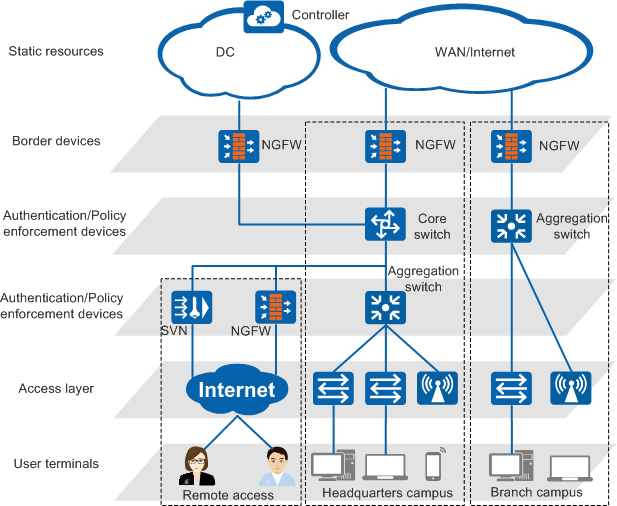
Network Architecture
Figure 1 shows the overall architecture of free mobility.
- User terminals initiate authentication.
- The access layer transparently forwards user traffic at Layer 2.
- Authentication devices authenticate users, and policy enforcement devices control user access rights. An authentication device and a policy enforcement device can be the same physical device or different physical devices.
- Border devices ensure the forwarding priority of specific users at the egress.
- Static resources are server resources that users can access. These resources can be managed as security groups by a controller.
The free mobility solution involves the following key roles:
- Controllers: work with network devices to authenticate users and deliver policies, decoupling service policies from IP addresses. Only Huawei Agile Controller-Campus or iMaster NCE-Campus is supported in the free mobility solution.
- Access devices: authenticate terminals to determine whether to allow the terminals to access the network and control their network access rights. The access devices include switches and firewalls. Only switches are mentioned in this manual.
- Terminals: provide human-machine interfaces for user authentication and resource access. The terminals include PCs, laptops, smartphones, tablets, and dumb terminals.