Example for Configuring ACL-based Remote Traffic Mirroring
Remote Traffic Mirroring Overview
In remote traffic mirroring, service traffic matching configured rules is copied to an observing port that is connected to a monitoring device through an intermediate network for analysis and monitoring.
You can configure traffic mirroring using Modular QoS Command-Line Interface (MQC) and ACL. MQC-based traffic mirroring is complex to configure but supports more matching rules and can be applied to both the inbound and outbound directions. ACL-based traffic mirroring is easy to configure but supports fewer matching rules than MQC-based traffic mirroring and can be applied to only the inbound direction.
Configuration Notes
You must dedicate observing ports for mirroring use and do not configure other services on them to prevent mirrored traffic and other service traffic from affecting each other. Do not configure any member port of an Eth-Trunk as an observing port. If you must do so, ensure that the bandwidth of service traffic on this port and the bandwidth occupied by the mirrored traffic do not exceed the bandwidth limit of the port.
If the mirroring function is deployed on many ports of a device, a great deal of internal forwarding bandwidth will be occupied, which affects the forwarding of other services. Additionally, if the mirrored port bandwidth is higher than the observing port bandwidth, for example, 1000 Mbit/s on a mirrored port and 100 Mbit/s on an observing port, the observing port will fail to forward all mirrored packets in a timely manner because of insufficient bandwidth, leading to packet loss.
For the applicable products and versions of this configuration example, see Applicable product models and versions.
Networking Requirements
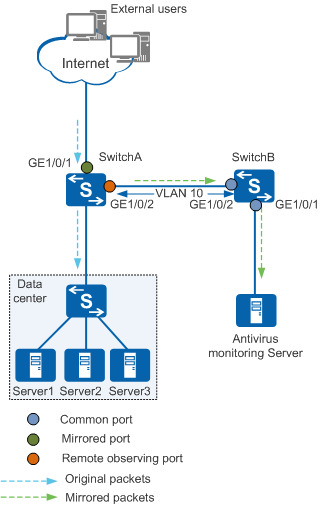
As shown in Figure 1, external users on the Internet access the servers of a company through SwitchA. The antivirus monitoring device Server connects to SwitchA through SwitchB.
The official website of the company is paralyzed because of malicious attacks. The Server needs to remotely analyze traffic with TCP port number WWW to locate the attack source.
Configuration Roadmap
- Configure GE1/0/2 of SwitchA as a Layer 2 remote observing port to forward mirrored packets to the specified VLAN.
- Configure an advanced ACL on SwitchA to match traffic with TCP port number WWW.
- Configure an ACL-based traffic policy on GE1/0/1 of SwitchA to mirror the matching traffic.
- Create a VLAN on SwitchB, disable MAC address learning in this VLAN, and add ports to the VLAN to forward the mirrored packets sent from the observing port to the Server.
Procedure
- Configure an observing port on SwitchA.
# Configure GE1/0/2 of SwitchA as a Layer 2 remote observing port and bind the observing port to VLAN 10.
<HUAWEI> system-view [HUAWEI] sysname SwitchA [SwitchA] observe-port 1 interface gigabitethernet 1/0/2 vlan 10 //Configure GE1/0/2 as Layer 2 remote observing port 1, and add it to VLAN 10.
After the configuration is complete, the observing port forwards mirrored packets to VLAN 10 removing the need to add the observing port to the VLAN.
- Configure an advanced ACL on SwitchA.
# Create an advanced ACL numbered 3000 on SwitchA to match traffic with TCP port number WWW.
[SwitchA] acl number 3000 //Create ACL 3000 to allow the packets with the TCP port number WWW to pass through. [SwitchA-acl-adv-3000] rule permit tcp destination-port eq www [SwitchA-acl-adv-3000] quit - Configure an ACL-based traffic policy on SwitchA.
# Configure an ACL-based traffic policy on GE1/0/1 of SwitchA to mirror the matching traffic.
[SwitchA] interface gigabitethernet 1/0/1 [SwitchA-GigabitEthernet1/0/1] traffic-mirror inbound acl 3000 to observe-port 1 //Mirror incoming packets that match ACL 3000 on GE1/0/1 to observing port 1. [SwitchA-GigabitEthernet1/0/1] return - Create a VLAN on SwitchB and add ports to the VLAN.
# Create VLAN 10 on SwitchB, disable MAC address learning in this VLAN, and add GE1/0/1 and GE1/0/2 to VLAN 10.

Here, VLAN 10 is used for forwarding only mirrored packets. If VLAN 10 already exists and has learned MAC address entries, run the undo mac-address vlan vlan-id command in the system view to delete all MAC address entries in VLAN 10.
