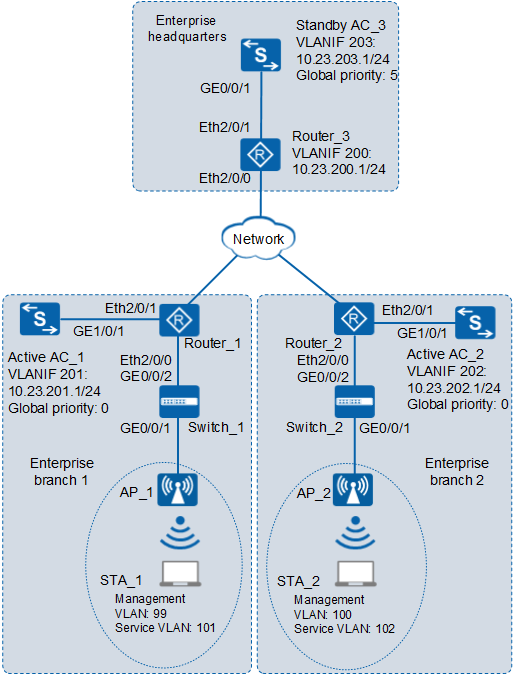
Example for Configuring N+1 Backup (APs and ACs in different network segments)
Configuration Process
You need to configure and maintain WLAN features and functions in different profiles. These WLAN profiles include regulatory domain profile, radio profile, VAP profile, AP system profile, AP wired port profile, WIDS profile, WDS profile, and Mesh profile. When configuring WLAN services, you need to set related parameters in the WLAN profiles and bind the profiles to the AP group or APs. Then the configuration is automatically delivered to and takes effect on the APs. WLAN profiles can reference one another; therefore, you need to know the relationships among the profiles before configuring them. For details about the profile relationships and their basic configuration procedure, see WLAN Service Configuration Procedure.
Networking Requirements
A large enterprise has branches in different areas. ACs are deployed in the branches to manage APs and provide WLAN access and e-mail services. These services require low network reliability and allow temporary service interruption. An AC is required to be a backup of all ACs to reduce cost. In this scenario, the enterprise can deploy a high performance AC at the headquarters as a standby AC to provide backup services for active ACs in the branches.
In Figure 1, AC_1 in branch 1 and AC_2 in branch 2 are both active ACs, and respectively provide services for AP_1 and AP_2. AC_3 in the headquarters serves as the standby AC of AC_1 and AC_2. AC_1 connects to the Network through Router_1 and connects to AP_1 through Router_1 and Switch_1; AC_2 connects to the Network through Router_2 and connects to AP_2 through Router_2 and Switch_2; AC_3 connects to the Network through Router_3. All ACs belong to different network segments. APs and ACs are also located in different network segments. Router_3 functions as a DHCP server to allocate IP addresses to APs and STAs. When the CAPWAP link on AC_1 or AC_2 fails, AC_3 is expected to replace AC_1 or AC_2 to continue serving the APs.
Configuration Roadmap
- Set up connections between each AC and other network devices. Configure Router_3 as a DHCP server to allocate IP addresses to APs and STAs.
- Configure AC_1 and AC_2 as the active ACs of AP_1 and AP_2 respectively, and configure basic WLAN services on AC_1 and AC_2.
- Configure AC_3 as the standby AC and configure basic WLAN services on AC_3. Ensure that service configurations on AC_3 are the same as those on AC_1 and AC_2.
- Configure N+1 backup on the active ACs first and then on the standby AC. When N+1 backup is enabled, all APs are restarted.
