Configuring Switches to Send and Receive Flush Packets
Context
When link switching occurs in a Smart Link group, existing forwarding entries no longer apply to the new topology. MAC address entries and ARP entries on the entire network need to be updated. Therefore, the Smart Link group needs to send Flush packets to notify other devices to update their MAC address entries and ARP entries. Because manufacturers define different Flush packet formats, the Flush packets described in this document are used for intercommunication only between Huawei switches. The remote device must be configured to receive Flush packets.
An interface can receive Flush packets only when the control VLAN ID is configured on the interface and the interface is added to the control VLAN.
You do not need to configure all interfaces on a switch to receive Flush packets from the specified control VLAN. This function needs to be configured only on interfaces on the primary and backup links connected to the destination device.
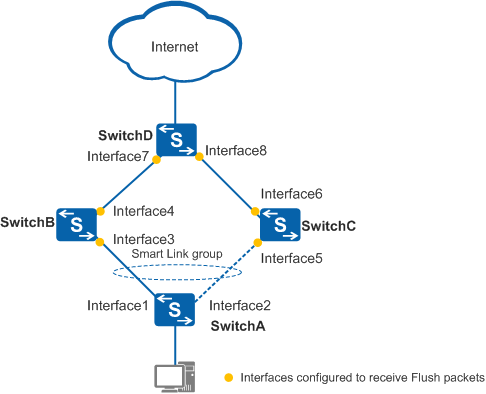
In Figure 1, Smart Link is configured on SwitchA. Interface3 and Interface4 of SwitchB, Interface5 and Interface6 of SwitchC, and Interface7 and Interface8 of SwitchD need to be configured to receive Flush packets.

If interfaces are not configured to send and receive Flush packets, a Smart Link group uses the aging mechanism to update MAC address entries and ARP entries, causing slow convergence. It is recommended that you enable interfaces to send and receive Flush packets when configuring a Smart Link group, which speeds up network convergence.
Procedure
- Enabling the Smart Link group on SwitchA to send Flush packets
Run system-view
The system view is displayed.
Run smart-link group group-id
The Smart Link group view is displayed.
Run flush send control-vlan vlan-id [ password { simple | sha } password ]
The Smart Link group is enabled to send Flush packets, and the encryption mode, control VLAN ID, and password in Flush packets are set. The VLAN ID specified by vlan-id must already exist on the switch. If the specified VLAN ID does not exist, Flush packets cannot be sent.
The encryption mode, control VLAN ID, and password configured for Flush packets sent by a switch must be the same as those configured for receiving Flush packets on the remote device.

The control VLAN cannot be a VLAN mapped to a VLAN-based Spanning Tree (VBST) dynamic instance.
The control VLAN must be in the protected instance list configured by the protected-vlan reference-instance command.
This command does not add member interfaces of the Smart Link group to the control VLAN. You must configure the member interfaces to allow packets of the control VLAN to pass through.
To improve security, use SHA as the authentication algorithm for Smart Link.
- Configuring interfaces on active and standby links of SwitchB, SwitchC, and SwitchD to receive Flush packets
Run system-view
The system view is displayed.
Run interface interface-type interface-number
The interface view is displayed.
Run smart-link flush receive control-vlan { { vlan-id } &<1-10> [ password { simple | sha } password ] | all }
The interface is enabled to receive Flush packets, and the encryption mode, control VLAN ID, and password in received Flush packets are configured.
The password is optional. If no password is specified, no password is used for authentication. If the control VLAN ID is changed, the password must be reconfigured.
The encryption mode, control VLAN ID, and password configured on the device that sends Flush packets must be the same as those configured on the device that receives Flush packets.

A maximum of 256 control VLANs can be configured on an interface for receiving Flush packets.
For security purposes, you are advised to use SHA as the authentication algorithm for Smart Link.
You can run the smart-link flush receive password { simple | sha } password command in the system view to encrypt a password to Flush packets on all interfaces of a control VLAN.
The password configured in a control VLAN on an interface that is enabled to receive flush packets takes precedence over the password configured globally. If no password is configured on an interface, the password configured globally is used.
Run stp disable
STP is disabled on the interface.