DHCP Snooping Fundamentals
DHCP snooping has two modes: DHCPv4 snooping and DHCPv6 snooping. Both modes function in a similar manner. This section uses DHCPv4 snooping as an example.
A DHCP snooping-enabled device forwards DHCP Request messages of users (DHCP clients) to an authorized DHCP server through the trusted interface. The device then generates DHCP snooping binding entries according to the DHCP ACK messages it receives from the DHCP server. To prevent attacks from unauthorized users, the device checks DHCP messages it receives through DHCP snooping-enabled interfaces against the binding table.
DHCP Snooping Trust Function
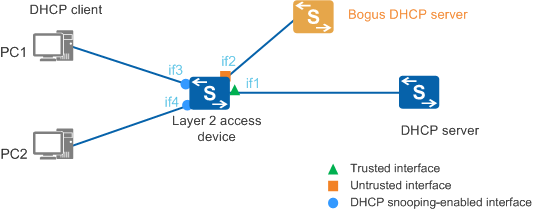
If a bogus DHCP server exists on a network, as shown in Figure 1, DHCP clients may obtain incorrect IP addresses and network configuration parameters from it, leading to communication failures. The trust function controls the source of DHCP Reply messages to prevent bogus DHCP servers from assigning IP addresses and other configurations to DHCP clients.
DHCP snooping involves two interface roles: trusted interface and untrusted interface. The interface roles ensure that DHCP clients obtain IP addresses from an authorized DHCP server.
- DHCP ACK messages, NAK messages, and Offer messages are received from the trusted interface. In addition, the device only forwards DHCP Request messages from DHCP clients to the authorized DHCP server through the trusted interface.
- DHCP ACK messages, NAK messages, and Offer messages are discarded on untrusted interfaces.

- After the dhcp snooping enable command is run on an interface, the interface forwards received DHCP Request messages to all trusted interfaces and discards received DHCP Reply messages.
- After an interface on which the dhcp snooping trusted command is run receives a DHCP Request message, it forwards the message to all other trusted interfaces. If there are no other trusted interfaces, it discards the message. After receiving a DHCP Reply message, it forwards the message only to the interfaces that are connected to clients and have the dhcp snooping enable command configured. If such interfaces cannot be found, it discards the DHCP Reply message.
When DHCP snooping is enabled on a Layer 2 access device, as shown in Figure 1, the interface directly or indirectly connected to the authorized DHCP server is generally configured as a trusted interface (for example, if1). Other interfaces are configured as untrusted interfaces (for example, if2). To ensure that DHCP clients can obtain IP addresses only from the authorized DHCP server, the DHCP Request messages from DHCP clients are forwarded only through the trusted interface. Bogus DHCP servers cannot assign IP addresses to the DHCP clients.
DHCP Snooping Binding Table
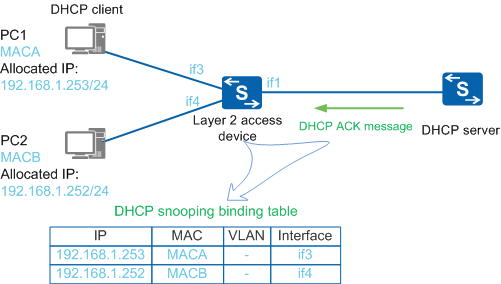
- A PC, functioning as a DHCP client, broadcasts a DHCP Request message.
- The DHCP snooping-enabled Layer 2 access device forwards the message to the DHCP server through the trusted interface.
- The DHCP server unicasts the DHCP ACK message carrying an IP address to the PC.
- The Layer 2 access device obtains required information, such as the PC's MAC address, IP address, and lease time of the IP address, from the DHCP ACK messages. It learns information (interface number and VLAN ID) about the DHCP snooping-enabled interface connected to the PC and generates a DHCP snooping binding entry for the PC.
A DHCP snooping binding entry is aged out when the IP address lease time expires. Alternatively, the entry is deleted when the client sends a DHCP Release message to release its IP address.
The DHCP snooping binding table records the mappings between IP addresses and MAC addresses of DHCP clients. The device can check DHCP messages against the DHCP snooping binding table to prevent attacks initiated by unauthorized users.
Configure DHCP snooping on the Layer 2 access devices or the first DHCP relay agent to ensure that the device obtains parameters such as MAC addresses for generating DHCP snooping binding entries.
If DHCP snooping is enabled on a DHCP relay agent, a trusted interface does not need to be configured on the DHCP relay agent. After receiving DHCP Request messages from clients, the DHCP relay agent modifies the source/destination IP addresses and MAC addresses, and unicasts the messages to the authorized DHCP server. Therefore, the DHCP ACK messages received by the DHCP relay agent are valid, and the DHCP snooping binding entries generated by the DHCP relay agent are correct.