Item |
Data |
|---|---|
Management VLAN for APs |
AC_1 (active AC): VLAN 99 |
AC_2 (active AC): VLAN 100 |
|
Service VLAN for STAs |
AC_1 (active AC): VLAN 101 |
AC_2 (active AC): VLAN 102 |
|
DHCP server |
Router_3 functions as the DHCP server for the APs and STAs. STAs' gateway:
APs' gateway:
|
IP address pool for APs |
AP_1: 10.23.99.2 to 10.23.99.254/24 AP_2: 10.23.100.2 to 10.23.100.254/24 |
IP address pool for STAs |
STA_1:10.23.101.2 to 10.23.101.254/24 STA_2:10.23.102.2 to 10.23.102.254/24 |
AP group |
AC_1:
|
AC_2:
|
|
AC_3 (standby AC):
|
|
SSID profile |
AC_1:
|
AC_2:
|
|
AC_3 (standby AC):
|
|
Security profile |
|
AP system profile |
AC_3: ap-system1 and ap-system2 |
Source interface of AC_1 |
VLANIF 201: 10.23.201.1/24 |
Source interface of AC_2 |
VLANIF 202: 10.23.202.1/24 |
Source interface of AC_3 |
VLANIF 203: 10.23.203.1/24 |
AC's global priority |
AC_1: 0 AC_2: 0 AC_3: 5 |
Configuration Notes
- No ACK mechanism is provided for multicast packet transmission on air interfaces. In addition, wireless links are unstable. To ensure stable transmission of multicast packets, they are usually sent at low rates. If a large number of such multicast packets are sent from the network side, the air interfaces may be congested. You are advised to configure multicast packet suppression to reduce impact of a large number of low-rate multicast packets on the wireless network. Exercise caution when configuring the rate limit; otherwise, the multicast services may be affected.
- In direct forwarding mode, you are advised to configure multicast packet suppression on switch interfaces connected to APs.
- In tunnel forwarding mode, you are advised to configure multicast packet suppression in traffic profiles of the AC.
Configure port isolation on the interfaces of the device directly connected to APs. If port isolation is not configured and direct forwarding is used, a large number of unnecessary broadcast packets may be generated in the VLAN, blocking the network and degrading user experience.
In tunnel forwarding mode, the management VLAN and service VLAN cannot be the same. Only packets from the management VLAN are transmitted between the AC and APs. Packets from the service VLAN are not allowed between the AC and APs.
Procedure
- Set the NAC mode to unified on the AC so that users can connect to the network properly.
<HUAWEI> system-view [HUAWEI] authentication unified-mode

If the NAC mode is changed from traditional to unified, the unified mode takes effect after you save the configuration and restart the device.
- Configure the routers, switches, and ACs to ensure communications among them.# On Router_1, create VLAN 99, VLAN 101 and VLAN201. VLAN 99 is used as the management VLAN and VLAN 101 is used as the service VLAN. Add Eth2/0/0 connected to Switch_1 to VLAN 99 and VLAN 101, and Eth2/0/1 connected to AC_1 to VLAN 201. Configure the IP address 10.23.99.1/24 for VLANIF 99, 10.23.101.1/24 for VLANIF 101 and 10.23.201.2/24 for VLANIF 201.
<HUAWEI> system-view [HUAWEI] sysname Router_1 [Router_1] vlan batch 99 101 201 [Router_1] interface ethernet 2/0/0 [Router_1-Ethernet2/0/0] port link-type trunk [Router_1-Ethernet2/0/0] port trunk allow-pass vlan 99 101 [Router_1-Ethernet2/0/0] quit [Router_1] interface ethernet 2/0/1 [Router_1-Ethernet2/0/1] port link-type trunk [Router_1-Ethernet2/0/1] port trunk allow-pass vlan 201 [Router_1-Ethernet2/0/1] quit [Router_1] interface vlanif 99 [Router_1-Vlanif99] ip address 10.23.99.1 255.255.255.0 [Router_1-Vlanif99] quit [Router_1] interface vlanif 101 [Router_1-Vlanif101] ip address 10.23.101.1 255.255.255.0 [Router_1-Vlanif101] quit [Router_1] interface vlanif 201 [Router_1-Vlanif201] ip address 10.23.201.2 255.255.255.0 [Router_1-Vlanif201] quit
# On Router_2, create VLAN 100, VLAN 102 and VLAN 202. VLAN 100 is used as the management VLAN and VLAN 102 is used as the service VLAN. Add Eth2/0/0 connected to Switch_2 to VLAN 100 and VLAN 102, and Eth2/0/1 connected to AC_2 to VLAN 202. Configure the IP address 10.23.100.1/24 for VLANIF 100, 10.23.102.1/24 for VLANIF 102 and 10.23.202.2/24 for VLANIF 202. See Router_1 for the detailed configuration procedure.
