Example for Configuring a Switch to Communicate with an NMS Through SNMPv2c
Networking Requirements
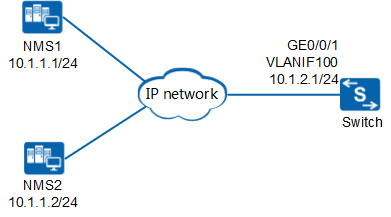
In the network shown in Figure 1, NMS1 and NMS2 manage devices on the network. The network is large and secure but the service traffic volume on the network is high. Therefore, devices on the network use SNMPv2c to communicate with the NMSs. A new switch is deployed on the network and needs to be managed by NMS2.
Users want to manage the switch using existing network resources and hope that faults on the switch can be quickly identified and rectified. To meet service requirements, NMS2 must manage all MIB objects on the switch except RMON objects.
Configuration Roadmap
Because the network is large and secure but the service traffic volume on the network is high, the new switch uses SNMPv2c. To reduce loads on the NMSs, configure NMS2 to manage the switch and NMS1 not to manage the switch.
The configuration roadmap is as follows:
Configure the SNMP version on the switch to SNMPv2c.
Configure the access right to enable NMS2 to manage all MIB objects on the switch except RMON objects.
Configure the inform host for the switch to deliver traps generated on the switch to NMS2. To help quickly identify faults according to trap messages and reduce useless traps, configure the switch to send only the traps of the modules enabled by default.
Configure NMS2.
Procedure
- Configure an IP address for an interface of the switch to
provide a reachable route between the NMS and the Switch.
# Configure an IP address for an interface of the switch according to Figure 1.
<HUAWEI> system-view [HUAWEI] sysname Switch [Switch] vlan 100 [Switch-vlan100] quit [Switch] interface gigabitethernet 0/0/1 [Switch-GigabitEthernet0/0/1] port link-type hybrid [Switch-GigabitEthernet0/0/1] port hybrid pvid vlan 100 [Switch-GigabitEthernet0/0/1] port hybrid untagged vlan 100 [Switch-GigabitEthernet0/0/1] quit [Switch] interface vlanif 100 [Switch-Vlanif100] ip address 10.1.2.1 24 [Switch-Vlanif100] quit
- Set the SNMP version on the switch to SNMPv2c.
[Switch] snmp-agent sys-info version v2c - Configure the access rights.
# Configure an ACL that allows NMS2 to manage the switch and prevents NMS1 from managing the switch.
[Switch] acl 2001 [Switch-acl-basic-2001] rule 5 permit source 10.1.1.2 0.0.0.0 [Switch-acl-basic-2001] rule 6 deny source 10.1.1.1 0.0.0.0 [Switch-acl-basic-2001] quit
# Configure the MIB view to allow NMS2 to manage all MIB objects on the switch except RMON objects.
[Switch] snmp-agent mib-view excluded allextrmon 1.3.6.1.2.1.16# Configure a community name and reference the ACL and MIB view for the community.
[Switch] snmp-agent community write adminnms2 mib-view allextrmon acl 2001 - Configure the inform host.
[Switch] snmp-agent target-host inform address udp-domain 10.1.1.2 params securityname adminnms2 v2c [Switch] snmp-agent inform timeout 5 resend-times 6 pending 7
- Configure NMS2.
You must set a read-write community name for an NMS running SNMPv2c. For details about the NMS configuration, see the manual of the NMS.

The authentication parameter configuration on the NMS must be the same as that on the switch. Otherwise, the NMS cannot manage the switch. If only the write community name is configured on the device, the read and write community names on the NMS must be the same as the write community name configured on the device.
- Verify the configuration.
After completing the configuration, run the following commands to verify that the configurations have taken effect.
# View the SNMP version.
[Switch] display snmp-agent sys-info version SNMP version running in the system: Polling: SNMPv1:disable, SNMPv2c:enable, SNMPv3:disable Trap : SNMPv1:disable, SNMPv2c:enable, SNMPv3:disable# View the configuration of the target host used to receive traps.
[Switch] display snmp-agent target-host Target-host NO. 1 ----------------------------------------------------------- IP-address : 10.1.1.2 Domain : - Source interface : - VPN instance : - Security name : %^%#uq/!YZfvW4*vf[~C|.:Cl}UqS(vXd#wwqR~5M(rU%%^%# Port : 162 Type : inform Version : v2c Level : No authentication and privacy NMS type : NMS With ext-vb : No -----------------------------------------------------------
Configuration Files
Switch configuration file
# sysname Switch # vlan batch 100 # acl number 2001 rule 5 permit source 10.1.1.2 0 rule 6 deny source 10.1.1.1 0 # interface Vlanif100 ip address 10.1.2.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type hybrid port hybrid pvid vlan 100 port hybrid untagged vlan 100 # snmp-agent snmp-agent local-engineid 800007DB03360102101100 snmp-agent community write cipher %^%#.T|&Whvyf$<Gd"I,wXi5SP_6~Nakk6<<+3H:N-h@aJ6d,l0md%HCeAY8~>X=>xV\JKNAL=124r839v<*%^%# mib-view allextrmon acl 2001 snmp-agent sys-info version v2c v3 snmp-agent target-host inform address udp-domain 10.1.1.2 params securityname cipher %^%#uq/!YZfvW4*vf[~C|.:Cl}UqS(vXd#wwqR~5M(rU%%^%# v2c snmp-agent mib-view excluded allextrmon rmon snmp-agent inform timeout 5 snmp-agent inform resend-times 6 snmp-agent inform pending 7 # return