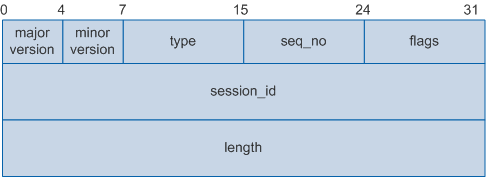
HWTACACS Packets
An HWTACACS client and an HWTACACS server communicate using HWTACACS packets sent over TCP/IP networks. Unlike RADIUS packets with the same format, HWTACACS packets (including HWTACACS Authentication Packet, HWTACACS Authorization Packet, and HWTACACS Accounting Packet) are formatted differently. HWTACACS packets all share the same HWTACACS Packet Header.
HWTACACS Packet Header
HWTACACS defines a 12-byte header that appears in all HWTACACS packets. Figure 1 shows the header.
Field |
Description |
|---|---|
major version |
Major HWTACACS version number. The current version is 0xc. |
minor version |
Minor HWTACACS version number. The current version is 0x0. |
type |
HWTACACS packet type.
|
seq_no |
Sequence number of the packet in a session. The first packet in a session has the sequence number 1 and each subsequent packet increments the sequence number by 1. The value ranges from 1 to 254. |
flags |
Encryption flag on the packet body. This field contains 8 bits, of which only the first bit has a valid value. The value 0 indicates that the packet body is encrypted, and the value 1 indicates that the packet body is not encrypted. |
session_id |
ID of the HWTACACS session, which is the unique identifier of a session. This field does not change for the duration of the HWTACACS session. |
length |
Total length of the HWTACACS packet body, excluding the packet header. |
HWTACACS Authentication Packet Format
- Authentication Start: indicates the type of authentication to be performed, and contains the user name and authentication data. This packet is only sent as the first message in an HWTACACS authentication process.
- Authentication Continue: indicates that the authentication process has not ended. This packet is sent by a client when the client receives an Authentication Reply packet from the server.
- Authentication Reply: notifies the client of the current authentication status. When the server receives an Authentication Start or Authentication Continue packet from a client, the server sends this packet to the client.
The following figure shows the HWTACACS Authentication Start packet body.
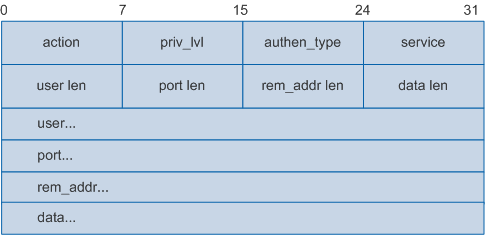
Field |
Description |
|---|---|
action |
Authentication action to be performed. Only the login authentication (0x01) action is supported. |
priv_lvl |
Privilege level of a user. The value ranges from 0 to 15. |
authen_type |
Authentication type.
|
service |
Type of the service requesting authentication. The value varies depending on the user type:
|
user len |
Length of the user name entered by a login user. |
port len |
Length of the port field. |
rem_addr len |
rem_addr field length. |
data len |
Authentication data length. |
user |
Name of the user requesting authentication. The maximum length is 129. |
port |
Name of the user interface requesting authentication. The maximum length is 47.
|
rem_addr |
IP address of the login user. |
data |
Authentication data. Different data is encapsulated depending on the values of action and authen_type. For example, when PAP authentication is used, the value of this field is PAP plain-text password. |
The following figure shows the HWTACACS Authentication Continue packet body.
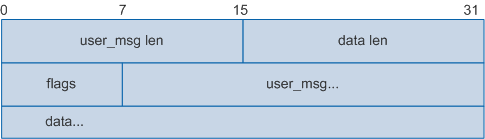
Field |
Description |
|---|---|
user_msg len |
Length of the character string entered by a login user. |
data len |
Authentication data length. |
flags |
Authentication continue flag. Allowed values are:
|
user_msg |
Character string entered by a login user. This field carries the user login password to respond to the server_msg field in the Authentication Reply packet. |
data |
Authentication data. Different data is encapsulated depending on the values of action and authen_type. For example, when PAP authentication is used, the value of this field is PAP plain-text password. |
The following figure shows the HWTACACS Authentication Reply packet body.
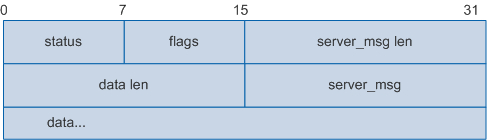
Field |
Description |
|---|---|
status |
Current authentication status. Legal values are:
|
flags |
Whether the client displays the password entered by user in plain text. The value 1 indicates that the password is not displayed in plain text. |
server_msg len |
Length of the server_msg field. |
data len |
Authentication data length. |
server_msg |
Optional field. This field is sent by the server to the user to provide additional information. |
data |
Authentication data, providing information to the client. |
HWTACACS Authorization Packet Format
- Authorization Request: contains a fixed set of fields that indicate how a user is authenticated or processed and a variable set of attributes that describe the information for which authorization is requested.
- Authorization Response: contains a variable set of attributes that can limit or change the clients action.
The following figure shows the HWTACACS Authorization Request packet body.
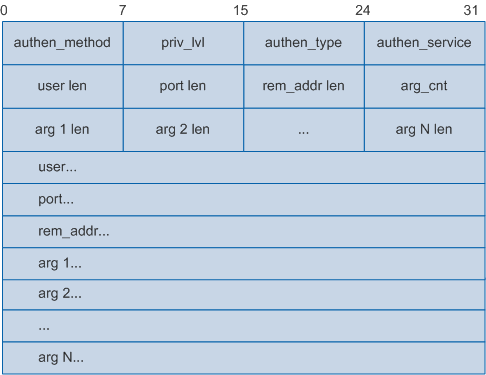