# On Router_3, create VLAN 200, VLAN 203, and add Eth2/0/0 connected to the Network to VLAN 200, and Eth2/0/1 connected to AC_3 to VLAN 203. Configure the IP address 10.23.200.1/24 for VLANIF 200. Configure the IP address 10.23.203.2/24 for VLANIF 203. See Router_1 for the detailed configuration procedure.
# On AC_1, create VLAN 101, VLAN 201, and add GE0/0/1 connected to Router_1 to VLAN 201. Configure the IP address 10.23.201.1/24 for VLANIF 201.
<HUAWEI> system-view [HUAWEI] sysname AC_1 [AC_1] vlan batch 101 201 [AC_1] interface gigabitethernet 0/0/1 [AC_1-GigabitEthernet0/0/1] port link-type trunk [AC_1-GigabitEthernet0/0/1] port trunk allow-pass vlan 201 [AC_1-GigabitEthernet0/0/1] quit [AC_1] interface vlanif 201 [AC_1-Vlanif201] ip address 10.23.201.1 255.255.255.0 [AC_1-Vlanif201] quit
# On AC_2, create VLAN 102, VLAN 202, and add GE0/0/1 connected to Router_2 to VLAN 202. Configure the IP address 10.23.202.1/24 for VLANIF 202. See AC_1 for the detailed configuration procedure.
# On AC_3, create VLAN 101, VLAN102, VLAN 203, and add GE0/0/1 connected to Router_3 to VLAN 203. Configure the IP address 10.23.203.1/24 for VLANIF 203. See AC_1 for the detailed configuration procedure.
# On Switch_1, create VLAN 99 and VLAN 101. Add GE0/0/2 connected to AC_1 and GE0/0/1 connected to AP_1 to VLAN 99 and VLAN 101, and the PVID of GE0/0/1 is VLAN 99.
<HUAWEI> system-view [HUAWEI] sysname Switch_1 [Switch_1] vlan batch 99 101 [Switch_1] interface gigabitethernet 0/0/1 [Switch_1-GigabitEthernet0/0/1] port link-type trunk [Switch_1-GigabitEthernet0/0/1] port trunk pvid vlan 99 [Switch_1-GigabitEthernet0/0/1] port trunk allow-pass vlan 99 101 [Switch_1-GigabitEthernet0/0/1] port-isolate enable [Switch_1-GigabitEthernet0/0/1] quit [Switch_1] interface gigabitethernet 0/0/2 [Switch_1-GigabitEthernet0/0/2] port link-type trunk [Switch_1-GigabitEthernet0/0/2] port trunk allow-pass vlan 99 101 [Switch_1-GigabitEthernet0/0/2] quit
# On Switch_2, create VLAN 100 and VLAN 102. Add GE0/0/2 connected to AC_2 and GE0/0/1 connected to AP_2 to VLAN 100 and VLAN 102. See Switch_1 for the detailed configuration procedure.
# Configure reachable routes between AC_1 and AC_3, AP_1 and AC_3, AC_2 and AC_3, and between AP_2 and AC_3. Perform the configurations according to networking requirements. The configuration procedure is not provided here.
# Configure the route between AC_1 and AP_1 with the next hop as Router_1's VLANIF 201.[AC_1] ip route-static 10.23.99.0 24 10.23.201.2
# Configure the route between AC_2 and AP_2 with the next hop as Router_2's VLANIF 202.[AC_2] ip route-static 10.23.101.0 24 10.23.202.2
- Configure a DHCP server to allocate IP addresses to APs and STAs.
