Overview of NAC
Definition
Network Admission Control (NAC) is an end-to-end access security framework and includes 802.1X authentication, MAC address authentication, and Portal authentication.
With the development of enterprise network, threats increasingly bring risks, such as viruses, Trojan horses, spyware, and malicious network attacks. On a traditional enterprise network, the intranet is considered as secure and threats come from extranet. However, 80% security threats actually come from the intranet. The intranet threats will cause serious damage in a wide range. Even worse, the system and network will break down. In addition, when intranet users browse websites on the external network, the spyware and Trojan horse software may be automatically installed on users' computers, which cannot be sense by the users. The malicious software may spread on the internal network.
The traditional security measures cannot meet requirements on border defense due to increasing security challenges. The security model should be converted into active mode to solve security problems from the roots (terminals), improving information security level of the entire enterprise.
The NAC solution integrates terminal security and access control and takes the check, audit, secure, and isolation measures to improve the proactive protection capability of terminals. This solution ensures security of each terminal and the entire enterprise network.
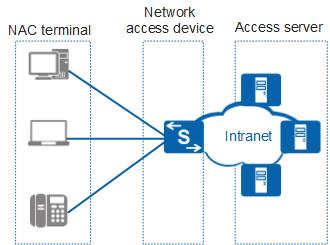
As shown in Figure 1, NAC includes three components: NAC terminal, network access device, and access server.
- NAC terminal: functions as the NAC client and interacts with network access devices to authenticate access users. If 802.1X authentication is used, users must install client software.
- Network access device: function as the network access control point that enforces enterprise security policies. It allows, rejects, isolates, or restricts users based on the security policies customized for enterprise networks.
- Access server: includes the access control server, management server, antivirus server, and patch server. It authenticates users, checks terminal security, repairs and upgrades the system, and monitors and audits user actions.
Purpose
Traditional network security technologies focus on threats from external computers, but typically neglect threats from internal computers. In addition, current network devices cannot prevent attacks initiated by devices on internal networks.
The NAC security framework was developed to ensure the security of network communication services. The NAC security framework improves internal network security by focusing on user terminals, and implement security control over access users to provide end-to-end security.