Logout of Portal Authentication Users
- The RADIUS server still performs accounting for the users, causing incorrect accounting.
- Unauthorized users may spoof IP addresses and MAC addresses of authorized users to access the network.
- If there are many offline users, these users are still counted as access users of the device. As a result, other users may fail to access the network.
The access device needs to detect user logout immediately, delete the user entry, and instruct the RADIUS server to stop accounting.
- A client logs out proactively.
- An access device controls user logout.
- The authentication server or Portal server forces a user to go offline.
A Client Logs Out
A user proactively initiates logout. For example, when the user clicks the logout button, the client sends a logout request to the Portal server.
For Portal authentication using the Portal protocol, after receiving a logout request from a user, the Portal server notifies the client that the user goes offline, without waiting for the access device to confirm the logout. For Portal authentication based on the HTTP or HTTPS protocol, after receiving a logout request from a user, the Portal server instructs the client to send a logout notification to the access device.
Portal authentication based on the Portal protocol
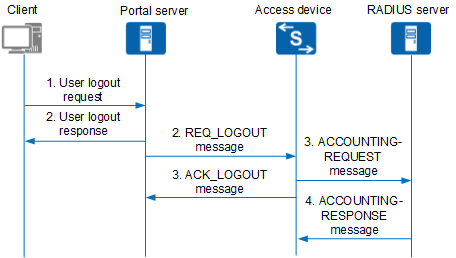
Figure 1 shows the logout process.
- The client sends a logout request to the Portal server.
- The Portal server sends a user logout response to the client and sends a logout notification packet (REQ_LOGOUT) to the access device.
The access device sends an accounting stop request packet (ACCOUNTING-REQUEST) to the RADIUS server and disconnects the user. The access device sends a logout response packet (ACK_LOGOUT) to the Portal server.
After receiving the ACK_LOGOUT message, the Portal server disconnects the user.
- The RADIUS server returns an accounting stop response packet (ACCOUNTING-RESPONSE) and disconnects the user.
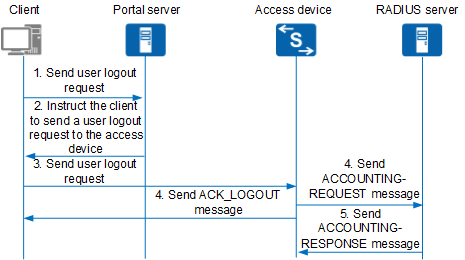
Portal authentication based on the HTTP or HTTPS protocol
- The client sends a logout request to the Portal server.
- The Portal server instructs the client to send a user logout request to the access device and disconnects the user.
- The client sends a logout request to the access device.
- The access device sends an ACCOUNTING-REQUEST message to the RADIUS server and disconnects the user. The access device sends a logout response packet (ACK_LOGOUT) to the client.
- The RADIUS server returns an ACCOUNTING-RESPONSE message and disconnects the user.
The Access Device Controls User Logout
The access device controls user logout using either of the following ways:
- Run the cut access-user command to force a user to go offline.
- Configure user detection to check whether a user is online. If the user does not respond within a specified period, the access device considers the user to be offline and deletes the user entry.
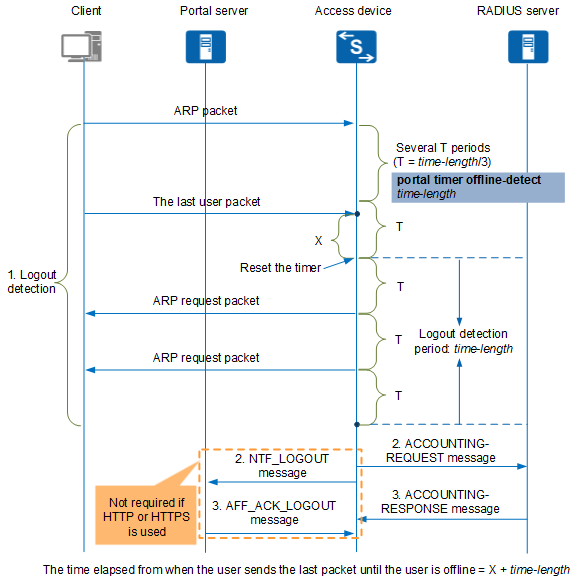
Figure 3 shows the user logout process controlled by the access device. The Portal protocol is used as an example. For the HTTP/HTTPS protocol, the process is similar except that the access device does not send a logout notification to the Portal server.
