitchA] vlan 2[SwitchA-vlan2] display this # vlan 2 dhcp snooping enable dhcp snooping check dhcp-request enable nd snooping enable nd snooping check ns enable nd snooping check na enable ipv4 source check user-bind enable ipv6 source check user-bind enable # return
[SwitchA-vlan2] quit# Run the display this command in the interface view to verify that GE0/0/3 is configured as the DHCP snooping trusted interface and the ND snooping trusted interface.[SwitchA] interface gigabitethernet 0/0/3
[SwitchA-GigabitEthernet0/0/3] display this # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 2 dhcp snooping trusted nd snooping trusted # return
Configuration Files
SwitchA configuration file
# sysname SwitchA # vlan batch 2 # dhcp enable # dhcp snooping enable # nd snooping enable savi enable # vlan 2 dhcp snooping enable dhcp snooping check dhcp-request enable nd snooping enable nd snooping check ns enable nd snooping check na enable ipv4 source check user-bind enable ipv6 source check user-bind enable # interface GigabitEthernet0/0/1 port link-type access port default vlan 2 # interface GigabitEthernet0/0/2 port link-type access port default vlan 2 # interface GigabitEthernet0/0/3 port link-type trunk port trunk allow-pass vlan 2 dhcp snooping trusted nd snooping trusted # return