# Configure Router_1 as a DHCP relay agent.
[Router_1] dhcp enable [Router_1] interface vlanif 99 [Router_1-Vlanif99] dhcp select relay [Router_1-Vlanif99] dhcp relay server-ip 10.23.200.1 [Router_1-Vlanif99] quit [Router_1] interface vlanif 101 [Router_1-Vlanif101] dhcp select relay [Router_1-Vlanif101] dhcp relay server-ip 10.23.200.1 [Router_1-Vlanif101] quit
# Configure Router_2 as a DHCP relay agent.
[Router_2] dhcp enable [Router_2] interface vlanif 100 [Router_2-Vlanif100] dhcp select relay [Router_2-Vlanif100] dhcp relay server-ip 10.23.200.1 [Router_2-Vlanif100] quit [Router_2] interface vlanif 102 [Router_2-Vlanif102] dhcp select relay [Router_2-Vlanif102] dhcp relay server-ip 10.23.200.1 [Router_2-Vlanif102] quit
# Configure Router_3 as the DHCP server to allocate IP addresses to APs and STAs, and configure the Option 43 field to advertise the IP addresses of AC_1 and AC_3 to AP_1, and to advertise the IP addresses of AC_2 and AC_3 to AP_2. Configure the DHCP server to allocate IP address to AP_1 from the IP address pool ap_1_pool, to AP_2 from ap_2_pool, to STA1 from sta_1_pool, and to STA2 from sta_2_pool.

In this example, AP_1 and AP_2 cannot share an IP address pool; otherwise, AP_1 can discover AC_2 and AP_2 can discover AC_1, which will cause APs unable to connect to the correct AC based on AC priority.
Configure the DNS server as required. The common methods are as follows:- In interface address pool scenarios, run the dhcp server dns-list ip-address &<1-8> command in the VLANIF interface view.
- In global address pool scenarios, run the dns-list ip-address &<1-8> command in the IP address pool view.
[Router_3] dhcp enable [Router_3] ip pool ap_1_pool [Router_3-ip-pool-ap_1_pool] network 10.23.99.0 mask 24 [Router_3-ip-pool-ap_1_pool] gateway-list 10.23.99.1 [Router_3-ip-pool-ap_1_pool] option 43 sub-option 2 ip-address 10.23.201.1 10.23.203.1 [Router_3-ip-pool-ap_1_pool] quit [Router_3] ip pool ap_2_pool [Router_3-ip-pool-ap_2_pool] network 10.23.100.0 mask 24 [Router_3-ip-pool-ap_2_pool] gateway-list 10.23.100.1 [Router_3-ip-pool-ap_2_pool] option 43 sub-option 2 ip-address 10.23.202.1 10.23.203.1 [Router_3-ip-pool-ap_2_pool] quit [Router_3] ip pool sta_1_pool [Router_3-ip-pool-sta_1_pool] network 10.23.101.0 mask 24 [Router_3-ip-pool-sta_1_pool] gateway-list 10.23.101.1 [Router_3-ip-pool-sta_1_pool] quit [Router_3] ip pool sta_2_pool [Router_3-ip-pool-sta_2_pool] network 10.23.102.0 mask 24 [Router_3-ip-pool-sta_2_pool] gateway-list 10.23.102.1 [Router_3-ip-pool-sta_2_pool] quit
- Configure basic WLAN services on AC_1.
- Configure basic WLAN services on AC_2.
# Configure basic parameters for AC_2 according to the configurations of AC_1.
# Configure the source interface of AC_2.
[AC_2] capwap source interface vlanif 202
# Create the AP group ap-group2.
[AC_2] wlan [AC_2-wlan-view] ap-group name ap-group2 [AC_2-wlan-ap-group-ap-group2] quit
# Import the APs offline on the AC and add the APs to the AP group ap-group2. In this example, the AP's MAC address is 60de-4474-9640. Configure a name for the AP based on the AP's deployment location, so that you can know where the AP is located. For example, if the AP with MAC address 60de-4474-9640 is deployed in area 2, name the AP area_2.
[AC_2] wlan [AC_2-wlan-view] ap auth-mode mac-auth [AC_2-wlan-view] ap-id 1 ap-mac 60de-4474-9640 [AC_2-wlan-ap-1] ap-name area_2 [AC_2-wlan-ap-1] ap-group ap-group2 Warning: This operation may cause AP reset. If the country code changes, it will clear channel, power and antenna gain configurati ons of the radio, Whether to continue? [Y/N]:y [AC_2-wlan-ap-1] quit
# Create the security profile wlan-security and set the security policy in the profile.
In this example, the security policy is set to WPA2+PSK+AES and password to a1234567. In actual situations, the security policy must be configured according to service requirements.
