Example for Configuring URPF
Networking Requirements
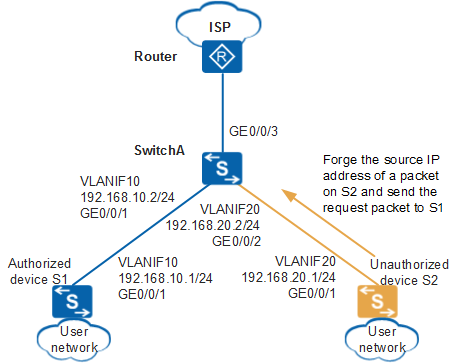
In Figure 1, SwitchA is connected to the Internet Service Provider (ISP) router through GE0/0/3 and connected to user networks through GE0/0/1 and GE0/0/2. The administrator requires that SwitchA defend against source IP address spoofing attacks to prevent unauthorized users from forging source IP addresses to attack authorized users.

SwitchA in this example is the S5720-HI.
Configuration Roadmap
- Configure S1 and S2 to communicate with SwitchA:
- Configure the interface and IP address of SwitchA.
- Configure the interface, IP address, and route of S1.
- Configure the interface, IP address, and route of S2.
- Configure URPF on SwitchA and verify the function:
- Configure traffic statistics collection on S1.
- View traffic statistics collected on S1.
- Forge the source IP address of a packet on S2 and send the request packet to S1.
- View traffic statistics collected on S1.
- Configure URPF on SwitchA.
- Forge the source IP address of a packet on S2 and send the request packet to S1.
- View traffic statistics collected on S1.
Procedure
- Configure S1 and S2 to communicate with SwitchA.
# Configure the interface and IP address of SwitchA.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] vlan batch 10 20 [SwitchA] interface gigabitethernet 0/0/1 [SwitchA-GigabitEthernet0/0/1] port link-type trunk [SwitchA-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [SwitchA-GigabitEthernet0/0/1] undo port trunk allow-pass vlan 1 [SwitchA-GigabitEthernet0/0/1] quit [SwitchA] interface gigabitethernet 0/0/2 [SwitchA-GigabitEthernet0/0/2] port link-type trunk [SwitchA-GigabitEthernet0/0/2] port trunk allow-pass vlan 20 [SwitchA-GigabitEthernet0/0/2] undo port trunk allow-pass vlan 1 [SwitchA-GigabitEthernet0/0/2] quit [SwitchA] interface vlanif 10 [SwitchA-Vlanif10] ip address 192.168.10.2 24 [SwitchA-Vlanif10] quit [SwitchA] interface vlanif 20 [SwitchA-Vlanif20] ip address 192.168.20.2 24 [SwitchA-Vlanif20] quit
# Configure the interface, IP address, and route of S1.
<HUAWEI> system-view [HUAWEI] sysname S1 [S1] vlan batch 10 [S1] interface gigabitethernet 0/0/1 [S1-GigabitEthernet0/0/1] port link-type trunk [S1-GigabitEthernet0/0/1] port trunk allow-pass vlan 10 [S1-GigabitEthernet0/0/1] undo port trunk allow-pass vlan 1 [S1-GigabitEthernet0/0/1] quit [S1] interface vlanif 10 [S1-Vlanif10] ip address 192.168.10.1 24 [S1-Vlanif10] quit [S1] ip route-static 192.168.20.0 24 192.168.10.2
# Configure the interface, IP address, and route of S2.
<HUAWEI> system-view [HUAWEI] sysname S2 [S2] vlan batch 10 [S2] interface gigabitethernet 0/0/1 [S2-GigabitEthernet0/0/1] port link-type trunk [S2-GigabitEthernet0/0/1] port trunk allow-pass vlan 20 [S2-GigabitEthernet0/0/1] undo port trunk allow-pass vlan 1 [S2-GigabitEthernet0/0/1] quit [S2] interface vlanif 20 [S2-Vlanif20] ip address 192.168.20.1 24 [S2-Vlanif20] quit [S2] ip route-static 192.168.10.0 24 192.168.20.2
# Check whether there are reachable routes among S1, S2, and SwitchA. If S1 can successfully ping S2, there are reachable routes among S1, S2, and SwitchA.