<HUAWEI> system-view [HUAWEI] sysname SwitchB [SwitchB] vlan 10 [SwitchB-vlan10] mac-address learning disable //Disable MAC address learning in this VLAN. [SwitchB-vlan10] quit [SwitchB] interface gigabitethernet 1/0/1 [SwitchB-GigabitEthernet1/0/1] port link-type access //Set the link type of the interface on the monitoring device to access. The default link type of interfaces is not access. [SwitchB-GigabitEthernet1/0/1] port default vlan 10 [SwitchB-GigabitEthernet1/0/1] quit [SwitchB] interface gigabitethernet 1/0/2 [SwitchB-GigabitEthernet1/0/2] port link-type trunk //Set the link type of the interface on the network side to trunk. The default link type of interfaces is not trunk. [SwitchB-GigabitEthernet1/0/2] port trunk allow-pass vlan 10 [SwitchB-GigabitEthernet1/0/2] return
- Verify the configuration.
# Check ACL rules and traffic behavior information.
<SwitchA> display traffic-applied interface gigabitethernet 1/0/1 inbound ----------------------------------------------------------- ACL applied inbound interface GigabitEthernet1/0/1 ACL 3000 rule 5 permit tcp destination-port eq www (match-counter 0) ACTIONS: mirror to observe-port 1 -----------------------------------------------------------
# Check the observing port configuration.
<SwitchA> display observe-port ---------------------------------------------------------------------- Index : 1 Untag-packet : No Interface : GigabitEthernet1/0/2 Vlan : 10 ----------------------------------------------------------------------
# Check the mirrored port configuration.
<SwitchA> display port-mirroring ---------------------------------------------------------------------- Observe-port 1 : GigabitEthernet1/0/2 ---------------------------------------------------------------------- Stream-mirror: ---------------------------------------------------------------------- Behavior Direction Observe-port ---------------------------------------------------------------------- 1 SACL - Observe-port 1 ----------------------------------------------------------------------
Configuration Files
Configuration file of SwitchA
# sysname SwitchA # observe-port 1 interface GigabitEthernet1/0/2 vlan 10 # acl number 3000 rule 5 permit tcp destination-port eq www # interface GigabitEthernet1/0/1 traffic-mirror inbound acl 3000 to observe-port 1 # return
Configuration file of SwitchB
# sysname SwitchB # vlan batch 10 # vlan 10 mac-address learning disable # interface GigabitEthernet1/0/1 port link-type access port default vlan 10 # interface GigabitEthernet1/0/2 port link-type trunk port trunk allow-pass vlan 10 # return
Applicable product models and versions
Product |
Product Model |
Software Version |
|---|---|---|
S2700 |
S2700-52P-EI, S2700-52P-PWR-EI |
V100R006C05 |
S3700 |
S3700-SI |
V100R006C05 |
S3700-EI |
V100R006C05 |
|
S3700-HI |
V200R001C00 |
|
S5700 |
S5700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02&C03) |
S5710-EI |
V200R001C00, V200R002C00, V200R003C00, V200R005(C00&C02) |
|
S5720-EI |
V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5700-HI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00SPC500&C01&C02) |
|
S5710-HI |
V200R003C00, V200R005(C00&C02&C03) |
|
S5720-HI |
V200R006C00, V200R007(C00&C10), V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5730-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S5731-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S5731-S, S5731S-S |
V200R019C00, V200R019C10 |
|
S5731S-H |
V200R019C00, V200R019C10 |
|
S5732-H |
V200R019C00, V200R019C10 |
|
S5735-L, S5735S-L |
V200R019C00, V200R019C10 |
|
S5735S-L-M |
V200R019C00, V200R019C10 |
|
S5735-S, S5735S-S |
V200R019C00, V200R019C10 |
|
S5700 |
S5735-S-I |
V200R019C10 |
S6700 |
S6700-EI |
V200R001(C00&C01), V200R002C00, V200R003C00, V200R005(C00&C01&C02) |
S6720-EI |
V200R008C00, V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720S-EI |
V200R009C00, V200R010C00, V200R011C00, V200R011C10, V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6720-HI |
V200R012C00, V200R013C00, V200R019C00, V200R019C10 |
|
S6730-H |
V200R013C02, V200R019C00, V200R019C10 |
|
S6730S-H |
V200R019C10 |
|
S6730-S, S6730S-S |
V200R019C00, V200R019C10 |
|
S7700 |
S7703, S7706, S7712 |
V200R005C00, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00, V200R013C02, V200R019C00, V200R019C10 |
S7703 PoE |
V200R013C00, V200R019C00, V200R019C10 |
|
S7706 PoE |
V200R013C00, V200R019C00, V200R019C10 |
|
S9700 |
S9703, S9706, S9712 |
V200R005C00, V200R006C00, V200R007C00, V200R008C00, V200R009C00, V200R010C00, V200R011C10, V200R012C00, V200R013C00 |

For details about software mappings, visit Hardware Query Tool and search for the desired product model.