[AC_2-wlan-view] security-profile name wlan-security [AC_2-wlan-sec-prof-wlan-security] security wpa2 psk pass-phrase a1234567 aes [AC_2-wlan-sec-prof-wlan-security] quit
# Create an SSID profile and set the SSID name to wlan-net1.
[AC_2-wlan-view] ssid-profile name wlan-net1 [AC_2-wlan-ssid-prof-wlan-net1] ssid wlan-net1 [AC_2-wlan-ssid-prof-wlan-net1] quit
# Create the VAP profile wlan-vap1, set the data forwarding mode and service VLAN, and apply the security profile and SSID profile to the VAP profile.
[AC_2-wlan-view] vap-profile name wlan-vap1 [AC_2-wlan-vap-prof-wlan-vap1] forward-mode direct-forward [AC_2-wlan-vap-prof-wlan-vap1] service-vlan vlan-id 102 [AC_2-wlan-vap-prof-wlan-vap1] security-profile wlan-security [AC_2-wlan-vap-prof-wlan-vap1] ssid-profile wlan-net1 [AC_2-wlan-vap-prof-wlan-vap1] quit
# Bind the VAP profile to the AP group and apply the VAP profile wlan-vap1 to radio 0 and radio 1 of the APs.
[AC_2-wlan-view] ap-group name ap-group2 [AC_2-wlan-ap-group-ap-group2] vap-profile wlan-vap1 wlan 1 radio 0 [AC_2-wlan-ap-group-ap-group2] vap-profile wlan-vap1 wlan 1 radio 1 [AC_2-wlan-ap-group-ap-group2] quit
# Set other parameters similarly as those of AC_1.
- Configure basic WLAN services on AC_3.
- Enable N+1 backup on AC_1, AC_2, and AC_3.# On AC_1, configure the AC's global priority and IP address of AC_3.

AC priorities determine the AC roles. The AC with a higher priority is the active AC, and the AC with a lower priority is the standby AC. A smaller value indicates a higher priority. If the AC priorities are the same, the AC that connects to more APs is the active AC. If the ACs connect to the same number of APs, the AC that connects to more STAs is the active AC. If the ACs connect to the same number of STAs, the AC with a smaller IP address is the active AC.
[AC_1-wlan-view] ac protect priority 0 protect-ac 10.23.203.1 Warning: Operation successful. It will take effect after AP reset.
# On AC_2, configure the AC's global priority and IP address of AC_3.[AC_2-wlan-view] ac protect priority 0 protect-ac 10.23.203.1 Warning: Operation successful. It will take effect after AP reset.
# Configure the global priority of AC_3.[AC_3-wlan-view] ac protect priority 5 Warning: Operation successful. It will take effect after AP reset.
# On AC_1, enable N+1 backup and restart all APs to make the function take effect.
By default, N+1 backup is enabled. The system displays an Info message if you run the undo ac protect enable command. You need to run the ap-reset all command to restart all APs. After the APs are restarted, N+1 backup starts to take effect.
[AC_1-wlan-view] undo ac protect enable Info: Backup function has already disabled. [AC_1-wlan-view] ap-reset all Warning: Reset AP(s), continue?[Y/N]:y
# On AC_2, enable N+1 backup and restart all APs to make the function take effect.[AC_2-wlan-view] undo ac protect enable Info: Backup function has already disabled. [AC_2-wlan-view] ap-reset all Warning: Reset AP(s), continue?[Y/N]:y
# Enable revertive switchover and N+1 backup on AC_3.
By default, global revertive switchover is enabled. The system displays an Info message if you run the undo ac protect restore disable command.
[AC_3-wlan-view] undo ac protect restore disable Info: Protect restore has already enabled. [AC_3-wlan-view] undo ac protect enable Info: Backup function has already disabled. [AC_3-wlan-view] ap-reset all Warning: Reset AP(s), continue?[Y/N]:y
- Verify the configuration.
