Interconnection Between VPNs and the Internet
Users within a VPN typically only communicate with other users in the same VPN. They cannot communicate with users on the Internet or connect to the Internet. Many VPN sites however may need to access the Internet. To implement interconnection between a VPN and the Internet, the following conditions must be met:
VPN devices that need to access the Internet have reachable routes to the Internet.
Routes from the Internet to VPN devices s are available.
Security mechanisms, such as firewalls must be used.
Interconnection between a VPN and the Internet can be implemented in the following ways:
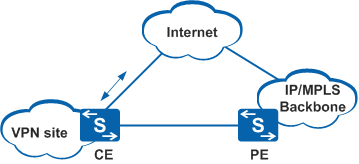
Implementing Interconnection on a PE Device
PE devices of the backbone network identify data streams destined for the VPN and the Internet, and forward data to the Internet and the VPN. PE devices provide firewall functions between the VPN and the Internet.
Implementing Interconnection on an Internet Gateway
Internet gateways are carrier devices connected to the Internet and must support VPN route management. For example, a PE device lacking an attached VPN user functions as an Internet gateway.
Implementing Interconnection on a CE Device
CE devices of the private network identify data streams destined for the VPN and the Internet, and forward data to two areas: One area connects to the VPN through a PE device and the other area connects to the Internet through an ISP router (that does not belong to the VPN). CE devices provide firewall functions.
Implementing Interconnection on a PE Device
Default static routes are used when interconnection is implemented on a PE device. The following applies in this scenario:
The PE device sends a default route destined for the Internet to the CE device.
The PE device adds a default route destined for the Internet gateway to the VPN routing table.
To ensure that the Internet has a route to the VPN, the PE device must have a static route to the CE in the public routing table and advertise this route to the Internet. The static route is manually added to the public routing table of the PE device. In the static route, the destination address is the address of the VPN user, and the outbound interface is the PE interface that connects to the CE device. The PE uses an IGP to advertise the route to the Internet.
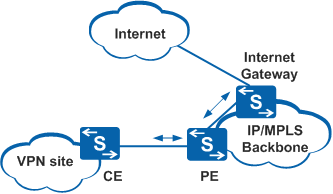
Implementing Interconnection on an Internet Gateway
An instance is configured for each VPN on the Internet gateway. Each VPN uses one interface that is bound to the VPN instance to access the Internet.
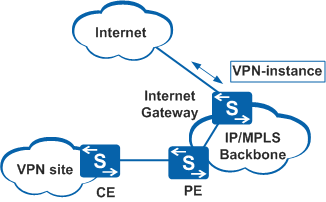
Implementing Interconnection on a CE Device
The following explains interconnection between a VPN and the Internet that can be implemented on a CE device:
Figure 3 shows a network example of a CE device connecting directly to the Internet.
A direct connection with the Internet can be achieved in either of the following ways:
A site (for example, central site) connects to the Internet. The CE device in the central site has a default route advertised to other sites through the backbone network. Firewalls are only deployed in the central site. All traffic to the Internet passes through the VPN backbone network except the traffic of the central site. One application is the connection between the Internet and Hub site in Hub and Spoke networking.
Each site connects to the Internet. Each CE device has a default route to the Internet and configured with firewall functions. No traffic to the Internet passes through the VPN backbone network.
Figure 4 shows a network example of a single CE interface or sub-interface connecting to a PE device.
The PE device injects the CE device routes into the public routing table and advertises routes to the Internet. The PE device then advertises the default route or Internet routes to the CE device. The interface that connects to the PE device does not belong to any VPN and is not associated with any VPN instance. The interface acts as a VPN user and a non-VPN user to connect to the PE device.
It is recommended that a tunnel be established between the VPN backbone device connected to the Internet and the PE device connected to the CE device. Internet routes are transmitted through the tunnel and are not accepted by P device.
Comparison of Three Interconnection Solutions
Implementing interconnection on a PE device saves interface resources and allows different VPNs to share one public IP address. Configuration on the PE device, however, is complex and security cannot be guaranteed. Denial of Service (DoS) attacks from the Internet may occur on the PE device. When DoS attacks occur, the link between the PE and CE devices is occupied by a significant amount of attack traffic and cannot transmit valid VPN packets.
Implementing interconnection on an Internet gateway provides higher security than that on a PE device. An Internet gateway must be configured with multiple VPN instances, which may overburden the gateway. An Internet gateway also has multiple interfaces connected to the Internet and each interface has a public network IP address. Each VPN uses an interface on the gateway and one public network IP address.
Implementing interconnection on a CE device is simple to deploy. This solution has high security and reliability because public routes are separated from VPN routes. This solution, however, consumes interface resources and each VPN needs a public network address.
Solution |
Security |
Interface |
Public IP Address |
Deployment (Easy or Difficult) |
|---|---|---|---|---|
Implementing interconnection on a PE device |
Low |
The PE device reserves only one interface for both VPN access and Internet access. This solution saves interface resources. |
Multiple VPNs on the PE device share a public IP address. |
Difficult |
Implementing interconnection on an Internet gateway |
High |
The Internet gateway must reserve an interface for each VPN to access the Internet. This solution consumes interface resources of the gateway. |
Each VPN uses a public IP address. |
Difficult |
Implementing interconnection on a CE device |
High |
The CE device must reserve an interface for each VPN to access the Internet. This solution consumes interface resources of the CE. |
Each VPN uses a public IP address. |
Easy |