STA Access
STAs can access wireless networks after APs are logged in and CAPWAP tunnels are established. STA access involves the following steps:
- Scanning
- Link authentication
- Association
A STA can access wireless networks in either IPv4 or IPv6 mode, with the IPv4 mode taking precedence.
- If the number of STAs associated with an AP reaches the maximum limit of the AP but not the maximum limit of the AC, a new STA cannot connect to the current AP. However, the STA can associate with another AP on the network.
- If the number of STAs associated with an AP reaches the maximum limit of the AC, a new STA cannot access the WLAN even though the maximum limit of the AP is not reached.
- If the number of STAs associated with an AP does not reach the maximum limit of the AP or AC, a new STA can access the WLAN.
Scanning
The STA scanning stage is similar for Fit AP and agile distributed architectures. The only difference is that STAs scan different objects: APs in Fit AP architecture and RUs in agile distributed architecture.
A STA can actively or passively scan wireless networks.
Active Scanning
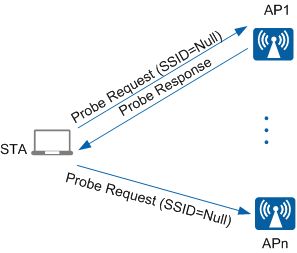
Probes containing an SSID: The STA sends a Probe Request frame containing an SSID in each channel to search for the AP with the same SSID. Only the AP with the same SSID will respond to the STA. For example, in Figure 1, the STA sends a Probe Request frame containing the SSID huawei to search for an AP with the SSID huawei.
This method applies to the scenario where a STA actively scans wireless networks to access a specified wireless network.
Probes that do not contain an SSID: The STA periodically broadcasts a Probe Request frame that does not contain an SSID in the supported channels as shown in Figure 2. The APs return Probe Response frames to notify the STA of the wireless services they can provide.
This method applies to the scenario where a STA actively scans wireless networks to determine whether wireless services are available.
Passive Scanning
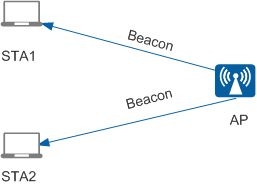
When passive scanning is enabled, a STA listens on the Beacon frames that an AP periodically sends in each channel to obtain AP information, as shown in Figure 3. A Beacon frame contains information including the SSID and supported rate.
To converse power, enable the STA to passively scan wireless networks. In most cases, VoIP terminals passively scan wireless networks.
Link Authentication
The link authentication stage is similar for Fit AP and agile distributed architectures. The only difference is that different objects authenticate STAs: APs in Fit AP architecture and RUs in agile distributed architecture.
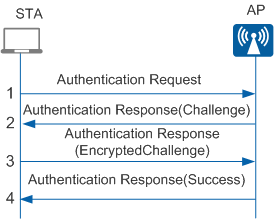
- Open system authentication requires no authentication. STAs that attempt to access the AP are successfully authenticated as long as the AP supports this mode. An illustration of the open system authentication procedure is shown in Figure 4.
- Shared key authentication requires that the STA and AP have the same shared key preconfigured. The AP checks whether the STA has the same shared key to determine whether the STA can be authenticated. If the STA has the same shared key as the AP, the STA is authenticated. Otherwise, STA authentication fails. Figure 5 shows the shared key authentication process.The shared key authentication process consists of the following steps:
- The STA sends an Authentication Request packet to the AP.
- The AP generates a challenge and sends it to the STA.
- The STA uses the preconfigured key to encrypt the challenge and sends it to the AP.
- The AP uses the preconfigured key to decrypt the encrypted challenge and compares the decrypted challenge with the challenge sent to the STA. If the two challenges are the same, the STA is authenticated. Otherwise, STA authentication fails.
Association
Client association is also known as link negotiation. After link authentication is complete, a STA initiates link negotiation using Association packets, as shown in Figure 6 in Fit AP architecture and Figure 7 and Figure 8 in agile distributed architecture.
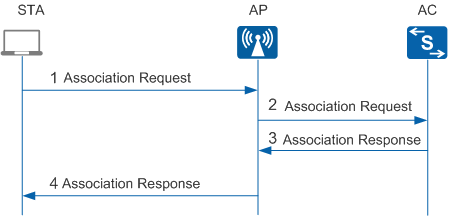
- STA association in Fit AP architecture consists of the following steps:
- The STA sends an Association Request packet to the AP. The Association Request packet carries the STA's parameters and the parameters that the STA selects according to the service configuration, including the transmission rate, channel, QoS capabilities, access authentication algorithm, and encryption algorithm.
- The AP receives the Association Request packet, encapsulates the packet into a CAPWAP packet, and sends the CAPWAP packet to the AC.
- The AC determines whether to associate with the STA according to the received Association Request packet and replies with an Association Response packet.
- The AP decapsulates the received Association Response packet and sends it to the STA.
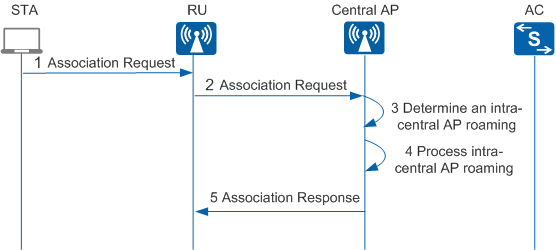
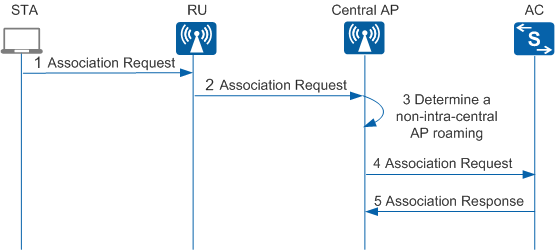
- STA association in agile distributed architecture consists of the following steps:
- The STA sends an Association Request packet to the RU. The Association Request packet carries the STA's parameters and the parameters that the STA selects according to the service configuration, including the transmission rate, channel, QoS capabilities, access authentication algorithm, and encryption algorithm.
- The RU receives the Association Request packet, encapsulates the packet into a CAPWAP packet, and sends the CAPWAP packet to the central AP.
- The central AP checks whether a local user entry matches.
- If so, intra-central AP roaming occurs. The central AP performs local roaming and sends an Association Response packet to the RU.
- If no, roaming is not intra-central AP roaming. The central AP forwards the Association Request packet to the AC. The AC then determines whether access authentication is required and sends an Association Response packet to the central AP.

- If the STA does not need to be authenticated, the STA can access the wireless network.
- If the STA needs to be authenticated, the STA initiates user access authentication. After authentication, the STA can access the wireless network. For details about user access authentication, see NAC Configuration in S2720, S5700, and S6700 V200R019C10 Configuration Guide - User Access and Authentication.