[S1] ping 192.168.20.1 PING 192.168.20.1: 56 data bytes, press CTRL_C to break Reply from 192.168.20.1: bytes=56 Sequence=1 ttl=253 time=1 ms Reply from 192.168.20.1: bytes=56 Sequence=2 ttl=253 time=1 ms Reply from 192.168.20.1: bytes=56 Sequence=3 ttl=253 time=1 ms Reply from 192.168.20.1: bytes=56 Sequence=4 ttl=253 time=1 ms Reply from 192.168.20.1: bytes=56 Sequence=5 ttl=253 time=1 ms --- 192.168.20.1 ping statistics --- 5 packet(s) transmitted 5 packet(s) received 0.00% packet loss round-trip min/avg/max = 1/1/1 ms - Configure URPF on SwitchA and verify the function.
# Configure traffic statistics collection on S1.
[S1] acl 3002 [S1-acl-adv-3002] rule permit icmp source 192.168.10.3 0 destination 192.168.10.1 0 //Matches ICMP packets with the source IP address of 192.168.10.3 and destination IP address of 192.168.10.1. [S1-acl-adv-3002] quit [S1] interface gigabitethernet 0/0/1 [S1-GigabitEthernet0/0/1] traffic-statistic inbound acl 3002 //Collects statistics about packets that match ACL 3002 on GE0/0/1. [S1-GigabitEthernet0/0/1] quit
# View initial traffic statistics collected on S1, and no information is displayed.
[S1] display traffic-statistics interface GigabitEthernet 0/0/1 inbound --------------------------------------------------------------------------- Interface GigabitEthernet0/0/1 ACL:3002 Rule:5 matched:0 packets, passed:0 packets, dropped:0 packets# Forge the source IP address of a packet on S2 and send the request packet to S1. In this example, S2 pings S1 with a specified source IP address, but does not receive any response packet from S1.
[S2] ping -a 192.168.10.3 192.168.10.2 Warning: The specified source address is not a local address, the ping command will not check the network connection. PING 192.168.10.2: 56 data bytes, press CTRL_C to break Request time out Request time out Request time out Request time out Request time out --- 192.168.10.2 ping statistics --- 5 packet(s) transmitted 0 packet(s) received 100.00% packet loss# View traffic statistics collected on S1. The statistics show that S1 has received request packets from S2, which is attack packets for S1.
[S1] display traffic-statistics interface GigabitEthernet 0/0/1 inbound --------------------------------------------------------------------------- Interface GigabitEthernet0/0/1 ACL:3002 Rule:5 matched:5 packets, passed:5 packets, dropped:0 packets# Configure URPF on SwitchA.
[SwitchA] interface gigabitethernet 0/0/2 [Switch-GigabitEthernet0/0/2] urpf strict [Switch-GigabitEthernet0/0/2] quit
# S2 pings S1 with a specified source IP address again, but does not receive any response packet from SwitchA.
[S2] ping -a 192.168.10.1 192.168.10.2 Warning: The specified source address is not a local address, the ping command will not check the network connection. PING 192.168.10.2: 56 data bytes, press CTRL_C to break Request time out Request time out Request time out Request time out Request time out --- 192.168.10.2 ping statistics --- 5 packet(s) transmitted 0 packet(s) received 100.00% packet loss# View traffic statistics collected on S1. You can find that attack packets forged on S2 are discarded because URPF is configured on SwitchA. As a result, S1 cannot receive request packets sent by S2.
[S1] display traffic-statistics interface GigabitEthernet 0/0/1 inbound --------------------------------------------------------------------------- Interface GigabitEthernet0/0/1 ACL:3002 Rule:5 matched:5 packets, passed:5 packets, dropped:0 packets
Configuration Files
SwitchA configuration file
# sysname SwitchA # vlan batch 10 20 # interface Vlanif10 ip address 192.168.10.2 255.255.255.0 # interface Vlanif20 ip address 192.168.20.2 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 10 # interface GigabitEthernet0/0/2 port link-type trunk undo port trunk allow-pass vlan 1 port trunk allow-pass vlan 20 urpf strict # return
S1 configuration file
#
sysname S1
#
vlan batch 10
#
acl number 3002
rule 5 permit icmp source 192.168.30.1 0 destination 192.168.10.1 0
#
interface Vlanif10
ip address 192.168.10.1 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 10
traffic-statistic inbound acl 3002
#
ip route-static 192.168.20.0 255.255.255.0 192.168.10.2
#
return
S2 configuration file
#
sysname S2
#
vlan batch 20
#
interface Vlanif20
ip address 192.168.20.1 255.255.255.0
#
interface GigabitEthernet0/0/1
port link-type trunk
undo port trunk allow-pass vlan 1
port trunk allow-pass vlan 20
#
ip route-static 192.168.10.0 255.255.255.0 192.168.20.2
#
return