IS-IS Auto FRR
With the development of networks, the Voice over IP (VoIP) and on-line video services require high-quality real-time transmission. Nevertheless, if an IS-IS fault occurs, multiple processes, including fault detection, LSP update, LSP flooding, route calculation, and FIB entry delivery, must be performed to switch traffic to a new link. This results in a lengthy traffic interruption, which cannot meet the requirement for real-time services.
Complying with RFC 5286 (Basic Specification for IP Fast Reroute Loop-Free Alternates), IS-IS Auto FRR protects traffic when links or nodes become faulty. IS-IS Auto FRR allows the forwarding system to rapidly detect such faults and take measures to restore services as soon as possible.
In most cases, you can bind BFD to IS-IS Auto FRR to ensure millisecond-level fault recovery. When BFD detects a link fault on an interface, the BFD session goes Down, triggering FRR on the interface. Subsequently, traffic is switched from the faulty link to the backup link, which protects services.
Principles
IS-IS Auto FRR pre-computes a backup link by using the Loop-Free Alternate (LFA) algorithm, and then adds the backup link and the primary link to the forwarding table. In the case of an IS-IS network failure, IS-IS Auto FRR can fast switch traffic to the backup link before routes on the control plane converge. This ensures normal transmission of traffic and improves the reliability of the IS-IS network.
The backup link is calculated through the LFA algorithm. With the neighbor that can provide the backup link being the root, the shortest path to the destination node is calculated by a device through the SPF algorithm. Then, the loop-free backup link is calculated according to the inequality defined in RFC 5286.
IS-IS Auto FRR can filter backup routes that need to be added to the IP routing table. Only the backup routes matching the filtering policy are added to the IP routing table. In this manner, users can flexibly control the addition of IS-IS backup routes to the IP routing table.
Applications
IS-IS Auto FRR support traffic engineering (TE) links, including the following types:
IP protecting TE
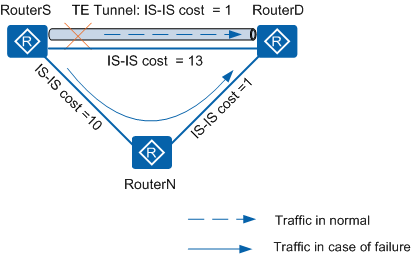
As shown in Figure 1, the TE tunnel has the smallest IS-IS cost among the paths from RouterS to RouterD. Therefore, RouterS selects the TE tunnel as the primary path to RouterD. The path RouterS->RouterN->RouterD has the second smallest cost. According to the LFA algorithm, RouterS selects the path RouterS->RouterN->RouterD as the backup path. The outbound interface of the backup path is the interface that connects RouterS to RouterN.

If the outbound interface of the backup link is the actual outbound interface of the TE tunnel, IP protecting TE fails.
TE protecting IP
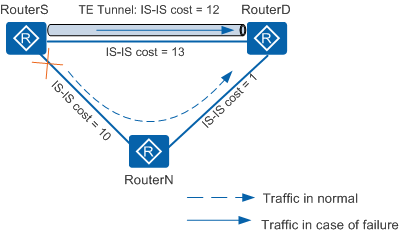
As shown in Figure 2, the physical path RouterS-->RouterN-->RouterD has the smallest IS-IS metric among the paths from RouterS to RouterD. Therefore, RouterS prefers the path RouterS-->RouterN-->RouterD as the primary path from RouterS to RouterD. The IS-IS cost of the TE tunnel is 12, and the explicit path of the TE tunnel is the direct link from RouterS to RouterD. The IS-IS metric of the direct link from RouterS to RouterD is 13, which is greater than the IS-IS metric of the TE tunnel. Therefore, IS-IS selects the TE tunnel as the backup path. TE protecting IP is implemented.
IS-IS Auto FRR traffic protection is classified into link protection and link-node dual protection.
| Traffic Protection Type | Object Protected | Condition | Application Example |
|---|---|---|---|
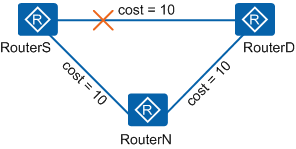
| Link protection | Traffic passing through a specific link | The link cost must satisfy the following inequality: Distance_opt(N,D) < Distance_opt(N,S) + Distance_opt(S,D) |
In Figure 3, traffic is transmitted from RouterS to RouterD. The link cost satisfies the link protection inequality. When the primary link fails, RouterS switches the traffic to the backup link RouterS->RouterN so that the traffic can be further transmitted along downstream paths. This ensures that the traffic interruption time is within 50 ms. |
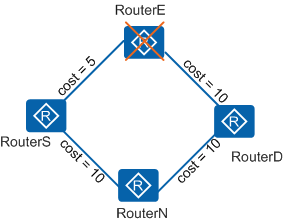
| Link-node dual protection | Next-hop node or link from the local node to the next-hop node. Node protection takes precedence over link protection. | Link-node dual protection must satisfy the following conditions:
|
In Figure 4, traffic is transmitted along the path RouterS->RouterE->RouterD. The link cost satisfies the link protection inequality. When RouterE or the link between RouterS and RouterE fails, RouterS switches the traffic to the backup link RouterS->RouterN so that the traffic can be further transmitted along downstream paths. This ensures that the traffic interruption time is within 50 ms. |

In Table 1, Distance_opt(X,Y) indicates the cost of the optimal path between node X and node Y. S indicates the source node of traffic; E indicates the faulty node; N indicates the node on the backup link; D indicates the destination node of traffic.