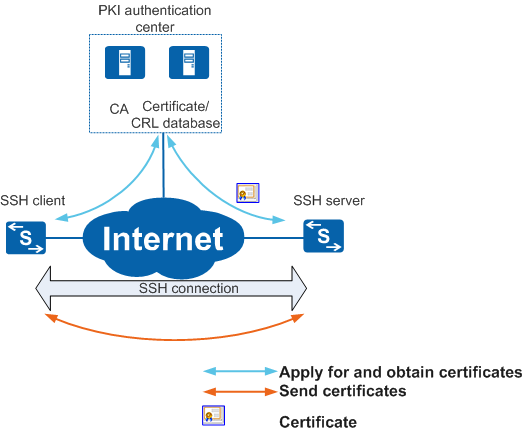
Application in SSH
On the network shown in Figure 1, an SSH client securely logs in to the web page of the SSH server and manages network devices on web. To improve security of SSH connections, the CA trusted by SSH client and server issues local certificates. The communicating parties verify the certificates of each other, and set up an SSH connection only when the certificate verification is successful. This avoids potential attacks.
The SSH client and server make the following interaction during SSL connection setup:
- The client and server apply for local certificates from the PKI authentication center.
- The PKI authentication center issues local certificates to the client and server.
- The client sends an SSH connection request to the server and sends its own local certificate to the server.
- After verifying the local certificate from the client, the server sends an SSH connection request and its own local certificate to the client.
- After verifying the local certificate from the server, the client sends the verification result to the server. The SSH connection is set up.