Defense Against Packet Fragment Attacks
If an attacker sends error packet fragments to a network device, the device may consume a large number of CPU resources, restart, or even break down. Defense against packet fragment attacks allows the device to detect packet fragments in real time and discard them or limit the rate of the packets to protect the device.
Attacks of packet fragments are classified into the following types.
Excess-Fragment Attacks
The offset of IP packets is calculated on the basis of 8 bytes. Normally, an IP header has 20 bytes and the maximum payload of an IP packet is 65515 bytes. An IP packet can be fragmented into up to 8189 fragments. The device will consume many CPU resources to reassemble packets with over 8189 fragments.
After defense against packet fragment attacks is enabled, the device considers a packet with over 8189 fragments malicious and discards all fragments of the packet.
Excess-Offset Attacks
An attacker sends a fragment with a large offset value to a target host. Then, the target host allocates memory space to store all fragments, consuming a large number of resources.
The maximum value of the offset is 65528. Generally, the offset value does not exceed 8190. If the offset value is 8189 multiplied by 8 and the IP header is 20, the last fragment can have only a 3-byte IP payload. In normal situations, the maximum value of the offset is 8189. The device considers packets with an offset value larger than 8190 malicious and discards them.
After defense against packet fragment attacks is enabled, the device checks whether the offset value multiplied by 8 is greater than 65528. If the offset value multiplied by 8 is greater than 65528, the device considers the fragments malicious and discards them.
Repeated Packet Fragment Attacks
An attacker sends repeated fragments to a target host multiple times. There are two situations:
The attacker sends the same fragments to a target host multiple times, causing a high CPU usage or memory error on the target host.
The attacker sends different fragments with the same offset to a target host. The target host cannot determine which fragment is reserved, which fragment is to be discarded, and whether all fragments need to be discarded. As a result, a high CPU usage or memory error may occur on the target host.
After defense against packet fragment attacks is enabled, the device applies the committed access rate (CAR) limit to packet fragments, reserves the first fragment, and discards all the remaining repeated fragments to protect the CPU.
Tear Drop Attack
The Tear Drop attack is the frequently used IP packet fragment attack. IP packets are incorrectly fragmented and the second fragment is contained in the first one. The offset of the second fragment is smaller than that of the first fragment, and the offset plus the Data field of the second fragment does not exceed the tail of the first fragment.
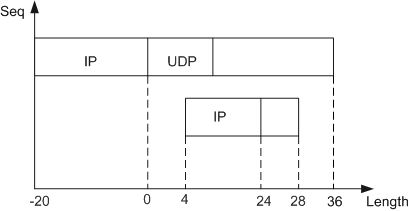
As shown in Figure 1:
The IP payload in the first fragment is 36 bytes, the total length of the IP packet is 56 bytes, the protocol is UDP, and the UDP checksum is 0 (that is, unchecked).
The IP payload in the second fragment is 4 bytes, the total length of the IP packet is 24 bytes, the protocol is UDP, and the offset is 24 (this is incorrectly calculated and the correct offset should be 36).
Tear Drop attacks cause system breakdown or restart. After defense against packet fragment attacks is enabled, the device discards all the fragments in a Tear Drop attack.
Syndrop Attack
A Syndrop attack is similar to a Tear Drop attack except that Syndrop attacks use TCP packets with a SYN flag and IP payload.
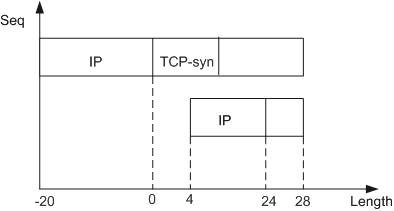
As shown in Figure 2:
The IP payload in the first fragment is 28 bytes, and the IP header is 20 bytes.
The IP payload in the second fragment is 4 bytes, the IP header is 20 bytes, and the offset is 24 (this is incorrectly calculated and the correct offset should be 28).
Syndrop attacks cause system breakdown or restart. After defense against packet fragment attacks is enabled, the device discards all fragments of Syndrop attacks.
NewTear Attack
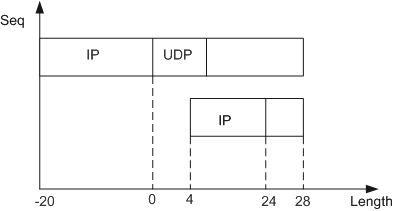
The IP payload of the first fragment is 28 bytes including the UDP header. The UDP checksum is 0.
