ARP Entry Fixing
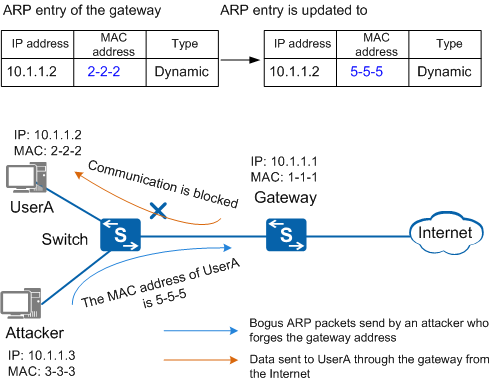
As shown in Figure 1, an attacker poses as UserA to send a bogus ARP packet to the gateway. The gateway then records an incorrect ARP entry for UserA. As a result, UserA cannot communicate with the gateway.
To defend against ARP gateway spoofing attacks, configure the ARP entry fixing function on a gateway. Upon learning an ARP entry for the first time, the gateway enabled with this function does not update the entry, updates only part of the entry, or sends a unicast ARP Request packet to check the validity of the ARP packet for updating the entry.
The device supports three ARP entry fixing modes, as described in Table 1.
| Mode | Description |
|---|---|
| fixed-all | When receiving an ARP packet, the device discards the packet if the MAC address, interface number, or VLAN ID does not match any ARP entry. This mode applies to networks where user MAC addresses and user access locations are fixed. |
| fixed-mac | When receiving an ARP packet, the device discards the packet if the MAC address does not match the MAC address in the corresponding ARP entry. If the MAC addresses match but the interface number or VLAN ID does not match that in the ARP entry, the device updates the interface number or VLAN ID in the ARP entry. This mode applies to networks where user MAC addresses are unchanged but user access locations often change. |
| send-ack | When the device receives ARP packet A with a changed MAC
address, interface number, or VLAN ID, it does not immediately update
the corresponding ARP entry. Instead, the device sends a unicast ARP
Request packet to the user with the IP address mapped to the original
MAC address in the ARP entry. The device then determines whether to
change the MAC address, VLAN ID, or interface number in the ARP entry
depending on the response from the user.
This mode applies to networks where user MAC addresses and user access locations often change. |