Application Scenarios for Keychains
Keychain provides authentication for applications. The following application protocols support Keychain authentication: Routing Information Protocol (RIP), Intermediate System to Intermediate System (IS-IS), Open Shortest Path First (OSPF), Border Gateway Protocol (BGP), and Multicast Source Discovery Protocol (MSDP). Applications use the same Keychain authentication procedures. Create a Keychain and then use the Keychain to perform an authentication.
IS-IS Using Keychain for Authentication
IS-IS is a commonly used routing protocol, and IS-IS security is needed. You can configure a fixed authentication algorithm and key to authenticate IS-IS packets. But fixed authentication algorithms and keys may be decrypted. The use of Keychain to authenticate the IS-IS packets makes IS-IS more secure.
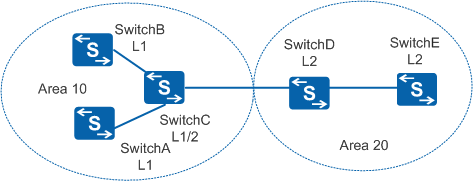
As shown in Figure 1, SwitchA, SwitchB, SwitchC, SwitchD and SwitchE use IS-IS to communicate. SwitchA, SwitchB, and SwitchC belong to area 10; SwitchD and SwitchE belong to area 20. SwitchA and SwitchB are Level-1 devices; SwitchD and SwitchE are Level-2 devices; SwitchC is a Level-1-2 device. Create a Keychain on each device to authenticate the IS-IS packets. Configure area and domain authentication in the IS-IS process, and configure interface authentication on the interface as well.