The access device obtains the client IP address, and starts the logout detection timer configured by time-length in the portal timer offline-detect time-length command. When receiving a packet from the client within T (T = time-length/3), the access device considers the user to be online and resets the logout detection timer at T. If the access device does not receive a packet from the client within T, the access device sends an ARP request packet to the client at an interval of T. If the access device does not receive any response packet or other packets from the client after sending two consecutive ARP request packets (that is, no packet from the client is received within the logout detection period), the access device considers the user to be offline.
The access device sends an NTF_LOGOUT message to the Portal server and disconnects the user. In addition, the access device sends an ACCOUNTING-REQUEST message to the RADIUS server.
The Portal server sends an AFF_ACK_LOGOUT message to the access device and disconnects the user. The RADIUS server sends an ACCOUNTING-RESPONSE message to the access device and disconnects the user.
The Authentication Server Forces a User to Log Out
The authentication server forces a user to log out using either of the following methods:
- Sends a Disconnect Message (DM) to an access device.
- Uses the standard RADIUS attributes Session-Timeout and Termination-Action. The Session-Timeout attribute specifies the online duration timer of a user. The value of Termination-Action is set to 0, indicating that the user is disconnected by the RADIUS server when the online duration timer expires.
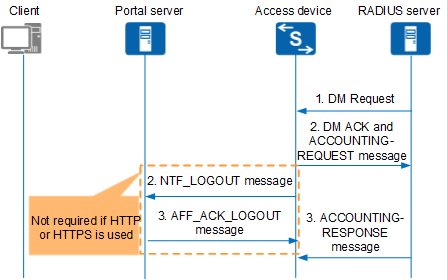
Figure 4 shows the user logout process controlled by the authentication server by sending a DM.
The RADIUS server sends a DM Request to the access device.
The access device sends an NTF_LOGOUT message to the Portal server and disconnects the user. In addition, the access device sends a DM ACK and an ACCOUNTING-REQUEST message to the RADIUS server.
The Portal server sends an AFF_ACK_LOGOUT message to the access device and disconnects the user. The RADIUS server sends an ACCOUNTING-RESPONSE message to the access device and disconnects the user.
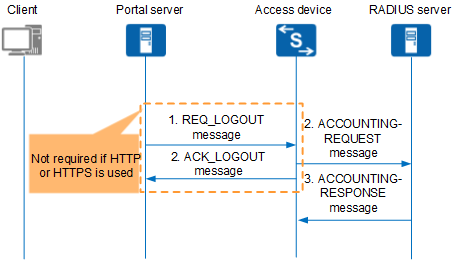
The Portal Server Forces a User to Log Out
When an administrator deregisters a user or the Portal server detects that a user is offline, the Portal server disconnects the user and sends a REQ_LOGOUT message to the access device.
Figure 5 shows the user logout process controlled by the Portal server. The Portal protocol is used as an example. For the HTTP/HTTPS protocol, the process is similar except that the Portal server does not send a logout notification to the access device.
- The Portal server sends an REQ_LOGOUT message to the access device.
The access device sends an ACCOUNTING-REQUEST message to the RADIUS server and disconnects the user. The access device sends an ACK_LOGOUT message to the Portal server.
After receiving the ACK_LOGOUT message, the Portal server disconnects the user.
- The RADIUS server returns an ACCOUNTING-RESPONSE message and disconnects the user.