The IP payload of the second fragment is 4 bytes. The offset is 24, which is incorrectly calculated. The correct offset should be 28.
NewTear attacks cause system breakdown or restart. After defense against packet fragment attacks is enabled, the device discards all fragments of NewTear attacks.
Bonk Attack
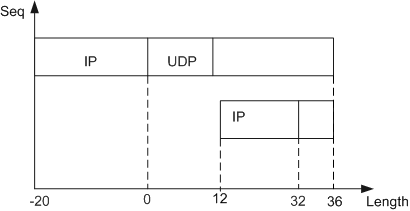
The IP payload of the first fragment is 36 bytes including the UDP header. The UDP checksum is 0.
The IP payload of the second fragment is 4 bytes. The offset is 32, which is incorrectly calculated. The correct offset should be 36.
Bonk attacks cause system breakdown or restart. After defense against packet fragment attacks is enabled, the device discards all fragments in a Bonk attack.
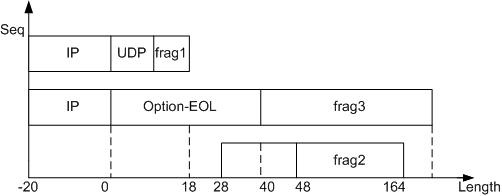
Nesta Attack
The IP payload in the first fragment is 18 bytes, the protocol used is UDP, and the checksum is 0.
The offset in the second fragment is 48 and the IP payload is 116 bytes.
The offset in the third fragment is 0, the more frag is 1 (that is, there are more fragments), the IP option (all EOLs) is 40 bytes, and the IP payload is 224 bytes.
Nesta attacks cause system breakdown or restart. After defense against packet fragment attacks is enabled, the device discards all fragments of Nesta attacks.
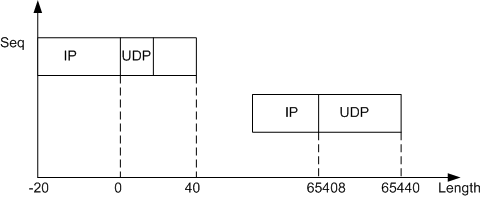
Rose Attack
A Rose attack may utilize protocols such as UDP and TCP.
As shown in Figure 6:
If Rose attacks use TCP:
The IP payload in the first fragment is 48 bytes (including the TCP header) and the length of the IP header is 20 bytes.
The IP payload in the second fragment is 32 bytes, the offset is 65408, and the more frag is 0 (last fragment).
If Rose attacks use UDP:
The IP payload in the first fragment is 40 bytes (including the UDP header, with UDP checksum 0), and the IP header is 20 bytes.
The IP payload in the second fragment is 32 bytes, the offset is 65408, and the more frag is 0 (last fragment).
Rose attacks cause system breakdown or restart. After defense against packet fragment attacks is enabled, the device discards all fragments in a Rose attack.
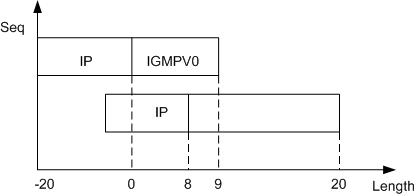
Fawx Attack
Fawx attack uses error fragments of IGMP packets. As shown in Figure 7, two fragments of an IGMP packet are sent. In the first fragment, the IP payload is 9 bytes. In the second fragment, the offset is 8, and the IP payload is 16 bytes.
Fawx attacks cause system breakdown or restart. After defense against packet fragment attacks is enabled, the device discards all fragments in a Fawx attack.
Ping of Death Attack
An attacker sends ICMP packets with the Data field longer than 65507 bytes to attack a device. If the device processes ICMP packets that have more than 65507 bytes in the Data field, the protocol stack may crash.
After defense against packet fragment attacks is enabled, the device discards ICMP packets that have more than 65507 bytes in the Data field.
Jolt Attack
An attacker sends packets longer than 65535 bytes to attack a device. Jolt attack uses 173 packet fragments. The IP payload of each packet fragment is 380 bytes. The total length is 65760 (173 x 380 + 20) bytes, which is greater than 65535. If the device processes such packets, the device may stop responding, crash, or restart.
After defense against packet fragment attacks is enabled, the device discards Jolt attack packets.