# Run the display ac protect commands on AC_1 to check N+1 backup information.
[AC_1-wlan-view] display ac protect ------------------------------------------------------------ Protect state : disable Protect AC : 10.23.203.1 Priority : 0 Protect restore : enable ... ------------------------------------------------------------
# Run the display ac protect commands on AC_2 to check N+1 backup information.
[AC_2-wlan-view] display ac protect ------------------------------------------------------------ Protect state : disable Protect AC : 10.23.203.1 Priority : 0 Protect restore : enable ... ------------------------------------------------------------
# Run the display ac protect and display ap-system-profile commands on AC_3 to check N+1 backup information.
[AC_3-wlan-view] display ac protect ------------------------------------------------------------ Protect state : disable Protect AC : - Priority : 5 Protect restore : enable ... ------------------------------------------------------------ [AC_3-wlan-view] display ap-system-profile name ap-system1 ------------------------------------------------------------------------------ AC priority : - Protect AC IP address : 10.23.201.1 ... [AC_3-wlan-view] display ap-system-profile name ap-system2 ------------------------------------------------------------------------------ AC priority : - Protect AC IP address : 10.23.202.1 ...
The WLAN with the SSID wlan-net or wlan-net1 is available for STAs connected to the APs, and these STAs can connect to the WLAN and go online normally.
When the link between an AP and AC_1 or AC_2 fails, AC_3 takes over the active role. This ensures accelerate service recovery.
Configuration Files
Switch_1 configuration file
# sysname Switch_1 # vlan batch 99 101 # interface GigabitEthernet0/0/1 port link-type trunk port trunk pvid vlan 99 port trunk allow-pass vlan 99 101 port-isolate enable group 1 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 99 101 # return
Switch_2 configuration file
# sysname Switch_2 # vlan batch 100 102 # interface GigabitEthernet0/0/1 port link-type trunk port trunk pvid vlan 100 port trunk allow-pass vlan 100 102 port-isolate enable group 1 # interface GigabitEthernet0/0/2 port link-type trunk port trunk allow-pass vlan 100 102 # return
AC_1 configuration file
# sysname AC_1 # vlan batch 101 201 # interface Vlanif201 ip address 10.23.201.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 201 # ip route-static 10.23.99.0 255.255.255.0 10.23.201.2 # capwap source interface Vlanif201 # wlan ac protect protect-ac 10.23.203.1 security-profile name wlan-security security wpa2 psk pass-phrase %^%#hgEp#@>security wpa2 psk pass-phrase %^%#hgEp#@> ssid-profile name wlan-net ssid wlan-net vap-profile name wlan-vap service-vlan vlan-id 101 ssid-profile wlan-net security-profile wlan-security regulatory-domain-profile name domain1 ap-group name ap-group1 regulatory-domain-profile domain1 radio 0 vap-profile wlan-vap wlan 1 radio 1 vap-profile wlan-vap wlan 1 ap-id 0 type-id 19 ap-mac 60de-4476-e360 ap-sn 210235554710CB000042 ap-name area_1 ap-group ap-group1 # return
AC_2 configuration file
# sysname AC_2 # vlan batch 102 202 # interface Vlanif202 ip address 10.23.202.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 202 # ip route-static 10.23.101.0 255.255.255.0 10.23.202.2 # capwap source interface vlanif202 # wlan ac protect protect-ac 10.23.203.1 security-profile name wlan-security security wpa2 psk pass-phrase %^%#m"tz0f>~7.[`^6RWdzwCy16hJj/Mc!,}s`X*B]}A%^%# aes ssid-profile name wlan-net1 ssid wlan-net1 vap-profile name wlan-vap1 service-vlan vlan-id 102 ssid-profile wlan-net1 security-profile wlan-security regulatory-domain-profile name domain1 ap-group name ap-group2 regulatory-domain-profile domain1 radio 0 vap-profile wlan-vap1 wlan 1 radio 1 vap-profile wlan-vap1 wlan 1 ap-id 1 type-id 19 ap-mac 60de-4474-9640 ap-sn 210235419610D2000097 ap-name area_2 ap-group ap-group2 # return
AC_3 configuration file