The meanings of the following fields in the Authorization Request packet are the same as those in the Authentication Start packet, and are therefore not described here: priv_lvl, authen_type, authen_service, user len, port len, rem_addr len, port, and rem_addr.
Field |
Description |
|---|---|
authen_method |
Authentication method used by the client to acquire user information. Allowed values are:
|
authen_service |
Type of the service requesting authentication. The value varies depending on the user type:
|
arg_cnt |
Number of attributes carried in the Authorization Request packet. |
argN |
Attribute of the Authorization Request packet, including the following:
|
The following figure shows the HWTACACS Authentication Reply packet body.
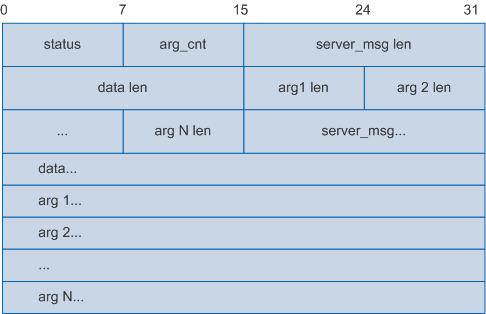

Meanings of the following fields are the same as those in the HWTACACS Authentication Reply packet, and are therefore not described here: server_msg len, data len, and server_msg.
Field |
Description |
|---|---|
status |
Authorization status. Legal values are:
|
arg_cnt |
Number of attributes carried in an Authorization Response packet. |
argN |
Authorization attribute delivered by the HWTACACS authorization server. |
HWTACACS Accounting Packet Format
- Accounting Request: contains information used to provide accounting for a service provided to a user.
- Accounting Response: After receiving and recording an Accounting Request packet, the server returns this packet.
The following figure shows the HWTACACS Accounting Request packet body.


Meanings of the following fields in the Accounting Request packet are the same as those in the Authorization Request packet, and are therefore not described here: authen_method, priv_lvl, authen_type, user len, port len, rem_addr len, port, and rem_addr.
Field |
Description |
|---|---|
flags |
Accounting type. Allowed values are:
|
authen_service |
Type of the service requesting authentication, which varies by user type:
|
arg_cnt |
Number of attributes carried in the Accounting Request packet. |
argN |
Attribute of the Accounting Request packet. |
The following figure shows the HWTACACS Accounting Response packet body.
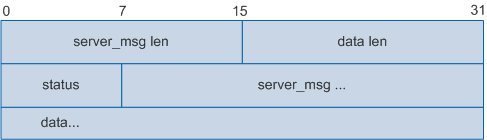
Field |
Description |
|---|---|
server_msg len |
Length of the server_msg field. |
data len |
Length of the data field. |
status |
Accounting status. Legal values are:
|
server_msg |
Information sent by the accounting server to the client. |
data |
Information sent by the accounting server to the administrator. |