Establishing SAs Through IKEv2 Negotiation
The process of establishing SAs through IKEv2 negotiation is much simpler than that through IKEv1 negotiation. To establish a pair of IPSec SAs, IKEv1 requires two phases: main or aggressive mode + quick mode. At least nine messages are exchanged in main mode + quick mode, and at least six messages are exchanged in aggressive mode + quick mode. In normal cases, IKEv2 requires only two exchanges, totaling four messages, to establish a pair of IPSec SAs. One additional Create_Child_SA Exchange can be used to establish another pair of IPSec SAs if required, during which only two messages are exchanged.
IKEv2 defines three exchanges: Initial Exchanges, Create_Child_SA Exchange, and Informational Exchange.
Initial Exchanges
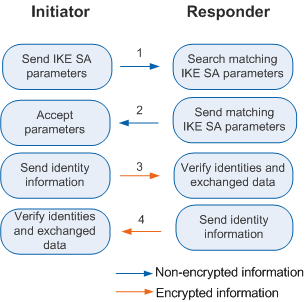
In normal cases, IKEv2 establishes the first pair of IPSec SAs through Initial Exchanges. Corresponding to IKEv1 phase 1, Initial Exchanges involve four messages in two exchanges, as shown in Figure 1.
Messages (1) and (2) are used in exchange 1 (called IKE_SA_INIT) to negotiate IKE SA parameters in plaintext, including the encryption key, authentication key, random number, and DH key. After IKE_SA_INIT is complete, shared keying material is generated, from which all keys used by IPSec SAs are derived.
Messages (3) and (4) are used in exchange 2 (called IKE_AUTH) to authenticate identities of the two parties and the first two messages, and to negotiate IPSec SA parameters. The two messages are encrypted. IKEv2 supports RSA signature authentication, PSK authentication, and EAP authentication. The initiator does not set the authentication payload in message (3) to indicate that EAP authentication is required.
Create_Child_SA Exchange
After one pair of IPSec SAs is established based on an IKE SA, Create_Child_SA Exchange can be performed to negotiate more pairs of IPSec SAs. In addition, Create_Child_SA Exchange can be performed for IKE SA re-negotiation.
Create_Child_SA Exchange involves two messages in one exchange and corresponds to IKEv1 phase 2. The initiator in Create_Child_SA Exchange can be the initiator or responder in Initial Exchanges. Create_Child_SA Exchange can be performed only after Initial Exchanges are complete. Messages transmitted in Create_Child_SA Exchange are protected by keys negotiated in Initial Exchanges.
Similar to IKEv1, when PFS is enabled, Create_Child_SA Exchange requires an additional DH exchange to generate new keying material. All keys used by child SAs are derived from this keying material.
Informational Exchange
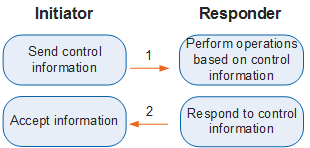
IKEv2 peers perform Informational Exchange to exchange control information, including error information and notifications, as shown in Figure 2.
Informational Exchange must be performed under the protection of an IKE SA. Specifically, Informational Exchange is performed after Initial Exchanges are complete. Control information may belong to an IKE SA or a child SA. Therefore, Informational Exchange must be protected by the IKE SA or the IKE SA based on which child IPSec SAs are established accordingly.