# sysname AC_3 # vlan batch 101 to 102 203 # interface Vlanif203 ip address 10.23.203.1 255.255.255.0 # interface GigabitEthernet0/0/1 port link-type trunk port trunk allow-pass vlan 203 # capwap source interface vlanif203 # wlan ac protect priority 5 security-profile name wlan-security security wpa2 psk pass-phrase %^%#m"tz0f>~7.[`^6RWdzwCy16hJj/Mc!,}s`X*B]}A%^%# aes ssid-profile name wlan-net ssid wlan-net ssid-profile name wlan-net1 ssid wlan-net1 vap-profile name wlan-vap service-vlan vlan-id 101 ssid-profile wlan-net security-profile wlan-security vap-profile name wlan-vap1 service-vlan vlan-id 102 ssid-profile wlan-net1 security-profile wlan-security regulatory-domain-profile name domain1 ap-system-profile name ap-system1 protect-ac ip-address 10.23.201.1 ap-system-profile name ap-system2 protect-ac ip-address 10.23.202.1 ap-group name ap-group1 ap-system-profile ap-system1 regulatory-domain-profile domain1 radio 0 vap-profile wlan-vap wlan 1 radio 1 vap-profile wlan-vap wlan 1 ap-group name ap-group2 ap-system-profile ap-system2 regulatory-domain-profile domain1 radio 0 vap-profile wlan-vap1 wlan 1 radio 1 vap-profile wlan-vap1 wlan 1 ap-id 0 type-id 19 ap-mac 60de-4476-e360 ap-sn 210235554710CB000042 ap-name area_1 ap-group ap-group1 ap-id 1 type-id 19 ap-mac 60de-4474-9640 ap-sn 210235419610D2000097 ap-name area_2 ap-group ap-group2 # returnRouter_1 configuration file
# sysname Router_1 # vlan batch 99 101 201 # dhcp enable # interface Vlanif99 ip address 10.23.99.1 255.255.255.0 dhcp select relay dhcp relay server-ip 10.23.200.1 # interface Vlanif101 ip address 10.23.101.1 255.255.255.0 dhcp select relay dhcp relay server-ip 10.23.200.1 # interface Vlanif201 ip address 10.23.201.2 255.255.255.0 # interface Ethernet2/0/0 port link-type trunk port trunk allow-pass vlan 99 101 # interface Ethernet2/0/1 port link-type trunk port trunk allow-pass vlan 201 # return
Router_2 configuration file
# sysname Router_2 # vlan batch 100 102 202 # dhcp enable # interface Vlanif100 ip address 10.23.100.1 255.255.255.0 dhcp select relay dhcp relay server-ip 10.23.200.1 # interface Vlanif102 ip address 10.23.102.1 255.255.255.0 dhcp select relay dhcp relay server-ip 10.23.200.1 # interface Vlanif202 ip address 10.23.202.2 255.255.255.0 # interface Ethernet2/0/0 port link-type trunk port trunk allow-pass vlan 100 102 # interface Ethernet2/0/1 port link-type trunk port trunk allow-pass vlan 202 # return
Router_3 configuration file
# sysname Router_3 # vlan batch 200 203 # dhcp enable # ip pool ap_1_pool gateway-list 10.23.99.1 network 10.23.99.0 mask 255.255.255.0 option 43 sub-option 2 ip-address 10.23.201.1 10.23.203.1 # ip pool ap_2_pool gateway-list 10.23.100.1 network 10.23.100.0 mask 255.255.255.0 option 43 sub-option 2 ip-address 10.23.202.1 10.23.203.1 # ip pool sta_1_pool gateway-list 10.23.101.1 network 10.23.101.0 mask 255.255.255.0 # ip pool sta_2_pool gateway-list 10.23.102.1 network 10.23.102.0 mask 255.255.255.0 # interface Vlanif200 ip address 10.23.200.1 255.255.255.0 # interface Vlanif203 ip address 10.23.203.2 255.255.255.0 # interface Ethernet2/0/0 port link-type trunk port trunk allow-pass vlan 200 # interface Ethernet2/0/1 port link-type trunk port trunk allow-pass vlan 203 # return