Terminal Type Identification
Bring Your Own Device (BYOD) has become a trend as the Internet develops fast. Many enterprises now allow employees to connect to enterprise networks wirelessly using their own mobile terminals, such as mobile phones, tablets, and laptops. This work style enables employees to use up-to-date technologies, gives them more flexibility in work, and improves their working efficiency. However, employees' own terminals may bring security risks to enterprise networks, and traditional security technology that authenticates and authorizes users based on user roles cannot secure enterprise networks in this scenario. Terminal type identification technology can solve this problem. This technology identifies types of mobile terminals that employees use to connect to an enterprise network to control access from the mobile terminals. Enterprises can use this technology to implement user authentication and authorization based on user information, device type, access time, access location, and device operating environment.
Terminal type identification requires the cooperation between the device and RADIUS server.
- If the RADIUS server does not support the terminal type identification function, you need to configure this function on the device. The device then sends identified terminal types to the RADIUS server, and the RADIUS server can deliver corresponding rights based on the terminal types.
For details, see Implementation of Terminal Type Identification.
- If the RADIUS server supports the terminal type identification function, you need to configure this function on the RADIUS server and configure the terminal type awareness function on the device. The device then sends identified terminal types to the RADIUS server, and the RADIUS server can deliver corresponding rights based on the terminal types.
For details, see Implementation of Terminal Type Awareness.
Implementation of Terminal Type Identification
- The device identifies the IP address, MAC address, reported service, TXT, and target of a terminal based on information in the mDNS packets sent by the terminal.
A terminal's organizationally unique identifier (OUI), the first 24 bits in its MAC address, identifies the manufacturer of the terminal.
The UA field in an HTTP packet sent from a terminal identifies the terminal's operating system, operating system version, CPU type, browser, and browser version.
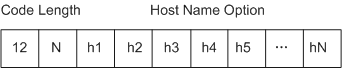
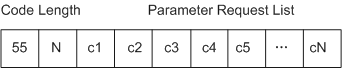
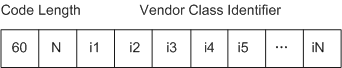
The Option 12, Option 55, and Option 60 field in DHCP packets sent from a terminal identifies the host name of the terminal, list of requested parameters, and manufacturer type, respectively.
- As shown in Figure 1, DHCP Option 12 is the Host Name Option. In this option field, 12 indicates the information type, N indicates the length of the following information, and h1 to hN indicate the information content (containing the host name of the STA).
- In Figure 2, DHCP Option 55 is the Parameter Request List. In this option field, 55 indicates the information type, N indicates the length of the following information, and c1 to cN indicate the information content (containing the list of parameters requested by a STA. Different STAs may request different parameters.)
- As shown in Figure 3, DHCP Option 60 is the Vendor Class Identifier. In this option field, 60 indicates the information type, N indicates the length of the following information, and i1 to iN indicate the information content (containing the manufacturer identifier).
The device can obtain the MAC address, DHCP option information, and UA information of a terminal during Portal authentication, MAC address authentication, and 802.1X authentication.
- After a user accesses the network, the device obtains the user MAC address.
- When a user sends a DHCP Request packet to apply for an IP address to an AP, the AP uses the DHCP snooping function to obtain the option information from the DHCP Request packet and sends the option information to the device.
- When the user sends an HTTP Get packet to obtain the authentication page, the device analyzes the HTTP Get packet and obtains the UA information from the packet.
- The device identifies the terminal type by analyzing the MAC address, UA information, and DHCP option information of the user.
- The device encapsulates the terminal type in an authentication request packet and sends the packet to the RADIUS server. The RADIUS server authenticates the user based on the user account and terminal type, and delivers corresponding access rights to the user.
- After a user accesses the network, the device obtains the user MAC address.
- The device identifies the terminal type according to the OUI in the MAC address. If the OUI is an identifiable one, the device encapsulates the terminal type in an authentication request packet and sends the packet to the RADIUS server.
- When a user sends a DHCP Request packet to apply for an IP address to an AP, the AP uses the DHCP snooping function to obtain the option information from the DHCP Request packet and sends the option information to the device.
- The device identifies the terminal type according to the MAC address and DHCP option information, encapsulates the terminal type in an accounting packet, and sends the accounting packet to the AAA server.
- When the user sends an HTTP Get packet to obtain the authentication page in the forcible web page push process, the device analyzes the HTTP Get packet and obtains UA information from the packet.
- The device identifies the terminal type according to the MAC address, UA information, and DHCP option information, encapsulates the terminal type in an accounting packet, and sends the accounting packet to the RADIUS server.

The terminal type identified by the device is carried by Huawei proprietary attribute 157 HW-Terminal-Type and sent to the RADIUS server. The RADIUS server configures this attribute so that it can deliver authorization information based on the user terminal type.
Implementation of Terminal Type Awareness
- UA mode: The device parses the UA field that carries terminal type information from the HTTP Get packets sent from terminals. The device then encapsulates the UA information into the Huawei proprietary attribute 159 HW-HTTP-UA in RADIUS accounting packets, and sends the packets to the RADIUS server.
- DHCP option field mode: The device parses the required option field containing terminal type information from the received DHCP Request packets. The device encapsulates the option field information into the Huawei proprietary attribute 158 HW-DHCP-Option in RADIUS accounting packets, and sends the packets to the RADIUS server.
- LLDP TLV type mode: The device parses the required TLV type containing terminal type information from the received LLDP packets. The device encapsulates the TLV type information into the Huawei proprietary attribute 163 HW-LLDP in RADIUS accounting packets, and sends the packets to the RADIUS server.
The device can obtain the UA, DHCP option, and LLDP TLV information of a terminal during Portal authentication, MAC address authentication, and 802.1X authentication.
- When a user sends a DHCP Request packet to apply for an IP address to an AP, the AP uses the DHCP snooping function to obtain the option information from the DHCP Request packet and sends the option information to the device.
- When a user sends an LLDP packet, the device obtains the TLV type information from the packet.
- When a user sends an HTTP Get packet to access the authentication page, the device obtains UA information from the packet.
- The device encapsulates the obtained DHCP option, UA, or LLDP TLV information in an accounting request and sends the accounting request to the RADIUS server. The RADIUS server then identifies the terminal type based on the account information and the DHCP option, UA, or LLDP TLV information, and delivers corresponding rights to the user.
- When a user sends a DHCP Request packet to apply for an IP address to an AP, the AP uses the DHCP snooping function to obtain the option information from the DHCP Request packet and sends the option information to the device.
- When a user sends an LLDP packet, the device obtains the TLV type information from the packet.
- When a user sends an HTTP Get packet to obtain the authentication page in the forcible web page push process, the device obtains UA information from the packet.
- The device encapsulates the obtained DHCP option, UA, or LLDP TLV information in an accounting request and sends the accounting request to the RADIUS server. The RADIUS server then identifies the terminal type based on the account information and the DHCP option, UA, or LLDP TLV information, and delivers corresponding rights to the user.